A new installer for Petya was released that also installs the Mischa Ransomware if it is unable to gain Administrative privileges. In the past, when Petya was installed it requested Administrative privileges so that it could modify the master boot record. If it was unable to gain these privs, the installer would not do anything to the computer. This has all changed, though, as now if the installer is unable to gain the required privs, it will instead install the Mischa Ransomware instead.
Petya + Mischa Ransomware = Double the Trouble
There is nothing a ransomware developer hates more than leaving money on the table and this is exactly what was happening with Petya. As Petya required administrative privileges to modify the master boot record, if it was not able to do so, the intallation failed. To counter this, the Petya devs did something clever, they bundled an extra ransomware called Mischa into the installer that will be installed when the Petya is unable to.
When a victim runs the executable, which is disguised as a PDF job resume, the installer will try to gain administrative privileges so that it can modify the MBR of the system drive. If it is unable to do so, whether that be because the user clicks no at the UAC prompt or for other reasons, the installer will instead install the Mischa Ransomware as it does not require administrative privileges.
Introducing the Mischa Ransomware
Unlike Petya, the Mischa Ransomware is your standard garden variety ransomware that encrypts your files and then demands a ransom payment to get the decryption key. Currently the ransom payment for Mischa is set at 1.93 bitcoins or approximately $875 USD.
The installer for Petya/Mischa is distributed via emails pretending to be job applications. These emails contain a link to a cloud storage service that contains an image of the supposed applicant and a downloadable executable that starts with PDF. This executable is named something similar to PDFBewerbungsmappe.exe. When a victim downloads the executable, it will have a PDF icon to make it appear as a PDF resume. This executable, though, when started tries to install Petya, and if that fails, installs the Mischa Ransomware.
When Mischa is installed it will scan the computer for data files, encrypt them them using the AES encryption algorithm, and then append a 4 character extension to the filename. For example, test.jpg may become test.jpg.7GP3. While encrypting a file Mischa will store the encrypted decryption key at the end of the encrypted file. An annoying aspect of Mischa is that not only will it encrypt your standard data file type (PNGs, JPGs, DOCXs, etc), but it will also encrypt .EXE files.
In each folder that Mischa encrypts a file it will also create two ransom notes called YOUR_FILES_ARE_ENCRYPTED.HTMLand YOUR_FILES_ARE_ENCRYPTED.TXT. These ransom notes contain information about what has happened to your files and links to the TOR payment sites. Also included in the ransom note is a special code that you must use in the payment site to pay the ransom.
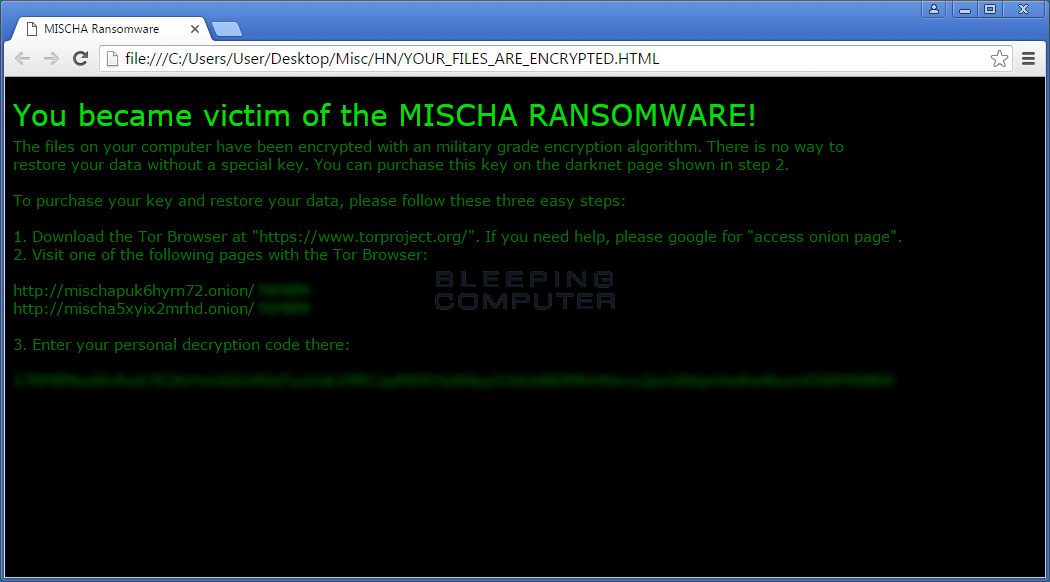
More information about the payment site is below. If you would like regarding this ransomware you can ask in the Mischa support topic: MISCHA RANSOMWARE Support and Help Topic – YOUR_FILES_ARE_ENCRYPTED.HTML & TXT.
The Mischa Ransomware TOR Payment Site
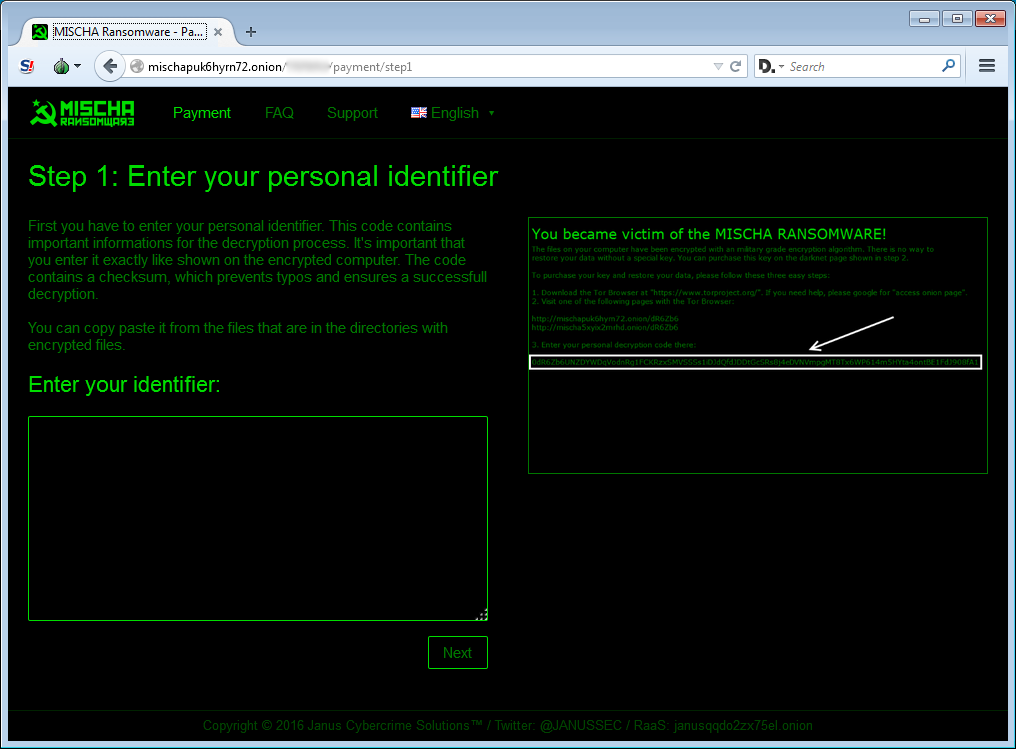
When you first go to the TOR payment site, you will be presented with a payment wizard that provides steps to make the ransom payment. The first step is to enter the personal code that is included in the victim’s ransom note and click next.
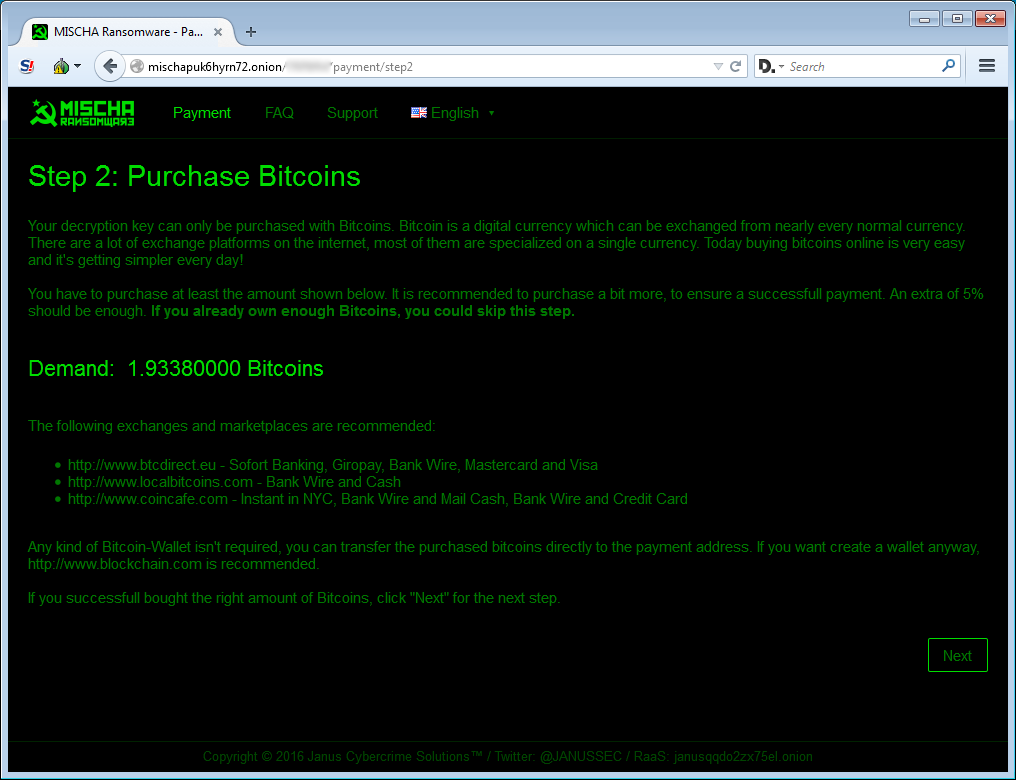
On the second page, or Step 2, you will be presented with information on how to many bitcoins you must purchase to pay the ransom and information on how to purchase them. Currently the ransom is set to about $875 USD or approximately 1.93 bitcoins.
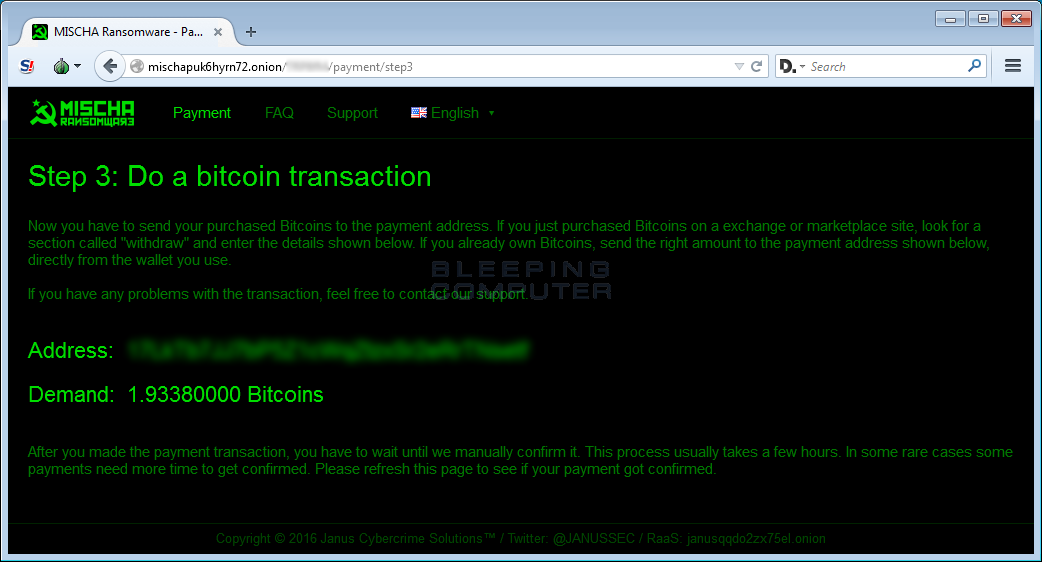
The third, and final, step will display the bitcoin address you must send payment to.
The Mischa Ransomware payment site also includes a support page that can be used to ask the malware developers questions and a FAQ, or Frequently Asked Questions, page, as shown below.
Unfortunately, at this time there is no way to recover your files for free, but it is always suggested that you attempt to use Shadow Explorer to see if your Shadow Volume Copies are intact. These can then possibly be used to restore older versions of the encrypted files. You can find information on how to do this in the Locky Information guide: https://www.bleepingcomputer.com/virus-removal/locky-ransomware-information-help#shadow.
As always, if you have questions or would like to discuss this ransomware, you can do so in this topic: MISCHA RANSOMWARE Support and Help Topic – YOUR_FILES_ARE_ENCRYPTED.HTML & TXT.
Files associated with the Mischa Ransomware:
YOUR_FILES_ARE_ENCRYPTED.HTML
YOUR_FILES_ARE_ENCRYPTED.TXT
PDFBewerbungsmappe.exe
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











