Research published last week by the Cyber-Security Research Center at the Ben-Gurion University of the Negev in Israel reveals that it only takes about 6,000 smartphones infected with malware to launch a DDoS attack capable of shutting down 911 emergency services in a US state.
To cripple 911 services across the entire US, attackers would need a botnet with as little as 200,000 devices, which is a pretty large number, but something that nation-state attackers would be willing to invest and create.
Researchers say that in its current state, the 911 emergency system has no defenses to protect itself against such attacks.
Mobile operators are required by current FCC regulations to forward any 911 call to emergency call centers, called public safety answering points (PSAP), regardless of the caller’s IMSI or IMEI identifiers. There is currently no system in place to blacklist repeated callers.
Nation-states could build huge botnets
During their investigation, Israeli researchers said that attacks can come from mobile phones infected with malware belonging to legitimate users, or from special laboratories, specifically built to carry out attacks. The cost of a botnet of 6,000 smartphones capable of launching attacks would be around $100,000, researchers estimated.
To scale the number to 200,000 smartphones, an attacker would have to invest between $3.3 and $3.4 million to build a DDoS cannon capable of shutting down the US 911 system and causing havoc around the country.
Taking into account that countries invest billions of dollars in military budgets, the initial investment is a low figure, and threat actors could build bigger botnets if they chose to, for better results.
Attacks can be anonymous, impossible to detect
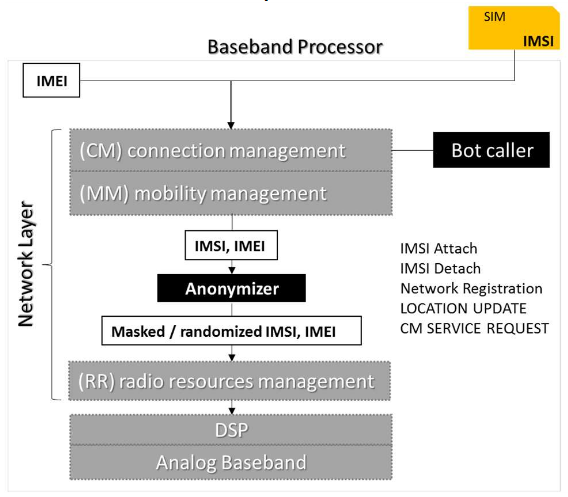
Researchers that worked on the attack methodology also say that attacks can be carried out anonymously by using malware embedded in the phone’s baseband firmware.
The malware would randomize the phone’s IMSI (SIM card-related) and IMEI (phone-related) identifiers for each attack, so mobile operators would not be able to blacklist the callers at their level. If 911 call centers implement a blacklisting system in the future, these randomized identifiers would be able to bypass them as well.
To make the attack even more powerful, researchers configured the malware they developed for their own tests to dial the 911 number continually. As soon as the previous connection was closed, the malware would start another.
The malware would also insert audio inside the call, in an attempt to keep 911 operators busy as much as possible and deny service for real users.
Full 911 shutdown is possible with enough determination and mobile bots
Tests with the 6,000 mobile botnet revealed that the DDoS attack blocked 911 access to 50 percent of users inside a state. If the attacker would want a complete service shutdown with a 90 percent denial rate, then the botnet’s size would have to be increased to 50,000.
911 DDoS attacks on the whole US level with the 200,000 botnet yielded a 33.3 percent denial rate for users across the country.
The 911 emergency system, according to the Department of Homeland Security, is one of the 16 critical services across the US, which should be protected and safeguarded at all times, not just in times of war.
Defensive measures need to be taken since mobile botnets have been spotted in the wild by CloudFlare.In September 2015, a mobile botnet of 650,000 smartphones, mostly located in China, launched classic HTTP DDoS attacks against local websites.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











