Security vendor interrupts hacking campaign targeting Israeli security firms, government agencies, and hospitals.Security experts have identified and isolated a series of attacks that were targeting the Israeli public sector. In this particular case, the hackers were using the MWI (Microsoft Word Intruder) exploit kit to deliver a modified version of the Zeus info-stealing trojan on infected PCs.
The discovery was made by Check Point security researchers after one of its high-profile clients submitted a suspicious RTF file for an in-depth analysis.
Apparently, the file in question arrived in the organization via spam email sent to multiple staff members, a few of which took the careless steps of downloading and opening the file.
RTF documents infected with the Microsoft Word Intruder kit
After Check Point’s analysis, the file was found to be infected with the MWI exploit kit, a well-known package which specifically targets Word files on Windows PCs.
The exploit kit is quite complex, leveraging multiple known vulnerabilities, to deliver other more dangerous payloads on the infected user’s PC. In this case, it was a slightly modified off-the-shelf variant of the Zeus trojan.
The Zeus trojan is a cyber-weapon developed to specifically target the corporate environment, and can steal browser passwords, banking credentials, and various other authentication details from its victims.
The C&C server was used to host multiple campaigns targeting Israeli agencies
The researchers were also able to track down the MWI kit’s C&C server to a German IP address, and with the help of its ISP, investigate the server’s content and logs.
Findings reveal that the server was used to manage and track several MWI-based campaigns, each in different stages of infections, and using different payloads, not just the Zeus trojan.
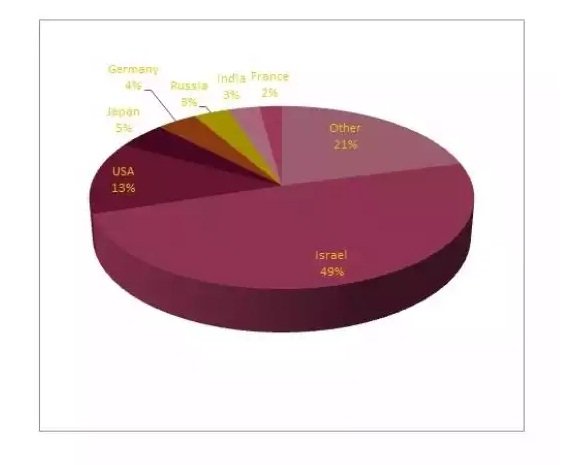
Analyzing the targeted IP addresses, researchers were also able to discover that over 49% of machines were from Israel.
While Check Point researchers say that “there are many reasons campaigns can end up with a lopsided geographical distribution of infection victims; that, alone, does not necessarily imply a ‘targeted campaign’ scenario.” This was not the case.
Analyzing each of the Israeli IP addresses, researchers were able to discover that over 200 PCs in 15 different Israeli locations were targeted, belonging to various government agencies, hospitals, research agencies, and security firms.
This clearly was not just an accident, and the attackers were looking for specific information during this campaign.
Source:softpedia.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











