Security researcher Axelle Apvrille has managed to deliver malware to a FitBit Flex fitness tracker, and to spread the infection to any computer that the device is subsequently connected to.
She took advantage of a vulnerability that she discovered back in March and pointed out to the manufacturer, but has yet to be patched: the wearable device has its Bluetooth port open.
This allows attackers that can get close enough to the target device to deliver an infected packet to it in less than 10 seconds. According to Apvrille, the rest of the attack occurs by itself, and the attacker doesn’t have to be near for that.
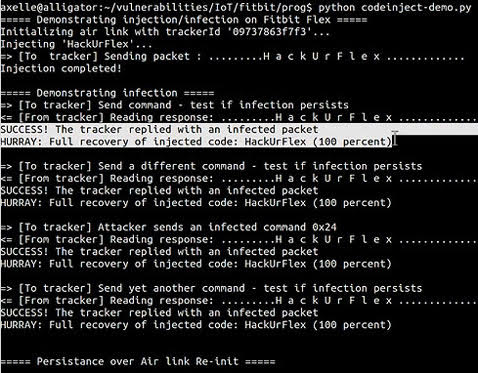
“[When] the victim wishes to synchronize his or her fitness data with FitBit servers to update their profile … the fitness tracker responds to the query, but in addition to the standard message, the response is tainted with the infected code,” she told The Register.
“From there, it can deliver a specific malicious payload on the laptop, that is, start a backdoor, or have the machine crash [and] can propagate the infection to other trackers (Fitbits).”
She also discovered ways to manipulate the information received by the device, mimicking motion where there is none.
By reverse-engineering the messages the device and its USB Bluetooth dongle send to each other, she managed to discover in part how these devices work, which can definitely be helpful as this is proprietary technology and details about it are not shared with the public or the research community.
Apvrille, who is a senior anti-virus researcher for Fortinet, presented her research on Wednesday at the Hack.lu conference in Luxembourg.
“The Internet of Things and proliferation of wireless devices is creating opportunities for threat actors to employ new attack strategies. Fortinet’s threat researchers proactively work to discover new vulnerabilities and properly communicate findings so necessary actions can be taken,” the company commented.
“As in all instances, our researchers follow responsible disclosure policies and in this case, Fitbit was notified of the vulnerability in March. Our security threat researcher demonstrated to Fitbit a vulnerability that enabled her to inoculate a Fitbit device with arbitrary code that could be sent to computers that the device connects to over a Bluetooth connection. To responsibly ensure that these vulnerabilities could not be exploited more broadly by other malicious actors, Fortinet and our researchers refrained from publishing key details about specific Fitbit devices and the methodologies employed to exploit these devices.”
UPDATE (23th October):
FitBit sent in the following statement:
“On Wednesday October 21, 2015, reports began circulating in the media based on claims from security vendor, Fortinet, that Fitbit devices could be used to distribute malware. These reports are false.
“In fact, the Fortinet researcher, Axelle Apvrille who originally made these claims has confirmed to Fitbit that this was only a theoretical scenario and is not possible. Fitbit trackers cannot be used to infect user’s devices with malware. We want to reassure our users that it remains safe to use their Fitbit devices and no action is required.
“As background, Fortinet first contacted us in March to report a low-severity issue unrelated to malicious software. Since that time we’ve maintained an open channel of communication with Fortinet. We have not seen any data to indicate that it is possible to use a tracker to distribute malware.
“We have a history of working closely with the security research community and always welcome their thoughts and feedback. The trust of our customers is paramount. We carefully design security measures for new products, monitor for new threats, and rapidly respond to identified issues. We encourage individuals to report any security concerns with Fitbit’s products or online services to security@fitbit.com. More information about reporting security issues can be found online at https://www.fitbit.com/security/.
Apvrille has also clarified though her Twitter account that she didn’t deliver malware on the FitBit device, but arbitrary code. “To complete the scenario you’d need to execute the malicious code on the victim’s host,” she noted, and for that one would need an exploit for the sync host.
“However the scenario where a small virus propagates is – I believe – possible but not yet demoed,” she concluded.
Source: net-security.org

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











