Developers with the open source content management framework Drupal today patched a series of highly critical remote code execution bugs in three separate modules. If exploited, the bugs could let an attacker take over any site running the modules. Fixes for pushed for RESTful Web Services, a module used for creating REST APIs, Coder, a module used for code analysis, and Webform Multiple File Upload, a module used for collecting files from site visitors. Collectively the modules are installed on more than 10,000 sites, according to Greg Knaddison, a Drupal developer and member of Drupal’s Security Team. RESTWS is the most popular of the three and according to Knaddison, is currently installed on more than half of the affected sites. Knaddison acknowledged in a tweet on Tuesday that while not every Drupal user will need to update, there is an urgency to do so.
The official advisory issued by Drupal on Wednesday makes a point to clarify that Drupal core isn’t affected by the vulnerabilities, but any site running the modules is. It claims that any site visitor could have exploited the vulnerabilities to take a variety of actions of the site, the most concerning being able to take over any affected site and server. Different conditions in each module could have triggered remote code execution if an attacker sent specially crafted requests that resulted in arbitrary PHP execution.
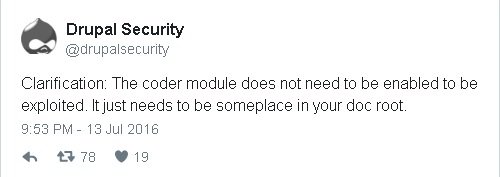
Drupal clarified Wednesday afternoon that for the vulnerability in Coder, the module does not have to be enabled in order to be exploited. That fix addresses a problem in which the module doesn’t sufficiently validate user inputs in script files that have PHP extensions. A user could’ve made requests directly to the file to execute code, the advisory claims.
Source:https://threatpost.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











