Attackers take social engineering to a totally new level. There’s a sneaky new trick going around that can fool some people into divulging their two-factor authentication code to crooks, while thinking they’re actually protecting their accounts.
Two-factor authentication, or 2FA, is a second layer of authentication that many online services support, from banks to Google, from Facebook to government agencies.
2FA works by requiring a user to enter a code that they received via SMS on their phone after they logged into a 2FA-protected account. If the user doesn’t enter the code promptly, the login is classified as a hacking attempt, and the user blocked from accessing the account, even if they entered the correct password. You can see the benefits, right?
Crooks pass as Google, ask users for “verification code”
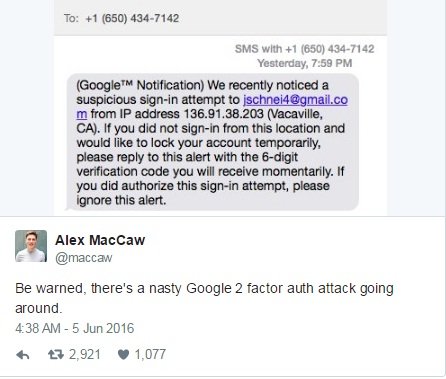
This past week, Alex MacCaw, co-founder of Clearbit.com, tweeted out the image of an SMS he had just received.
An unknown attacker had sent MacCaw an SMS message posing to be from Google. The SMS read as follows:
“ (Google™ Notification) We recently noticed a suspicious sign-in attempt to jschnei4@gmail.com from IP address 136.91.38.203 (Vacaville, CA). If you did not sign-in from this location and would like to lock your account temporarily, please reply to this alert with the 6-digit verification code you will receive momentarily. If you did authorize this sign-in attempt, please ignore this alert. ”
Basically, the attackers were mentally preparing the victim to receive the 2FA verification code, for their illegal login attempt they were about to carry out.
The crooks were going to access MacCaw’s account, and when his 2FA system would kick in, MacCaw would act to lock his account by sending the “verification code to Google.” In fact, MacCaw would be sending the 2FA code to the crook, who would then enter it in the login page and access his account, with his cooperation.
Fortunately, MacCaw recognized their tactics and didn’t fall for this new type of social engineering trick.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











