A security researcher discovered a new variant of the Angler exploit kit that includes the exploit code for a recently patched Adobe Flash Player flaw.
The French security researcher “Kafeine” has discovered a new variant of the popular Angler exploit kit that includes the exploit code for a recently patched Adobe Flash Player vulnerability (CVE-2015-8446). Kafeine reported that new exploit code was added to the Angler exploit kit on December 14.
The new Angler exploit kit has been used by threat actors in the wild to spread the TeslaCryptransomware.
Once the ransomware infects a PC, it encrypts files and renames them with a .vvv extension requesting the payment of a $500 ransom within one week, after which the price to recover the files increases to $1,000.
The CVE-2015-8446 vulnerability is a Flash Player heap buffer overflow flaw that Adobe patched on December 8. had been added to Angler.
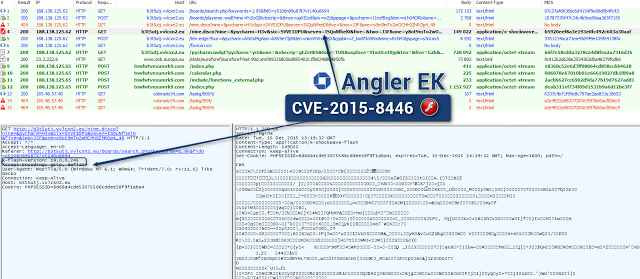
This vulnerability was discovered by an anonymous researcher who reported it via the Zero Day Initiative (ZDI). Recently Adobe released Flash Player 20.0.0.228 and 20.0.0.235 versions (Desktop Runtime with support for Firefox and Safari) that fixed 77 security issues.
Kafeine added that the exploit for the Flash vulnerability has been used by threat actors to deliver the Bedep Trojan Downloader.
Last week experts at Malwarebytes confirmed that the code for the CVE-2015-8446 exploit included in the Angler Exploit kit had been used by cyber criminals to serve the TeslaCrypt ransomware.
Once it infects a computer, the ransomware encrypts files and renames them with a .vvv extension. Victims are instructed to pay $500 within one week, after which the price for the private key needed to recover the files increases to $1,000.
The experts noticed that the new variant of the Angler Exploit Kit had a low detection rate at the time of its discovery.
Source:https://securityaffairs.co/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











