Distributed via Word files and the Angler EK. Cyber-crooks are diversifying their activities by including as many threats as possible inside their malware-delivery campaigns. One such example is a campaign detected by Proofpoint, which saw a new type of PoS (Point of Sale) malware bundled with the Vawtrack banking trojan.
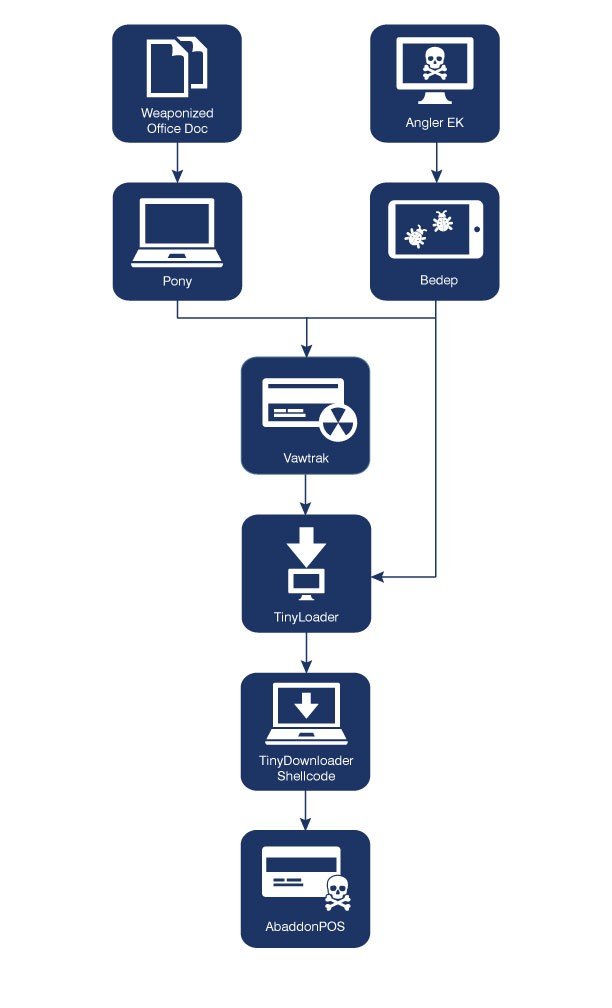
This new PoS malware was named AbaddonPOS and is part of a complex malware delivery infrastructure that also includes the Vawtrack banking trojan, the Angler exploit kit, the Bedep ad fraud malware, the Pony infostealer, and the TinyLoader payload downloader.
Weaponized Word docs and the Angler exploit kit
Infection usually occurs via Microsoft Word documents, known to be a favorite medium of transmitting malware among cyber-criminals, which at first deliver the Pony infostealer.
A second method of infection relies on users accessing malicious websites where a version of the Angler exploit kit gets them infected with the Bedep malware.
These two (Pony, Bedep), besides doing their own damage, also establish connections to C&C server and then fetch the TinyLoader payload downloader. This particular malware strand is specifically designed to do one thing and one thing only: download other malware from C&C servers using its own, custom protocol, hence its extremely small size of only 5Kb.
The malware TinyLoader downloads is AbaddonPOS. Researchers had some troubles detecting it, since it was a new family, never seen before.
Similarities between AbaddonPOS and TinyLoader
After carefully looking at its code, Proofpoint researchers found that the malware behaves like any other typical PoS malware specialized in stealing credit and debit card transaction data, and also trying to evade detection via various anti-analysis tricks.
It was actually when analyzing this latter part of the PoS malware’s code that researchers noted quite a lot of similarities between AbaddonPOS and TinyLoader.
Because the two used the same anti-analysis and obfuscation techniques, Proofpoint says that there’s a high chance that the authors of the two malware families are the same.
“The practice of threat actors to increase their target surfaces by leveraging a single campaign to deliver multiple payloads is by now a well-established practice,” said the Proofpoint security researchers.
“While using this technique to deliver point of sale malware is less common, the approach of the US holiday shopping season gives cybercriminals ample reason to maximize the return on their campaigns by distributing a new, powerful PoS malware that can capture the credit and debit card transactions of holiday shoppers.”
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











