Short Bytes: A man named Ivan Kwiatkowski managed to install Locky ransomware on the machine of a person who was pretending to be a tech support executive of a reputed company. Ivan wrote his experiences in a blog post tells that how the tech support scammer fell into the pit he dug for innocent people.
Ivan Kwiatkowski had a contact with such scammer when his parents informed him about their machine being infected by a virus. “A few days ago, I received a panicked call from my parents who had somehow managed to land on a (now defunct) web page (snapshot here) claiming they had been infected by Zeus,” Ivan narrates the story.
“This horrible HTML aggregate had it all: audio message with autoplay, endless JavaScript alerts, a blue background with cryptic file names throwing us back to Windows’ BSoD days, and yet somehow it displayed a random IP address instead of the visitor’s one.”
In his blog post, Ivan described the two instances he encountered with the scammers, a different person each time. Before contacting the “tech support”, he first set up a mouse trap. He loaded an old XP virtual machine which he used to pretend that he was “businessman working on an important, high-figure contract, and that time is of the essence”.
During the first interaction, Ivan talked to Patricia who was kind to him and made him download a support client which was, in fact, digitally signed. After running some false commands in CMD, she suggested Ivan, who was pretending to be as dumb as possible, to buy their anti-trojan software. The exclusive software was only available through Microsoft premium partners, she said. “Oh, so I just have to get it from microsoft.com then?” Ivan asked. She agreed to the same and hung up the call.
In the second interaction, Ivan was introduced to a new person named Dileep Singh Shekhawat, who appeared to be more experienced than Patricia. Dileep suggested a different package which priced higher at $333. Ivan agreed to pay for the software package and arranged some test credit card numbers which weren’t going work on the other end. He repeated the card details around 10 times to Dileep. No matter, how many times he entered the card details, the payment wasn’t going to proceed for obvious reasons.
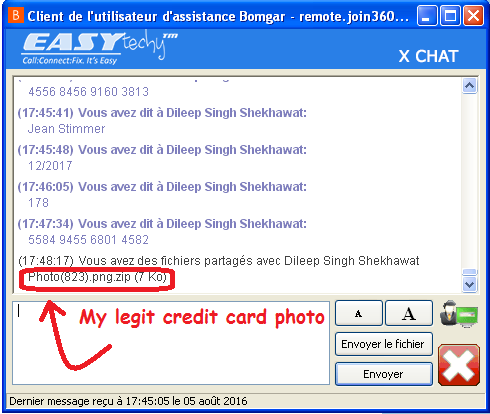
During this whole drama, Ivan got struck with an idea. He took some Locky ransomware sample from in mail box, wrapped it inside an image and pushed to Dileep who was still struggling with the payment. “I took a photo of my credit card, why don’t you input the numbers yourself? Maybe that’ll work.”
After the image reached the other end, “I tried opening your photo, nothing happens,” Dileep replied.
Ivan kept him busy to give the ransomware time to complete the operations in the background. At last, he told Dileep that he would call him again after contacting the bank.
“Whenever one stumbles on an obvious scam, the civic thing to do is to act like you buy it”, Ivan concludes. “Rationale: scammers don’t have the time to separate legitimate mugus from the ones who just pretend. Their business model relies on the fact that only gullible people will reply.”
Source:https://fossbytes.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











