The Rokku Ransomware is a new infection currently being spread in email attachments. When infected, a victim’s data files will be encrypted and then ransomed back for .24 bitcoins or approximately $100 USD. At this time there is no way to decrypt the files for free, but this infection is still being analyzed for weaknesses.
The Rokku Encryption Process
When Rokku is first installed it will remove all shadow volume copies on a computer so that they cannot be used to restore your data. It will then encrypt the data files on the computer and append the .rokku extension. This means that a file normally called test.jpg would now be called test.jpg.rokku.
According to Fabian Wosar, of Emsisoft, when Rokku encrypts a victim’s data it will use theSalsa20 algorithm and will encrypt each files with its own unique key. A file’s key is then encrypted using RSA and stored in the last 252 bytes of the associated file. This allows the developers to provide individual decryption keys for test file decryption. This is also the first ransomware that I know of that uses the Salsa20 algorithm, which provides much greater encryption speeds compared to AES.
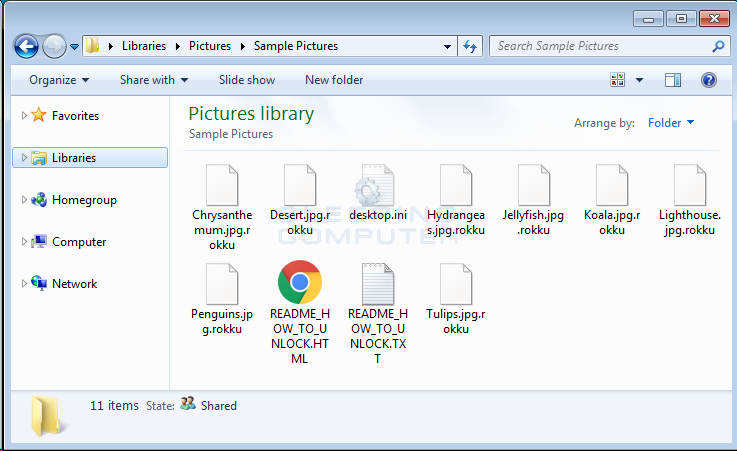
In each folder that is encrypted and in the victim’s Startup folder, Rokku will create two ransom notes titled README_HOW_TO_UNLOCK.HTML and README_HOW_TO_UNLOCK.TXT. These ransom notes contain information on what has happened to the victim’s files and links to Rokku’s Tor payment site.
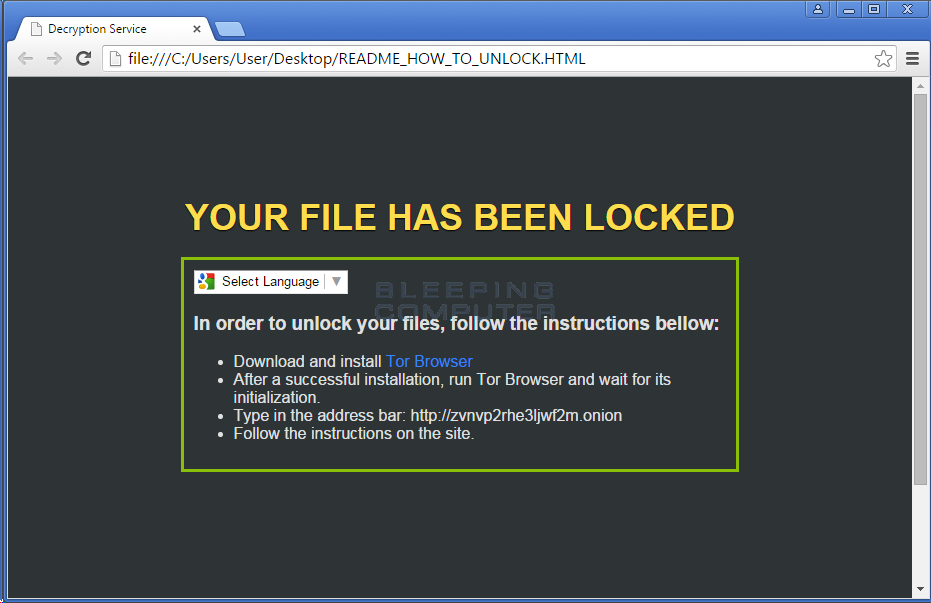
An interesting feature of Rokku is the use of the Google Website Translator Plugin in the ransom notes. This allows them to create one English ransom note and easily use the translator for those who do not understand English.
At this time Rokku cannot be decrypted for free, but because it utilizes a weak algorithm such as RSA-512 to encrypt the Salsa20 keys, a future solution may be discovered.
The Rokku Unlock Service Tor Payment Site
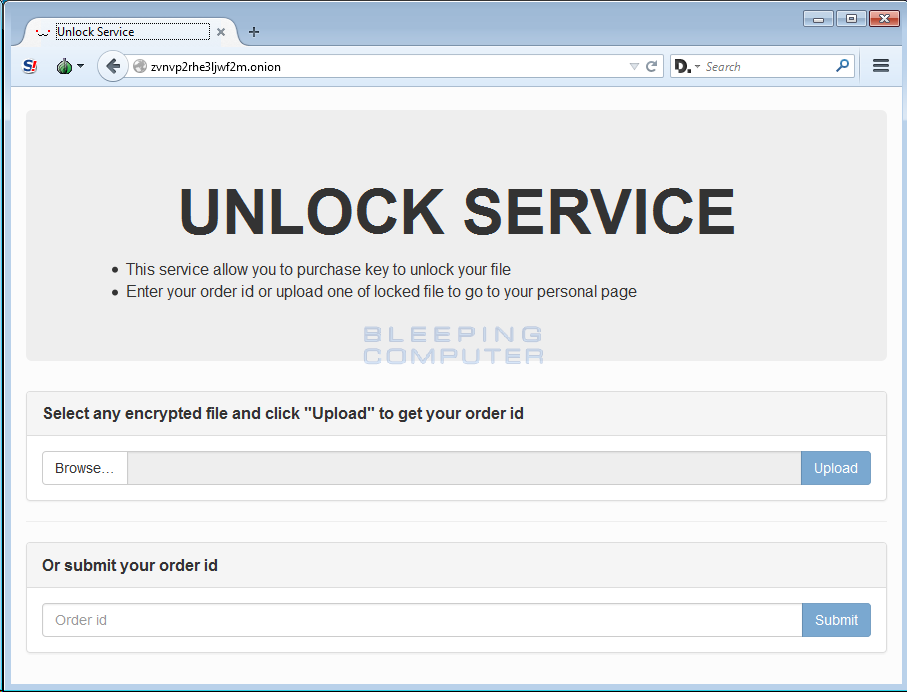
The Rokku Ransomware utilizes a Tor payment site called the Unlock Service. This service is interesting as it requires you to upload an encrypted file in order to login for the first time. Once you login you are then provided a unique “order id” that can be used for future logins.
Once logged in you will be shown the Unlock Service screen that contains your order id, the amount of bitcoins the victim needs to pay, and a bitcoin address the payments should be sent. A lot of mention has been given to the fact that a QR code is shown on this page as well, but this is not necessarily a new feature as CryptoWall has been offering the ability to get a QR code for a while.
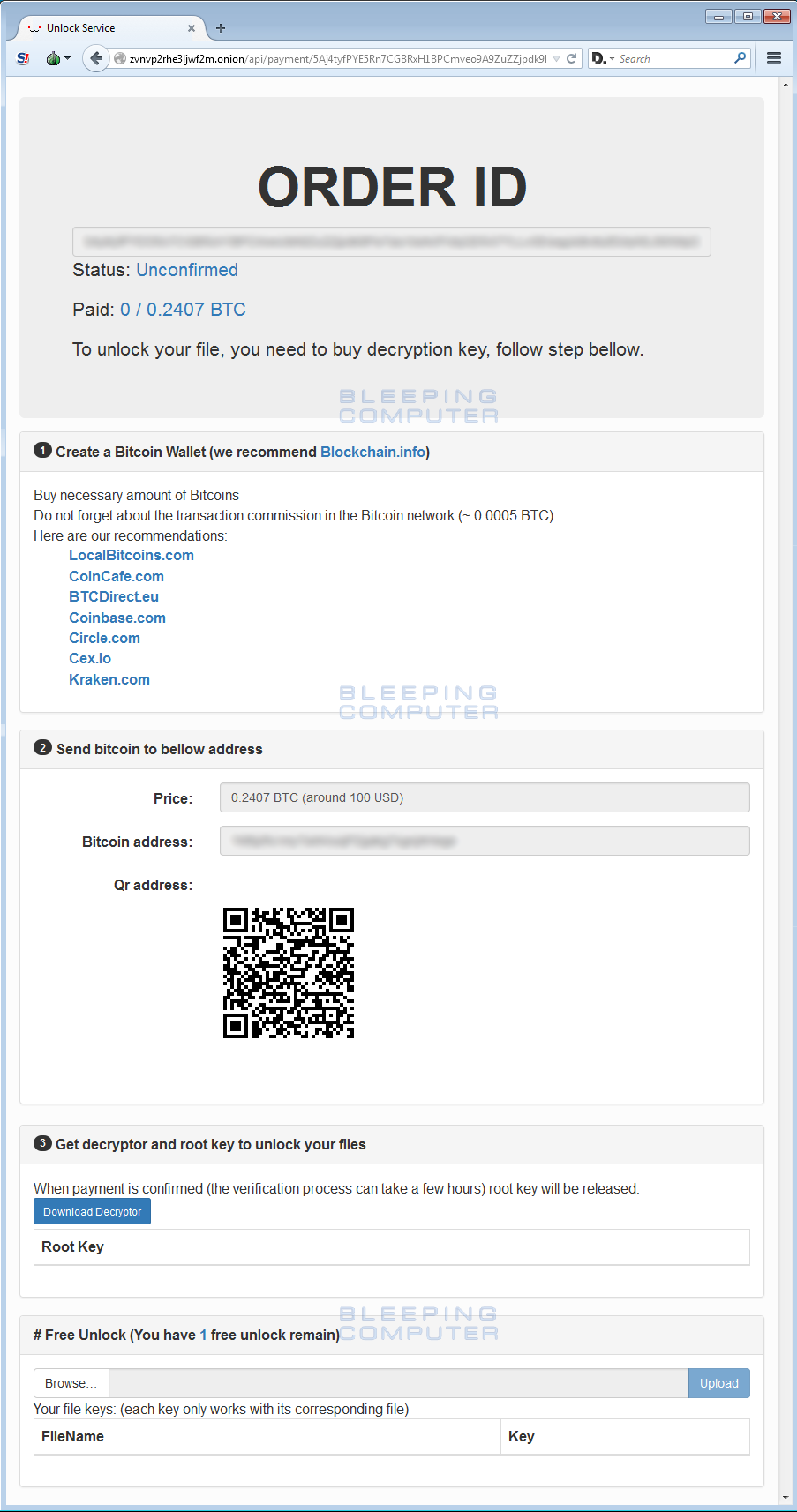
The Rokku Unlock Service also allows a victim to decrypt one file for free to prove that they can do so. When you upload a file, its individual decryption key will be listed and you can then download the decryptor to decrypt that one file. Please note that the decryption key that is given will only work on that particular file as each file has its own key.
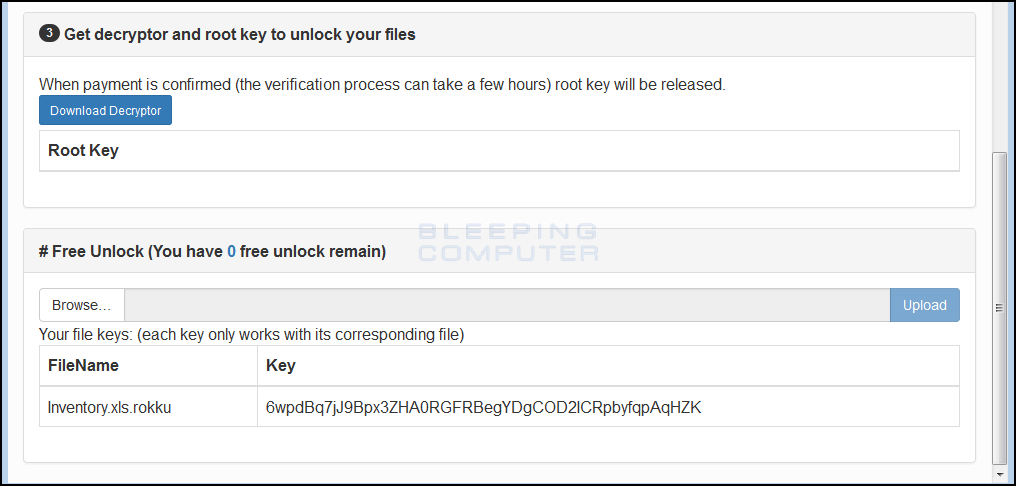
This key can then be entered into the decryptor so that you can decrypt the test file as shown below.
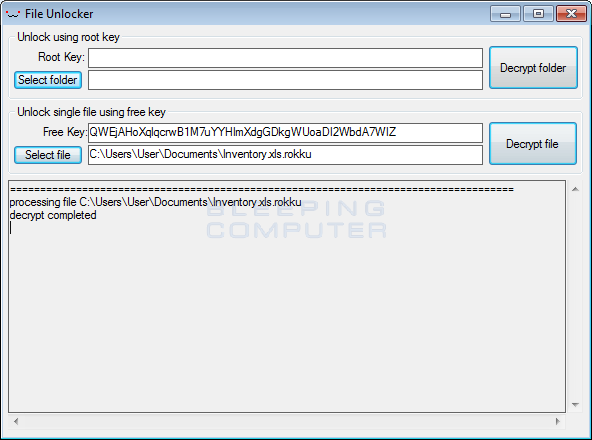
As already stated, currently this ransomware cannot be decrypted for free. Analysts are, though, analyzing it further to see if there is a weakness in the RSA-512 component so that the individual file keys can be decrypted.
How to Remove the Rokku Ransomware
The Rokku Ransomware does not currently set any autostart locations for any files other than the ransom notes. That means that there really is no active ransomware infection once your computer is rebooted or the malware has finished. To remove Rokku, simply scan your computer with your preferred anti-virus solution in order to remove the executable. The ransom notes, on the other hand, will have to be removed manually as most AV vendors do not detect ransom notes and other non-malicious files.
Files associated with the Rokku Ransomware:
%StartMenu%\Programs\Startup\README_HOW_TO_UNLOCK.HTML
%StartMenu%\Programs\Startup\README_HOW_TO_UNLOCK.TXT
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











