Experts at FireEye have discovered a stealthy botnet relying on a backdoor called LATENTBOT has compromised companies around.
Experts at FireEye have discovered a stealthy botnet relying on a backdoor called LATENTBOT has compromised companies around. According to FireEye the LATENTBOT remained undetected since 2013 infecting computers in US, UK, South Korea, Brazil, United Arab Emirates, Singapore, Canada, Peru and Poland in 2015.
“FireEye Labs recently uncovered LATENTBOT, a new, highly obfuscated BOT that has been in the wild since mid-2013. It has managed to leave hardly any traces on the Internet, is capable of watching its victims without ever being noticed, and can even corrupt a hard disk, thus making a PCuseless.” states the report published by FireEye.
The experts observed multiple campaigns targeting multiple industries, but the threat actors appear to be focused on the financial services and insurance sectors.
FireEye has uncovered similar samples in the wild across the time, using passive DNS information its experts dated the bot around mid-2013.
Giving a detailed look to the LATENTBOT botnet, the experts discovered that it implements a 6-stage obfuscation process, operates completely in memory (LATENTBOT will only keep its code in memory for the short time that is needed to infect the target), and implements a single exfiltration mechanism.
Below the list of features implemented by the LATENTBOT beckdoor.
a) Multiple layers of obfuscation
b) Decrypted strings in memory are removed after being used
c) Hiding applications in a different desktop
d) MBR wiping ability
e) Ransomlock similarities such as being able to lock the desktop
f) Hidden VNC Connection
g) Modular design, allowing easy updates on victim machines
h) Stealth: Callback Traffic, APIs, Registry keys and any other indicators are decrypted dynamically
i) Drops Pony malware as a module to act as infostealer
LATENTBOT is able to scan for cryptocurrency wallets via Pony stealer 2.0 malware plugin, it uses a custom encryption algorithm to protect command and control (C2) communications.
“LATENTBOT itself is not targeted in nature – it has been observed in multiple industries – but it is selective in the types of Windows systems to infect. For example, it won’t run in Windows Vista or Server 2008. LATENBOT also uses compromised websites as CnC infrastructure, making infection easier and detection harder.”
The researchers discovered that when the bot is running on a laptop, it will query the battery status via GetSystemPowerStatus and call SetThreadExecutionState in order to prevent the system from entering in sleep mode.
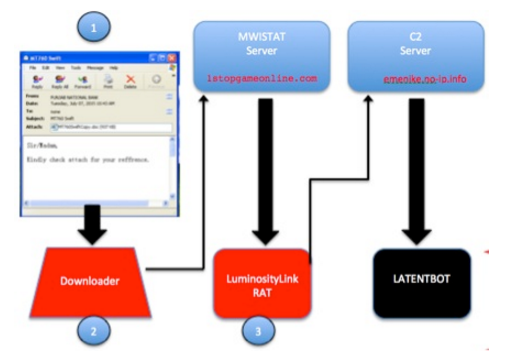
The threat actors exploit emails as attack vector, they have been using malicious messages containing an old word exploit created with Microsoft Word Intruder (MWI) exploit kit. When victims opened the document an embedded malicious executable runs, contacting the C&C server for campaign tracking and download the second stage binary, which turns out to be a LuminosityLink RAT.
“During our analysis, the Word documents downloaded LuminosityLink as the second stage binary. LuminosityLink is a full-featured RAT that has the ability to steal passwords, record keystrokes, transfer files and activate attached microphones or webcams.” continues the report.
“Since the running LuminosityLink is a RAT that offers multiple capabilities to fully control the infected box, it is surprising that another payload is being downloaded from a secondary C2 at emenike[.]no-ip.info (180.74.89.183),” FireEye detailed. That new module is LATENTBOT.
The report, published by FireEye includes full details on the back door, enjoy it!
Source:https://securityaffairs.co/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











