The Ring is a Wi-Fi doorbell that connects to your home Wi-Fi. It’s a really cool device that allows you to answer callers from your mobile phone, even when you’re not home.
It’s one of the few IoT devices we’ve looked at that we might even use ourselves. It acts as a CCTV camera, automatically activating if people come close to your home. You can talk to them, to delivery couriers, to visitors etc. It can even hook up to some smart door locks, so you can let guests in to your home.
It is genuinely useful! Unlike most IoT devices 🙂

BUT
To set it up, one has to connect it to your home Wi-Fi router. That requires that you give it your Wi-Fi key. Here’s where the problem lies.
First some analysis of the hardware.
The major component is the doorbell itself, which is comprised of the necessary circuitry, a li-ion battery, a USB charging port for the battery and a set up button. This is connected to a back plate which attaches the doorbell to the wall and can provide power from an AC source.

Once set up, you fix it to the outside of your house. It’s secured with two Torx T4 screws.

..which means it is extremely vulnerable to theft. Indeed, Ring offer a free replacement if stolen.
The attack, stealing the Wi-Fi key
Take off the door mounting, flip it over and press the orange ‘set up’ button.

Pressing the setup button sets the doorbell’s wireless module (a Gainspan wireless unit) into AP mode. This might sound very familiar if you read our post about the Fitbit Aria scales vulnerability.
An access point is created with this format:
Ring-1ea7a2
…where the last three octets are the end of the MAC address. Simply connect to it.
From here the Gainspan’s HTTP server can be connected-to, to talk directly to the wireless module via a REST style API.

If the URL /gainspan/system/config/network is requested from the web server running on the Gainspan unit, the wireless configuration is returned including the configured SSID and PSK in cleartext.
The doorbell is only secured to its back plate by two standard screws. This means that it is possible for an attacker to gain access to the homeowner’s wireless network by unscrewing the Ring, pressing the setup button and accessing the configuration URL.
As it is just a simple URL this can be performed quite easily from a mobile device such as a phone and could be performed without any visible form of tampering to the unit.
An example:
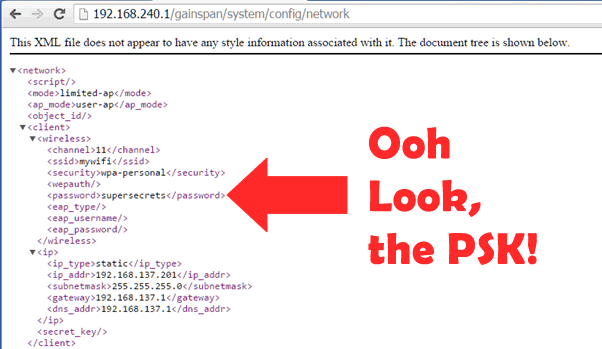
This is quite a fail: walk up to door, remove doorbell, retrieve users Wi-Fi key, own their network!
- Did Ring ever intend to expose this functionality, or was is this just default functionality that Gainspan have in their firmware? As it’s a standard Gainspan URL it looks like they just hadn’t disabled the configuration.
- The Wi-Fi key is still stored in the doorbell somewhere – how well protected is it now? It’s most likely stored in the module, somebody with a soldering iron could possibly get it.
- Having physical access to the doorbell means we might be able to upload modified firmware. Your doorbell becomes a back door?
Source:https://www.pentestpartners.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











