A banking trojan, detected by ESET as Win32/Brolux.A, is targeting Japanese internet banking users and spreading through at least two vulnerabilities: a Flash vulnerability leaked in the Hacking Team hack and the so-called unicorn bug, a vulnerability in Internet Explorer discovered in late 2014. Both exploits are (still) distributed through an adult website and try to install a signed malicious binary designed to steal personal information from the victim. The spreading mechanism reminds us of another banking trojan specifically targeting Japanese financial institutions,Win32/Aibatook.
Infection
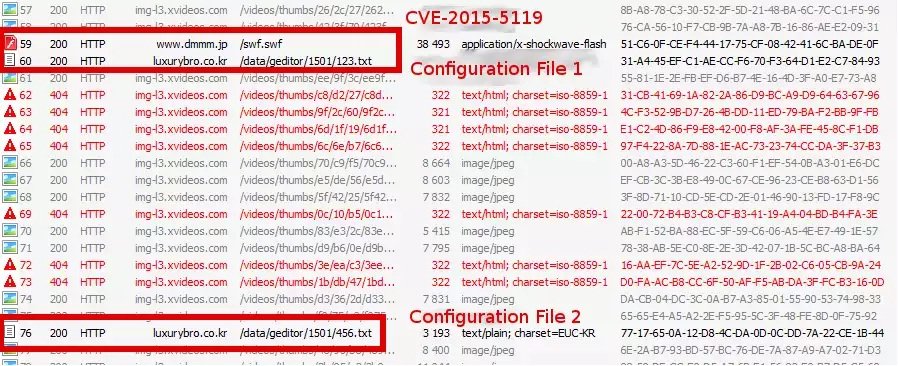
When a user visits the malicious adult website, he is exposed to an exploit targeting either Internet Explorer (CVE-2014-6332) or Flash Player (CVE-2015-5119). The cybercriminals are thus using two widely known, weaponized vulnerabilities. This is yet another reminder that software we routinely used should always be kept up-to-date and patched. A proof-of-concept code for the vulnerability affecting Internet Explorer has been available for quite some time; this campaign is reusing a slightly modified version of it.
As for the Flash vulnerability, a working exploit was released publicly earlier this year during the analysis of the Hacking Team leak. Although these vulnerabilities have already been included in major exploit kits, we do not believe that any known exploit kit is used in this campaign. The exploit itself was easy to analyze as no additional obfuscation layer was added, as is customary with exploits used in popular exploit kits. As can be seen in the screenshot below, it appears the adult website attempting to compromise users is in fact just scraping videos from another, legitimate, adult website.
Target
The main payload will download two configuration files. The first one contains a list of 88 Japanese internet banking URLs that are monitored by the trojan, while the second contains the accompanying browser window names. Win32/Brolux.A is a simple trojan monitoring whether the user is visiting one of the targeted Japanese internet banking websites. It supports Internet Explorer, Firefox and Chrome browsers. If the user is browsing the web with IE, Win32/Brolux.A will fetch the current URL in the address bar and then compare it to the list in the first configuration file. If Firefox or Chrome is used, it will instead compare the window’s title with the list obtained in the second configuration file. If there is a match, it will spawn a new IE process, pointing to a phishing page.
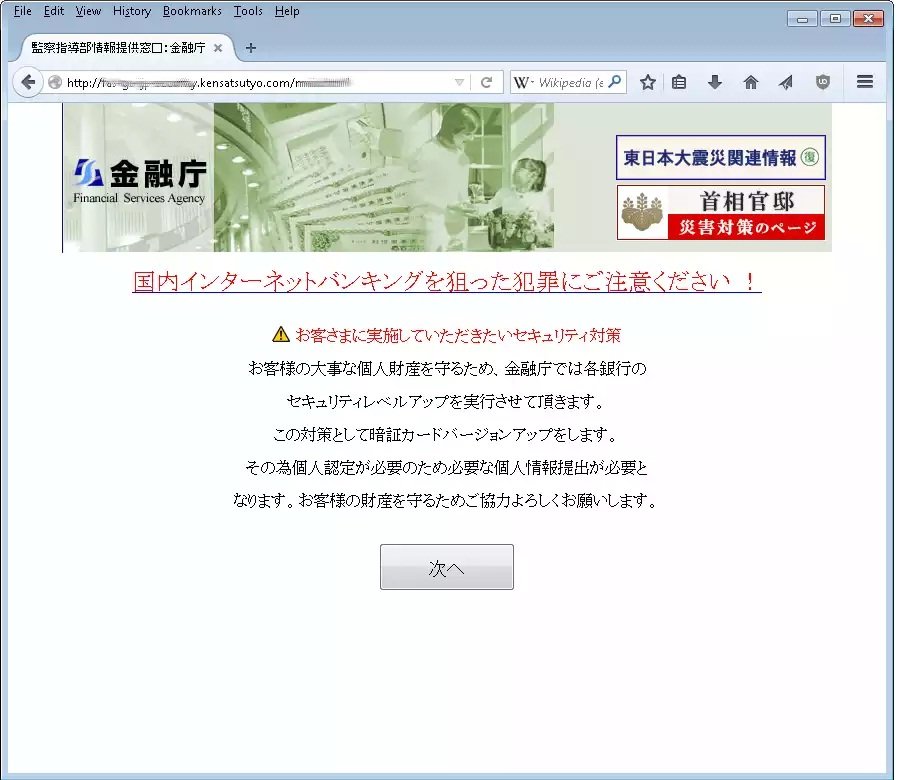
The phishing page asks for login information, as well as answers to security questions. The page tries to use two trusted institutions in Japan: the Public Prosecutors Office and the Financial Services Agency (FSA). The URL mimics both institutions while the page’s content refer to the FSA.
Rough translation:
- Please pay attention to crimes aimed at domestic internet banking!
- Security measures that customers should implement:
- In order to protect the important personal property of customers, Financial Services Agency will make each bank enhance its security.
Each bank will be required to provide customers with an updated card, and to submit information necessary to identify the customer uniquely.
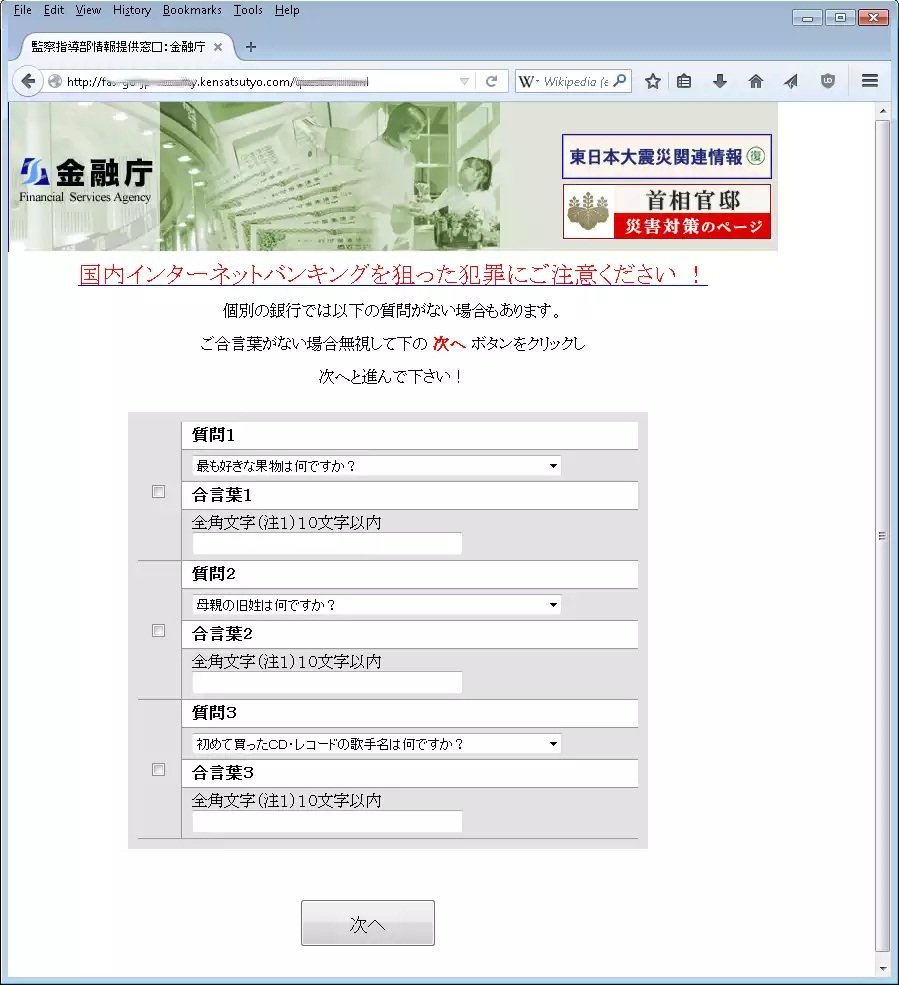
Rough translation:
- Please pay attention to crimes aimed at domestic internet banking!
- For each bank, there are some cases where answers to the questions below are not required.
- In case there is no passphrase, please ignore and click ‘Next’ button to move to the next field!
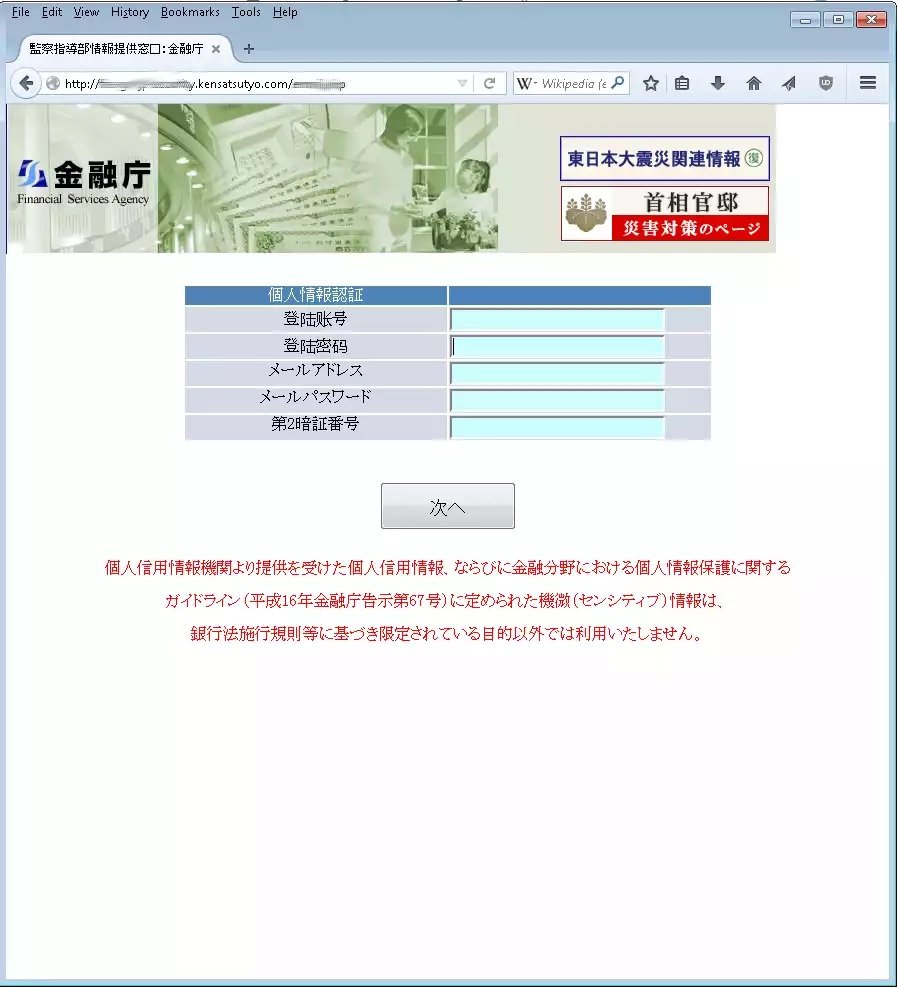
Rough translation:
- Personal information:
- Registration number
- Passphrases
- Mail address
- Mail password
- The second PIN
- We will not use personal credit data offered from Consumer Data Industry or sensitive information, which is defined by guideline for personal information protection, 2004 Financial Services Agency Notification No. 67, for purposes other than the original intent, which is limited by Ordinance for Enforcement of the Banking Act.
Interestingly, both the Public Prosecutors Office and the FSA issued statements about this kind of abuse.
The Chinese connection
The sample of Win32/Brolux.A we analyzed uses a Chinese mutex name. Also, the phishing page contained errors and was not entirely written in Japanese: two fields in the third phishing page shown above are written in Chinese.
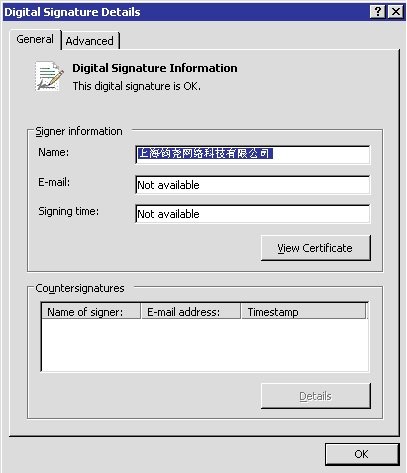
Finally, the analyzed Win32/Brolux.A sample was signed with the following certificate:
Interestingly, this certificate, awarded to a Chinese company, has been used in the past to sign different Potentially Unwanted Applications and malware samples. Analyzing the different samples, some of them stand out. We found samples of Venik malware targeting Korean banks. This malware changes the host file on the victim’s computer to redirect requests for targeted Korean internet banking website to a phishing page. Incidentally, this modus operandi is quite similar to Win32/Brolux’s.
While Win32/Brolux uses simple techniques, it is a reminder for us all to take some precautionary measures to prevent threats like these from causing harm. First of all, Win32/Brolux is using old exploits to spread, so keeping the software running on your computer up-to-date and patched is a must. Then, being suspicious when your internet banking websites suddenly contain new content is a good safeguard against this type of attack.
| Indicator | Value |
|---|---|
| Certificate thumbprint | 88 ca 78 5c e6 ef 05 ac e6 de 58 46 86 86 29 cc d0 1b cd 40 |
| Win32/Brolux.A SHA1 | 0010d0ae9c56e222c9e90d3ef7dd9a215ca1780d |
| Flash Exploit SHA1 | a646997f716f7af7a734a5148827431d6233101e |
| Venik SHA1 (signed by same certificate) | 41188c1c88f24879745ae4649e0af37f9a47d20c |
| Venik SHA1 (signed by same certificate) | 73F1B8D4650AEC0F60C6C243B8AC68805830460E |
| Malicious domain | dmmm.jp |
| Phishing page | fas-go-jp-security.kensatsutyo.com |
| Domain hosting configuration files | luxurybro.co.kr |
Source:https://www.welivesecurity.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.