A Chinese mobile app promotion company has created malicious adware that allows them to gain complete control of users’ Android devices. The company misuses this access to make the phones download additional apps and to show ads. Naturally, they get paid for installing these apps and promoting a variety of services.
As their adware is roping more and more of devices around the world into a makeshift botnet, the additional bad news is that all communications within the botnet are unencrypted, so anyone can effectively hijack the connection and take control of the botnet.
“The malicious adware uses novel techniques to maintain persistence and obfuscate its activity, including installing system level services, modifying the recovery script executed on boot, and even tricking the user into enabling automatic app installation,” FireEye researchers have discovered.
“We have observed over 300 malicious, illegitimate versions of Android apps being distributed, including: Amazon, Memory Booster, Clean Master, PopBird, YTD Video Downloader, and Flashlight.”
The attackers repackage popular apps and inject malicious logic and ad components into them, then push them onto user via different channels (a giant ad cooperative network, posts on social networks, etc.).
Once on a victim’s phone, the malware unpacks and releases the malicious payload along with the normal components of the repackaged app. The victim gets the app he or she wanted to download in the first place, and there’s nothing to incite suspicion about the download’s true nature.
The entire process of infiltrating the device, achieving persistence on it, and delivering promoted adds and apps to it looks like this:
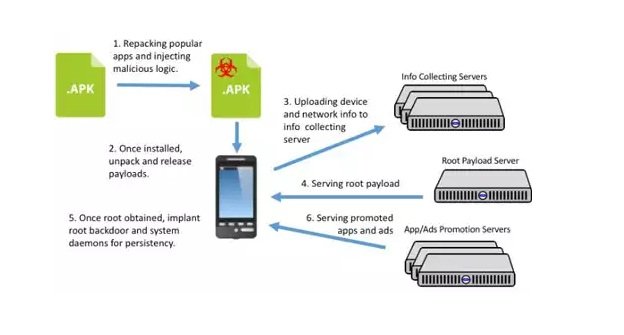
The researchers are pretty sure that the company – NGE Mobi/Xinyinhe – is behind this scheme, as several clues regarding the certificates, root exploit and subdomains used in the scheme point to the company.
The malicious adware has infected devices all over the world, and found its way onto 20 different versions of Android, from version 2.3.4 to 5.1.1 (the latest).
The researchers offered the usual good advice about keeping your device as safe as possible from this and other malware: don’t click on suspicious links and download files form untrusted sources, don’t install apps outside the official app store, and regularly update your device.
Source:https://www.net-security.org/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











