Intel x86 CPUs Come with a Secret Backdoor That Nobody Can Touch or Disable.
Hardware security expert Damien Zammit says that recent Intel x86 CPUs come with a secret subsystem that works as a separate CPU inside your CPU, can’t be disabled, and nobody can review the closed proprietary code.
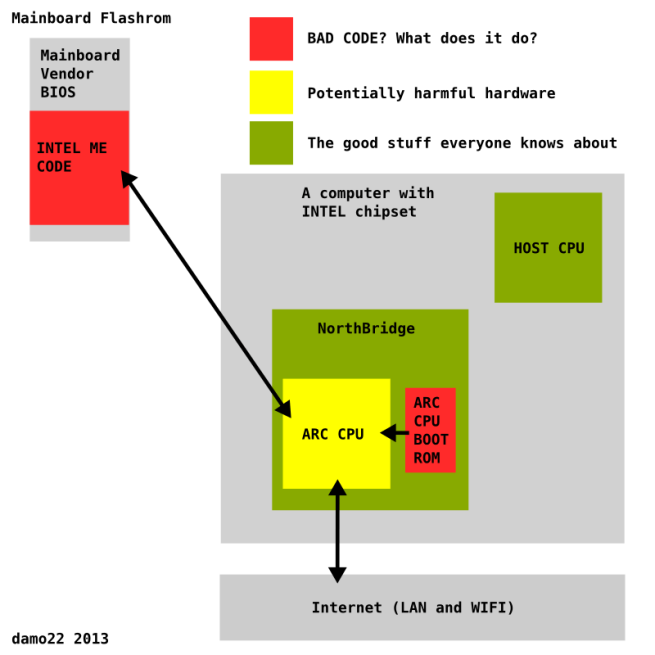
Called the Intel Management Engine (ME), this subsystem is literally embedded inside the x86 chipset, where it runs its own closed-source firmware. Intel says ME was designed to allow big enterprises to manage their computers remotely, for a fee of course, via the Active Management Technology (AMT).
Zammit says that AMT runs separately from any OS a user might install, allowing access to the computers in any deployment.
Intel ME sets up a TCP/IP server, accesses memory behind your back
In order for AMT to have all these remote management features, the ME platform will access any portion of the memory without the parent x86 CPU’s knowledge, and also set up a TCP/IP server on the network interface. Zammit says that this server can send and receive traffic regardless if the OS is running a firewall or not.
There are some problems which Zammit details. The first is that nobody outside Intel’s headquarters has ever seen the source code of the ME platform.
Secondly, the ME firmware is signed cryptographically with an RSA 2048 key that can’t be brute-forced in a human life (or more).
The third obstacle Zammit detailed is the fact that on newer Intel Core2 CPU series, the ME can’t be disabled because the CPU will refuse to boot.
Fourth and last, there’s no way to audit the health of the ME firmware. A security researcher wouldn’t be able to search for any alleged NSA backdoors, nor will he be able to check if his PC’s CPU was compromised by an attacker’s rootkit.
Intel ME: the perfect backdoor, or the unremovable rootkit?
Zammit’s gripe is that nobody has access to this CPU-in-CPU except the all-mighty Intel engineers.
“A large portion of ME’s security model is “security through obscurity”, a practice that many researchers view as the worst type of security,” Zammit wrote in an exposé for BoingBoing. “If ME’s secrets are compromised (and they will eventually be compromised by either researchers or malicious entities), then the entire ME security model will crumble, exposing every recent Intel system to the worst rootkits imaginable.”
Security researchers have previously brought up the issue of hidden code in Intel firmware, but this was in the Intelligent Platform Management Interface (IPMI) protocol, a predecessor of the Active Management Technology (AMT) currently included in ME.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











