HDDCryptor, sometimes spelled HDD Cryptor and also identified as Mamba, is a new ransomware variant that rewrites a computer’s MBR (Master Boot Record) boot sectors and locks users out of their PCs. While we might hurry to classify this as a Petya clone, HDDCryptor predates both Petya and Satana, being spotted on the Bleeping Computer forums at the end of January this year.
The ransomware was never the focus point of a massive distribution campaign, which is why it never garnered any attention from security vendors and independent security researchers.
A revamped HDDCryptor returns
A surge of activity that appears to have started in the last days of August has brought HDDCryptor in the spotlight, with some research now available from Renato Marinho of Morphus Labs, and the Trend Micro team.
Trend Micro says the ransomware reaches computers after users download files from malicious websites. Crooks drop the malicious binary on the computer directly, or through an intermediary payload downloaded at a later stage.
This initial binary is named using a random three-digit number in the form of 123.exe. A hybrid analysisof the file doesn’t reveal too many initial clues.
When executed this initial binary drops the following files in a folder on the computer’s system root:
dccon.exe (used to encrypt the disk drive)
dcrypt.exe
dcrypt.sys
log_file.txt (log of the malware’s activities)
Mount.exe (scans mapped drives and encrypts files stored on them)
netpass.exe (used to scan for previously accessed network folders)
netuse.txt (used to store information about mapped network drives)
netpass.txt (used to store user passwords)
Two of these files are freely available and legitimate tools. Netpass.exe is a free network password recovery tool, and dcrypt.exe is the executable for DiskCryptor, an open source disk encryption utility.
To gain boot persistence, HDDCryptor creates a new user called “mythbusters” with password “123456,” and also adds a new service called “DefragmentService,” that runs at every boot. This service calls the ransomware’s original binary (the three-digit exe file).
The netpass.exe tool is executed first to scan for previously accessed network folders and extract credentials. The information on these network drives is stored in two local text files, one holding details about the mapped drives, and any credentials, if present.
HDDCryptor encrypts files and overwrites the MBRs
The infection process continues with dccon.exe and Mount.exe. Both these files use DiskCryptor to encrypt the user’s files. Dccon.exe encrypts files on the user’s hard drive, while Mount.exe encrypts files on all mapped network drives, even the ones currently disconnected, but that remained physically reachable.
After the encryption ends, the ransomware rewrites all the MBRs for all hard drive partitions with a custom boot loader. It then reboots the user’s computer without user interaction and shows the following message.
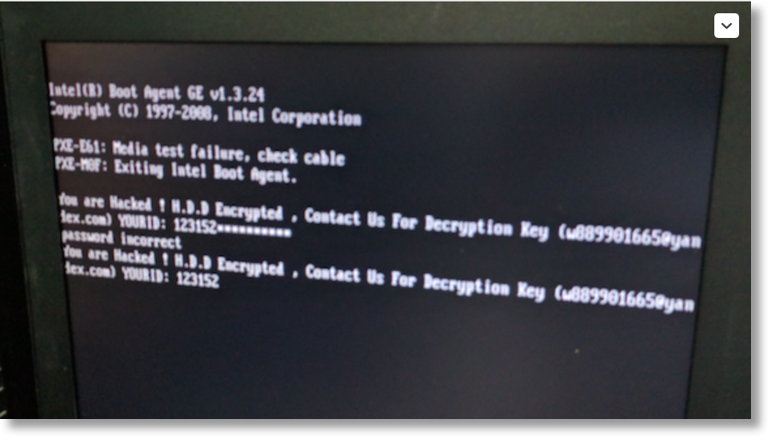
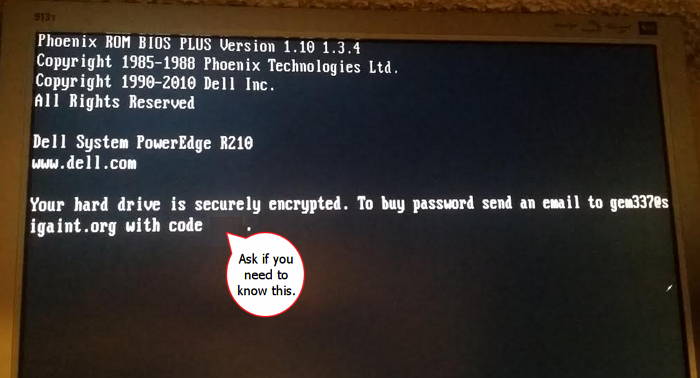
The January version of this ransomware showed the following message, using a different wording and another email address.
 a
aThe January version used four-digit victim IDs, while the August-September infections now use a six-digit identifier instead.
In January, the ransomware authors were asking for the equivalent of $700 in Bitcoin, as one of the victims that posted on Bleeping Computer revealed. The full email ransom demand is below:
Here are our standard payment instructions.
Our bitcoin wallet address is (removed)
$700 is approx. 1.0520 BTC according to current exchange rate.
In case you have no prior experience with Bitcoin (and can't find
someone who has - which is the best option) here's a summary on
different ways to buy bitcoin:
https://en.bitcoin.it/wiki/Buying_Bitcoins_%28the_newbie_version%29
For example, you can buy bitcoins on coinbase.com (using your bank
account), localbitcoins.com (multiple payment methods, depending on
vendor), bitquick.co (cash deposit in local bank, seems to work pretty
fast but we have no personal experience with them) or virwox.com (they
accept cards and paypal, and on virwox.info you can find a tutorial on
buying bitcoins there).
Please note that for security reasons some websites will delay payment
for up to 48 hours (that's true for purchasing on virwox with paypal) so
please pay attention to terms of service. We won't be able to confirm
your transaction and send you the password during that delay period.
In our experience your best chance to make the transfer quickly is
to find an online seller with good reviews on localbitcoins.com. If you
use cash deposit to pay that seller your transaction should only take a
few hours. Also vendors can be really helpful on that website.
Alternatively you can look up bitcoin ATMs in your area - their fee is
usually a bit higher but that's one of the fastest ways to buy bitcoins.
For amounts up to $300 you can use circle.com - it allows to send money
from credit and debit cards almost instantly. You can also break up
bigger amounts and make several payments from different accounts if you
find it convenient.
After you purchase $700 worth of bitcoins you can just send them to our
bitcoin wallet directly from the website you've chosen - this way you
won't have to install bitcoin software, manage your own wallet etc. If
you find it difficult to transfer the indicated amount in a single
transaction you can break up the sum and make several transactions to
the same bitcoin address (possibly using different methods of purchasing
bitcoins).
After that we'll send you the password that'll let you boot Windows and
further instruction on permanently decrypting hard drives. We'll also
tell how we got in so you can fix it and prevent future incidents.The ransom note received by Marinho in September is less verbose and less helpful than the one from January. The crook is now also asking for 1 Bitcoin (~$600).
Your HDD Encrypted By AES 2048Bit
send 1BTC Per HOST to My Bitcoin Wallet , then we give you Decryption key For Your Server HDD!!
My Bitcoin Wallet Address : (removed)
We Only Accept Bitcoin , it’s So easy!
you can use Brokers to exchange your money to BTC ASAP
it's Fast way!
Here:
https://localbitcoins.com/
if You Don't Have a Account in Bitcoin , Read it First :
https://bitcoin.org/en/getting-started
bitcoin Market :
https://blockchain.info/
https://www.okcoin.com/
https://www.coinbase.com/
https://bitcoinwallet.com/
-----------At the time of writing, the Bitcoin wallet address associated with the September campaign shows that four victims have paid so far.
After a user pays the ransom, he receives a password, which he has to enter in the pre-boot screen.
Most of the research on this infection has been done by Marinho, who says that his company was called in to investigate and fix a massive infection at a multi-national company that affected computers in its Brazil, India, and US subsidiaries.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











