The Microsoft Enhanced Mitigation Experience Toolkit, short EMET, is an optional download for all supported client and server versions of Microsoft’s Windows operating system that adds exploit mitigation to the system’s defenses.
Basically, it has been designed to prevent attacks from being carried out successfully if they have breached system defenses such as antivirus solutions already.
EMET is easy to install and runs out of the box, but to get the most out of the program, you need to spend time getting to know it and configuring it.
This article provides you with tips on how to make the most out of EMET.
1. Protecting important processes
EMET protects core Microsoft and a handful of third-party processes only after installation. While that takes care of programs like Java, Adobe Acrobat, Internet Explorer or Excel, it won’t protect programs that you have installed manually such as Firefox, Skype or Chrome.
While it is theoretically possible to add all your programs to EMET, you may want to consider adding only high-risk programs to the application instead.
High-risk programs? A short definition of a high-risk program is that it is either exploited regularly (e.g. Internet Explorer), capable of executing files downloaded from the Internet (web browser, email client), or stores valuable data for you (e.g. encryption software).
This would make Firefox, Chrome and Thunderbird high-value targets and Notepad, Minesweeper and Paint not.
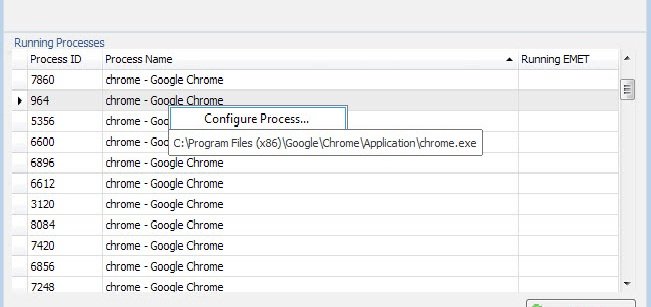
To add applications to EMET’s protection list
- Open EMET on the system.
- You find a list of running processes in the interface. If the program that you want to protect is not running, start it on the PC.
- Right-click on its process afterwards and select “configure process” from the context menu.
- This adds the selected process to EMET’s application list.
- Select okay afterwards to save the selection and restart the program you have just added to EMET.
Tip: It is highly suggested to test each application individually before you start to add more processes to EMET. A program may not be compatible with all exploit mitigation techniques that EMET offers.
2. Debugging misbehaving processes
The chance is rather high that you will encounter issues after adding programs to EMET. Some programs may refuse to start entirely while others may open and close immediately after they have been started.
This is usually the case when one or multiple mitigations are not compatible with the process. The main issue here is that you won’t receive information which mitigation caused the problem.
Verify that there is a problem
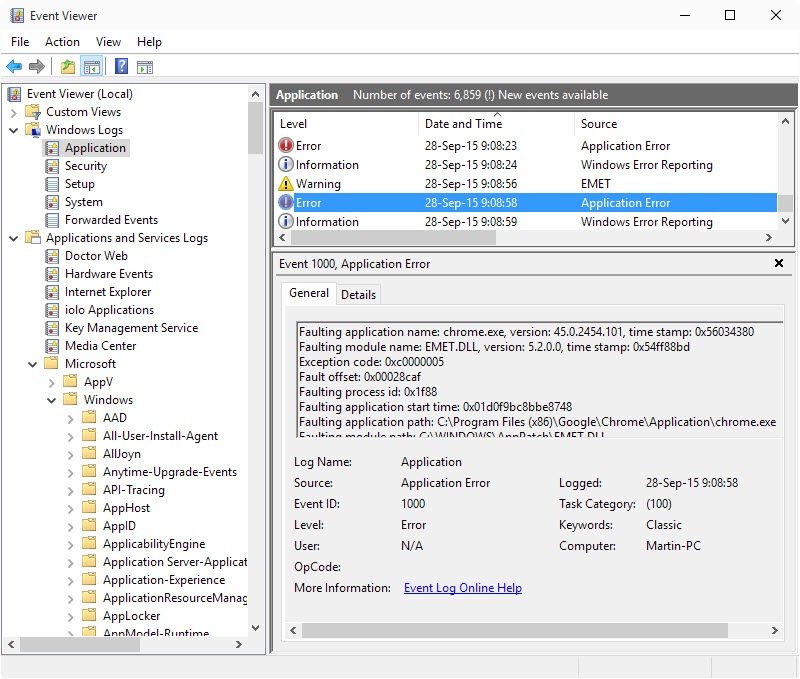
One of the easier ways to verify that something is not working right is to check for EMET entries in the Windows Event log.
- Tap on the Windows-key, type event viewer and hit enter.
- You find EMET entries under Event Viewer (local) > Windows Logs > Application.
I suggest you sort by Date and Time, and look for “Application Error” as the source. You should find EMET.DLL listed as the source of the issue under General when you select one of the log entries.
Obviously, you could also remove all protections for the application in EMET and run it again to see if it resolves the issue.
Correcting the issue
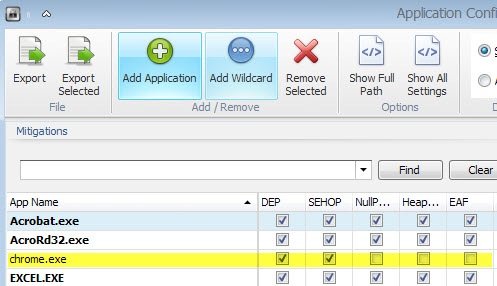
The only surefire way of enforcing compatibility with Microsoft EMET is trial and error. Open the protected applications listing again in EMET, turn off all protections, and start turning them on again one by one.
Try to run the program after each switch to see if it works. If it does, repeat the process by switching on the next mitigation in line until you come to one that prevents the program from starting up.
Disable that mitigation again and continue the process until you have enabled all mitigations that are compatible with the selected software.
Google Chrome for instance failed to start using the default mitigations selected for new processes. I discovered that the only mitigation the browser was not compatible with was EAF which I disabled as a consequence.
3. System-wide rules
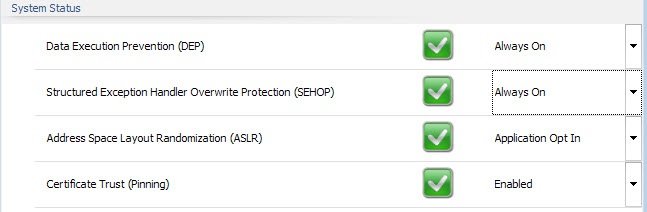
EMET ships with four system-wide rules that you can configure in the main interface. Certificate Pinning, Data Execution Prevention and Structured Exception Handler Overwrite Protection are enabled as system-wide rules while Address Space Layout Randomization is set to opt-in instead.
This means that you need to enable the rule for each application you want protected by it. You may change the status of these system wide rules, for instance by enforcing the opt-in rule system-wide as well.
This may however cause issues with programs running on the system. Since it is enforced for all programs when enabled, you may want to monitor the system closely and switch back to opt-in if you notice issues starting or running applications on the machine.
4. Rule importing and exporting
Configuring programs in EMET so that they are protected by the application takes a while because of the issues outlined above.
Good news is that you don’t need to repeat the process on other PCs that you manage as you can use EMET’s import and export feature for that.
Tip: EMET ships with a set of extra rules that users can add to the program. To access those select import in EMET and then one of the following:
- CertTrust – EMET default config of Certificate Trust Pinning for MS and 3rd party online services
- Popular Software – Enables protections for common software such as Internet Explorer, Microsoft Office, Windows Media Player, Adobe Acrobat Reader, Java, WinZip, VLC, RealPlayer, QuickTime, Opera
- Recommended Software – Enables protections for minimal recommended software such as Internet Explorer, Microsof Office, Adobe Acrobat Reader and Java
Option 3 is the default option that gets loaded automatically. You can add other popular programs to EMET automatically by importing the Popular Software rules.
Rule migration and policies
To export rules select the export button in EMET’s main interface. Pick a name for the xml file in the save dialog and a location.
This set of rules can then be imported on other systems, or kept as a safeguard on the current machine.
Since rules are saved as XML files, you may edit them manually as well.
Administrators can deploy Group Policy directives on systems as well. The adml/admx files are part of the EMET installation and can be found under Deployment/Group Policy Files after installation.
Source:https://www.ghacks.net/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.