Following an investigation by Pen Test Partners, British Telecom (BT) has released a firmware upgrade for their popular range of Wi-Fi extenders.
The investigation uncovered vulnerabilities within the firmware when left the device exposed to possible XSS (Cross Site Scripting) Exploits as well as the ability to change the user’s password without notification.
By combining these flaws it was proved possible to grab the victim’s WPA passphrase following tricking them into visiting a maliciously crafted website from their home network.
BT was quick to offer an upgrade, available here, which resolves the issues. The telecommunications giant were also quick to credit Pen Test Partners, thanking them for the discovery:
“We are grateful to Pen Test Partners for alerting us to this issue. We have been working to address this potential weakness and issued an update which corrected the problem in August 2016. We are not aware of any cases where customers have suffered any issues. Customers should ensure they download the firmware update from the BT website.”
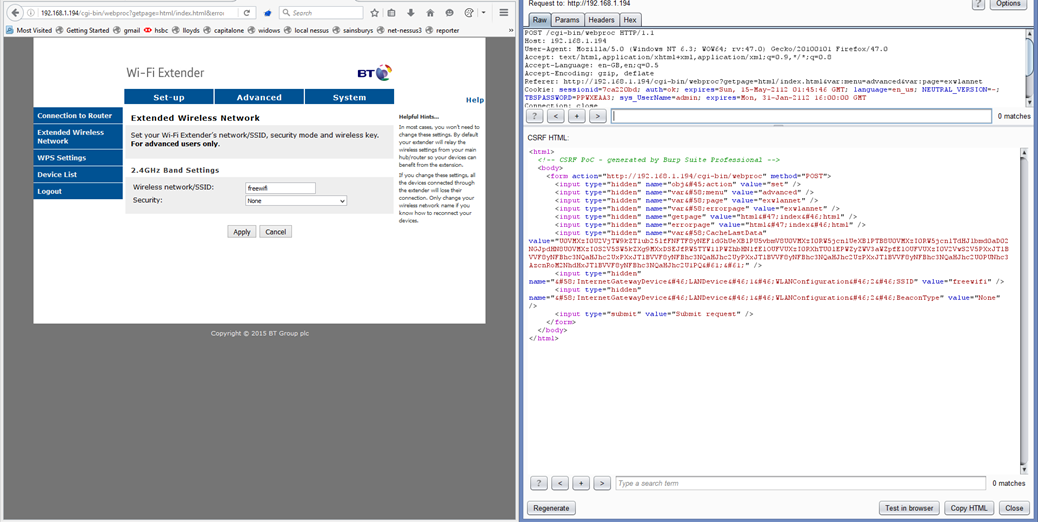
The report detailed that a malformed JavaScript could be created and spammed over the local network (if the IP of the extender was unknown), which could be crafted to change the password without ever seeking verification of the previous password, as is standard in many applications.
The var:errorpage parameter within the configuration was also found to be vulnerable, this time to XSS. The device also didn’t validate input or its HTML encoding when it rewrites changes back out to the web page.
Altering cookie parameters also allowed unauthenticated users to glean username and passwords directly.
“The var:errorpage parameter seems to be vulnerable to reflected cross-site scripting because it is not correctly validated on input, nor HTML-encoded when it is written out to the web page again.
Example:

Also, if we try it with document[.]cookie instead of ‘1’, we get to see the username and password.” states thereport from Pen Test Partners.
Pen Test Partners combined these vulnerabilities, grabbed the cookies and ended up with the victim’s NAT IP, admin password, SSID as well as their Pre-Shared Key.
The popularity of BT Wi-Fi extenders, as well as, the extent of the vulnerabilities and relative ease of performing this exploit means that all home users without version 1.1.8, if they haven’t done so, should stop what they’re doing, especially if it’s online, and upgrade immediately.
Source:https://securityaffairs.co/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











