This week we’ve detected an unsophisticated piece of malware targeting mobile subscribers in North America. The malware termed a RAT (remote access tool) is being sent via SMS in the US and has been witnessed a few times recently in various forms.
The number originated from an OTT carrier (Twilio) and was found to be sending messages to hundreds of subscribers of US operators.
While unsophisticated, this malware is interesting as it is delivered using SMS and is purporting to be a MMS message. We’ve seen this specific behaviour before in Russia in 2013. And as we’ve reported on before, the normal propagation method for malware using SMS is via worms.
The SMS message sent contained links to an APK file that asked the subscriber to click on a link and view ‘a new MMS’ that was waiting for them:

We inspected the file and found that the APK is packaged using the DroidJack framework. This framework of malware is unique to Android devices and allows hackers to remotely control or monitor the host phone; surveilling data traffic, eavesdropping on phone conversations or hijacking a phone’s camera.
It’s interesting to note that packaging this malware through DroidJack is a very straightforward process, with limited technical skills required. An attacker could easily deploy this by following a tutorial on the DroidJack website.
It’s interesting to note that packaging this malware through DroidJack is a very straightforward process, with limited technical skills required. An attacker could easily deploy this by following a tutorial on the DroidJack website.
And even more noteworthy is that, unlike most malware attacks, the author didn’t make any efforts to hide the malware. In comparison to previous attacks, where the attacker injects the malware into a legitimate application to make the user believe it’s a normal app, the attacker chose not to do this:

They disguised this sample as ‘MMSdisplay’.

This malware packages the standard functions of DroidJack – which are all listed on their website – and include extracting data, uploading executables, recording phone calls, obtaining detailed device information, reading WhatsApp messages and making the app irremovable even after a factory reset.
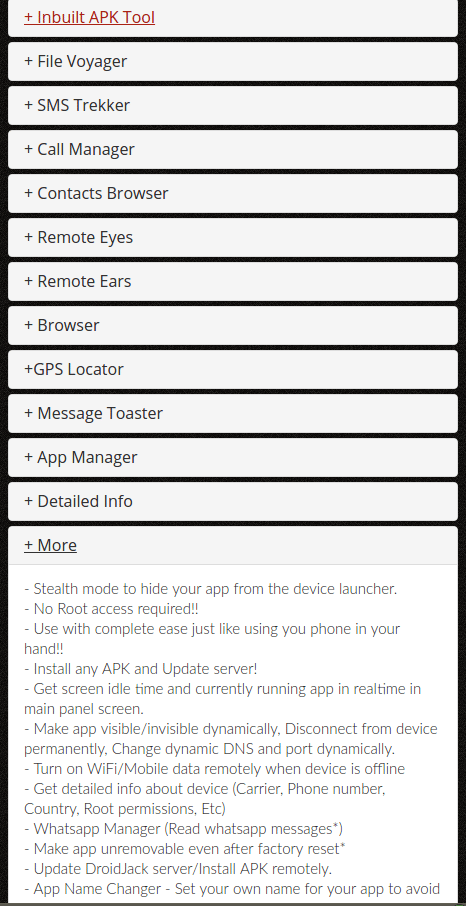
Droidjack uses Kryonet library to implement the communication between the infected device and the Command and Control (C&C) server. The sample we have configures to use andro1[….]ddns.net:1337 as the Command and Control server. All the setup can be through the UI, as explained in demo during the tutorial.

Simple, but persistent.
This is not the first time the attacker has attempted to exploit mobile users. We observed the same Twilio number sending PayPal phishing spam to North American subscribers, with the phishing website tracked to be hosted at the same location as the malware.
Our research shows us that this PayPal phishing scam is related to a campaign which has been active since January:

Both end links redirect to a landing page that encourages victims to provide their PayPal login details:

The OTT-portunity
We’ve recently reported on an increase in spam messages coming from OTT accounts, as criminals are already using this bearer to send the majority of spam in North America. Earlier this year we blocked several hundred thousand Craigslist-related SMS spam messages – with the vast majority of these phishing messages originating from OTT or VoIP carriers – and the majority of all spam blocked by us in recent months came from OTT carriers using SMS services.
We can see that as criminals enter into new bearers, the drive to exploit the unknown is very real. With the (limited) success of criminals sending spam through OTT carriers, we could be seeing a move by malware authors to follow suit and try their luck.
As previously mentioned, we typically see malware being distributed by infected handsets – not via a SMS from OTT carrier accounts. Given the industry evolution, this change in attack method is not surprising.
Smart ≠ Sophisticated
While we often demonstrate the increasing sophistication and complexity of attacks on mobile networks, it’s important to remember that a simple attack can also be a success for the attacker. As security controls become tighter and mobile operators work to identify and block attacks on mobile networks, bad actors are using a variety of methods and moving to different bearers.
With threats migrating to new messaging channels, we’ll continue to see hackers attempting new (and old) exploitation methods – and OTT carriers are no different.
AdaptiveMobile is blocking this attack for our customers. We recommend that mobile users exercise caution when opening messages from unknown senders and do not click on a link if you do not trust the contents.
md5sum 538c4779f56678b4b93bfff8b2f7e3e7
sha1sum a6cd14a424708c2fa2c5bf838fe4682a4554b522
sha256sum 7d0249e2c0f5286441eb4fba57451aeeb5ab2778bfb0cc2758e972a43603a670
Source:https://www.adaptivemobile.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











