Next time a site wants your personal info, remember the ClixSense debacle. Plaintext passwords, usernames, e-mail addresses, and a wealth of other personal information has been published for more than 2.2 million people who created accounts with ClixSense, a site that claims to pay users for viewing ads and completing online surveys. The people who dumped it say they’re selling data for another 4.4 million accounts.
Troy Hunt, operator of the breach notification service Have I Been Pwned?, said he reviewed the file and concluded it almost certainly contains data taken from ClixSense. Besides unhashed passwords and e-mail addresses, the dump includes users’ dates of birth, sex, first and last names, home addresses, IP addresses, account balances, and payment histories.
A post advertising the leaked data said it was only a sample of personal information taken from a compromised database of more than 6.6 million ClixSense user accounts. The post said that the larger, unpublished data set also includes e-mails and was being sold for an undisclosed price. While the message posted over the weekend to PasteBin.com has since been removed, the two sample database files remained active at the time this post was being prepared. The Pastebin post, which was published on Saturday and taken down a day or two later, read in part:
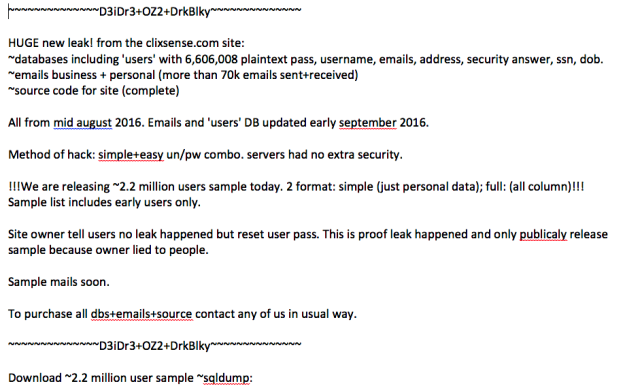
HUGE new leak! from the clixsense.com site:
~databases including ‘users’ with 6,606,008 plaintext pass, username, emails, address, security answer, ssn, dob.
~emails business + personal (more than 70k emails sent+received)
~source code for site (complete)
The post went on to say that most of the compromised personal information was current as of last month and that e-mail and some of the other data was last updated earlier this month. If true, that would make the data much more valuable than many of the recent leaks such as theone from Dropbox, which dates back to 2012.
Thoroughly hacked
In a private message, ClixSense owner Jim Grago confirmed that his company’s servers, domain name system settings, and e-mail were all completely compromised. He also confirmed that the database contained entries for about 6.6 million accounts, adding further credence to claims attackers made in the now-deleted Pastebin post. In the message, Grago wrote: This all started last Sunday, September 4th about 5am EST when my lead developer called me and said ClixSense was redirecting to a gay porn site. The hackers were able to take over our dns and setup the redirection. On Monday (Labor day) they were able to hack into our hosting provider and turned off all of our servers, hacked into our Microsoft Exchange server and changed the passwords on all of our email accounts. On Tuesday they were able to gain access to a server that was directly connected to our database server and get a copy of our users table.
Grago also said ClixSense issued a mandatory password reset for all users shortly after the trouble began. An announcement on the ClixSense website said the database compromise involved an old server that was no longer in use but still had access to the database server. The old server has since been terminated. The announcement made no mention of the personal information circulating online or what precautions users should take now that such a vast amount of their personal information has gone public.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











