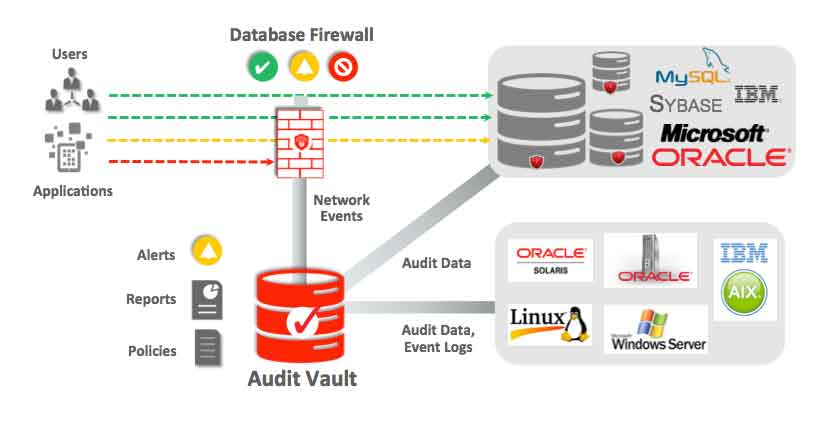
Databases can be a treasure trove of confidential data. Normally most databases contain confidential information, private data of companies, people, intellectual property, employees or customers. Confidential data may include the customer data, employee’s salary data, employee address data, patient records, financial data, credit card numbers and much more. From a database security company’s point of view, a database of any company or organization, is a system which is formed by sets of organized data, which are stored and structured in cloud or local servers, and any kind of data treatment or access by any individual or application should be done with access or modification permissions. According to database security audit services consultants, any concurrent database access by several users without any database security solutions involves many risks such as database hack or deletion. According to a survey of a database security company, lost or stolen data, especially confidential data, can cause brand damage, fines, legal complications and disadvantage over competition.
These risks are forcing companies to take into account issues such as database security and implementation of database security solutions. Alternatively, companies can take help of database security audit services which include backup and recovery in the event of incidents caused by human error, natural disasters and in many cases by cyber-attacks.
Database security services aim to protect the database from unauthorized activities that endanger the structure, availability, consistency and integrity of database. Also privacy and personal data protection regulations require the implementation of database security audit services and solutions to align with data protection law. Database security companies must achieve implementation of data security using procedures that allow access control, restructure or update of the database according to application requirements without changing much the design of the data model.
Companies or organizations can implement database security solution at the application level, the infrastructure level or at database storage level explains an expert from database security company. The database security solution implemented at the database storage level (disk or tape), secures against the risks such as storage media loss or theft. But the same database security solution cannot secure against malware infected infrastructure or internal employees.
The database security solution implemented at the application level is another option and provides the highest level of control. But the same database security solution can’t secure against loss or theft of storage media. Also, implementation of the database security solution at the application level requires many changes in the application and at times is not be a viable approach.
Because of these complexities, many companies and organizations are choosing help of experts of database security company so that they can implement advanced solutions. These database security solutions provide database security at storage level, application level and the level of data flow.
How you can resolve the database security problem?
According to experts from IICS – International Institute of Cyber Security, the database security solutions and services can add new levels of security to your company and help your company to protect and manage confidential data in an effective manner. Our services include database security audit services and database security training courses. Our database security audit services manage the confidentiality, integrity and continuity of business information, thus increasing the credibility and reliability of the company. The following are some aspects and advantages of our database security audit services:
- Database security audit services include penetration testing. This helps in putting security controls in the database.
- All the database infrastructure is subjected to database security audit services. Without the help for database security audit services it would be difficult to know all the risks and vulnerabilities.
- Database security audit services help in implementing a monitoring system. The system has the ability to monitor and verify all activities. This system can detect any unusual and unauthorized activity.
- Creating processes that would develop and maintain detailed information about the vulnerabilities and business risks of company’s networks and applications.
- Ensure proper implementation of cryptographic controls management procedures for safeguarding and strengthening database upon completion of database security audit services.
- Database security audit services ensure proper implementation and regular execution of database backup processes.
- Generate policies and procedures for effective management of service and third party providers.
- Implementation of business continuity plan, forensic and data recovery plan in case of any cyber attack.
- The database infrastructure would be protected against fire, theft and other forms of physical damage. Database security audit services generate policies for physical and logical security.
With database security training courses, you will learn to manage risks, security incidents, vulnerabilities and decrease the risks of non-compliance with the personal data protection law. The following are some aspects and advantages of database security training:
- You can increase the efficiency by reducing management costs linked to database security in a large-scale environment with the help of security management architecture taught during database training course.
- With database security training, you can easily learn all the database security skills in real-time with lot of practice.
- During the database security training course, you can implement database security controls on the actual infrastructure and add higher levels of security.
- Customize database security training can be easily integrated into database management systems and other security solutions already implemented.
- During the course you learn implementation of database encryption solution.
- Also the topics such as simplification of compliance with data privacy obligations, backup automation, implementation of industry best practices and standards are part of database security training course.
Source:https://www.iicybersecurity.com/database-security-audit-services.html

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.