Short Bytes: TOR anonymity network is one of the most useful online security measures that we’ve got. However, attackers have come up with new ways to puncture this security envelope from time to time. In a related development, using 1,500 specially-crafted hidden services called “Honions”, security researchers have identified more than 100 malicious TOR nodes, or HSDirs, to be precise.
Uncovering another rotten layer of The Onion Router, researchers have located more than 100 malicious nodes that are probably spying on the hidden services being used by the Dark Web sites.
This research was carried out by two Northwestern University researchers Amirali Sanatinia and Guevara Noubir. They kept a close eye on the TOR network for 72 days and found multiple malicious TOR Hidden Services Directories (HSRDirs) on the network.
What are TOR Hidden Services Directories (HSRDirs)?
HSDirs, basically a type of TOR nodes, are the servers that stay hidden and operate inside TOR itself. To maintain the complete secrecy, traffic to the hidden services never leaves the TOR network. To achieve this purpose, the exit node and hidden service are at the same place. HSDirs don’t know about the location of a hidden service, but are useful while connecting a hidden server to the TOR users.
In simpler words, the HSDir nodes are very important as they are a way to hide the true IP address of a user and talk to the rest of the TOR network.
What if HSDirs are compromised?
This will allow the hacker to sniff your traffic and stay anonymous using TOR–both at the same time.
The researchers used 1,500 specially-crafted hidden services called “Honey Onions”, or Honions. They measured about 40,000 requests and using some smart calculations, they found about 110 malicious HSDirs. These nodes were located mostly in the US, France, Germany, UK, and the Netherlands.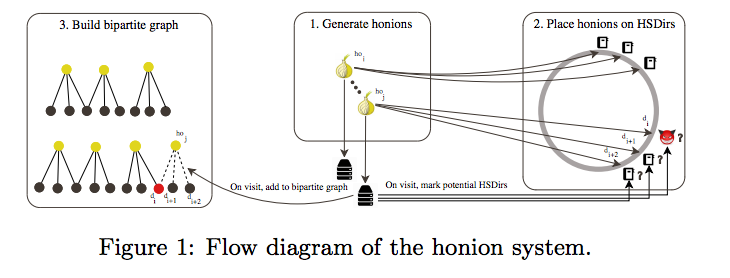 Elaborating these results further, the researchers write:
Elaborating these results further, the researchers write:
If we compare 110 nodes to the total 7,000 TOR nodes, we have 3% malicious TOR nodes. Sounds scary!
Well, the TOR developers are aware of this issue and they are constantly working to identify and remove the harmful HSDir nodes. The TOR Project is also working on a new design that’ll make it harder for attackers to target the users. Another great piece of research was carried out by MIT, creating Rifle— a TOR-alternative that promises to be better.
Source:https://fossbytes.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











