A new ransomware has been discovered by security researcher Yonathan Klijnsma called Maktub Locker that shows the most attention to detail that I have see on its ransomware payment site. Before we get to the decryption site, let’s just take a moment to give a brief summary of the ransomware itself.
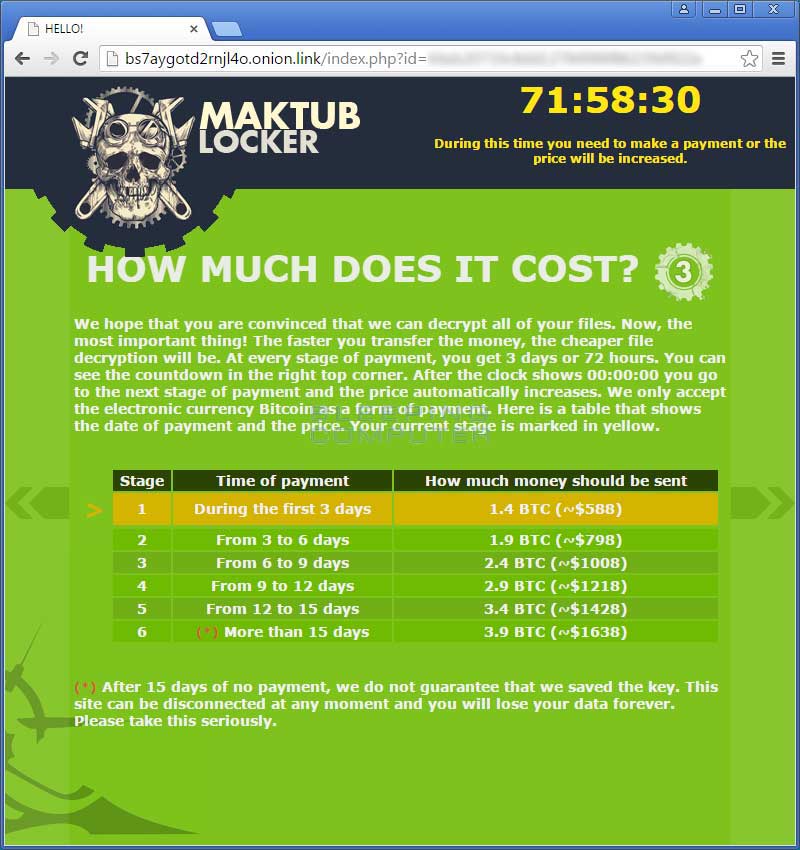
So far Maktub Locker appears to be your standard variety that encrypts your data and then ransoms your files for 1.4 bitcoins. After a certain amount of time, you enter a new stage where the ransom amount increases, where ultimately the ransom price tops out at 3.9 bitcoins. Maktub Locker does not currently use a static extension for encrypted files, but rather assigns a random extension for each victim.
At this point the ransomware is currently being analyzed and not much is known about it’s inner workings and whether we can defeat its encryption method. What we do know is that it is spreading as an executable with a .SCR extension attached to emails. This attachment pretends to be an updated Terms of Service document that when opened launches the ransomware. An example filename for this attachment is TOS-update-2016-Marth-18.scr.
When the ransomware is launched, it will display a Word document that pretends to be an updated Terms of Use, while the ransomware is quietly encrypting the data on the victim’s computer.
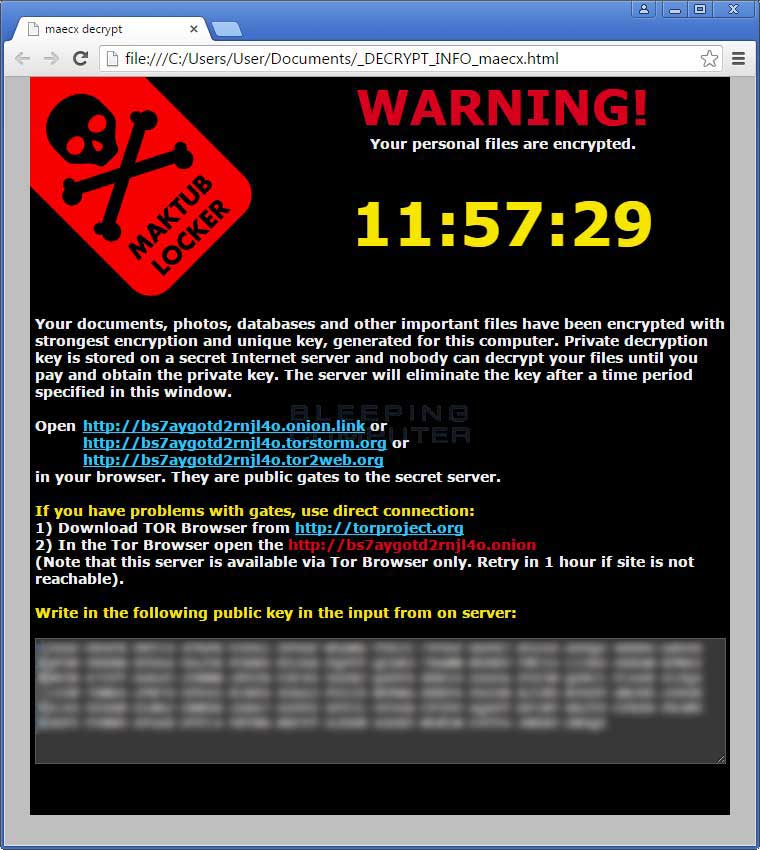
When Maktub has finished encrypting your files, it will display a ransom note titled _DECRYPT_INFO_[random].html, which can be seen below.
As much as I am against those who profit from malware, what makes Maktub Locker really stand out to me is not the infection but the attention to detail that was given to their TOR decryption site. This ransomware site is by far the nicest, if not artistic, ransomware site that I have seen to date.
The decryption site is broken up into 5 pages, with each page containing its own artistic theme. This artwork does not appear to have been designed by the ransomware developers as the logo was taken from a designer on Deviant Art. I could not, though, find any matches for the background artwork on each of these pages.
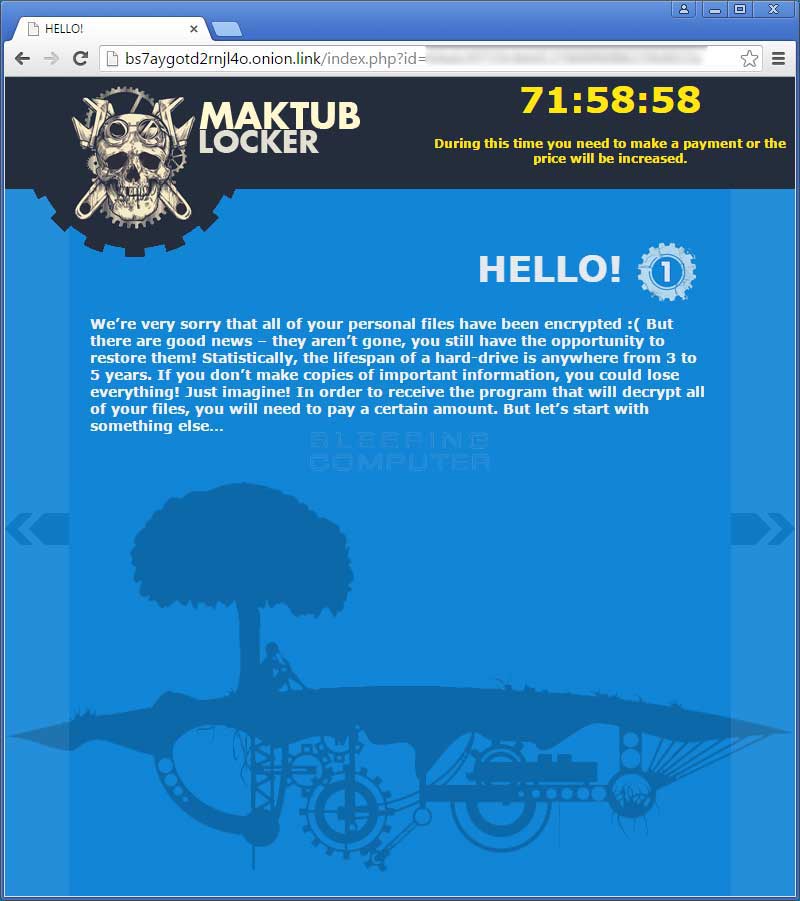
The first page of the decryption site is a brief introduction as to what happened to the victim’s files.
The next page is your standard free decryption page. This particular ransomware offers 2 free decryptions rather than the standard one file.

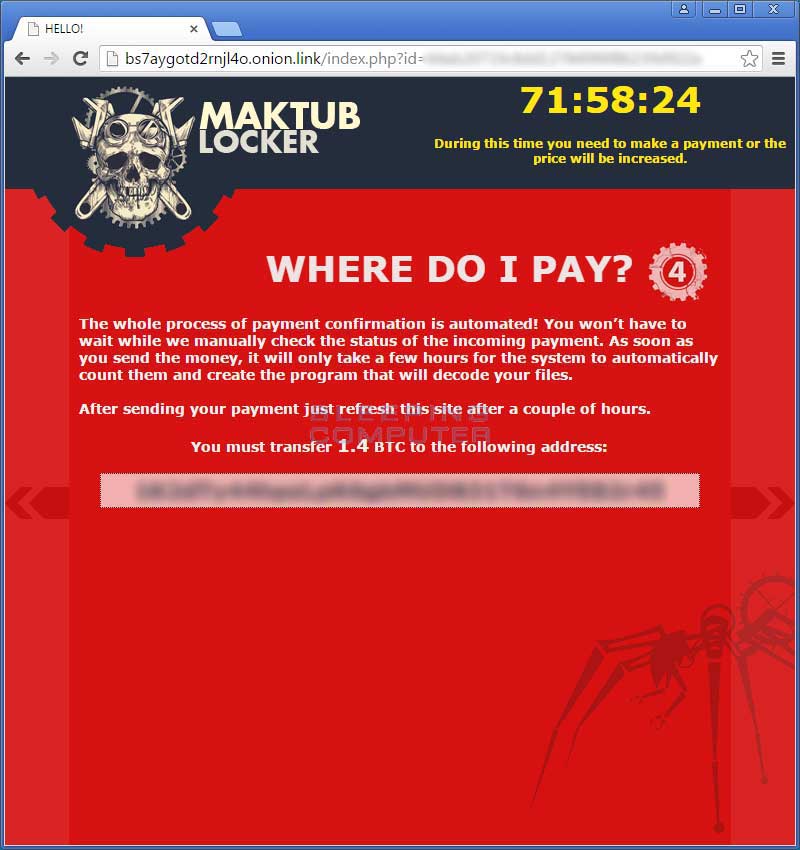
The third page shows the different payment stages that the victim can go into. As more time goes on, the victim goes into the next payment stages with a higher ransom amount.
The fourth page will provide the unique bitcoin address that the victim must use to send the ransom payment.
Finally, the fifth page is your standard how to buy bitcoins page.

If the ransomware industry does not work out for these people, they may have a shot at web design. As more information is released, I will be sure to post it on the site.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











