Kaspersky posted a great article about their TeamXrat Ransomware analysis and how they were able to create a decryptor for its victims. Reported back in mid September in our forums, I and other security researchers were never able to find an actual sample of the malware. It turns out that this was because the ransomware is being manually installed via hacked RDP services and then manually cleaned up after the installation is finished.
Installed via Hacked Remote Desktop Services
According to Kaspersky, this ransomware, which they have named the Xpan Ransomware, is created by a Brazillian cybergang that goes by the name TeamXrat or CorporacaoXRat. This group targets servers and computers running Remote Desktop Services and attempt to brute force passwords to gain access. Once they are able to gain access, they will manually install the ransomware and encrypt the victims data.
Depending on the version of the ransomware, when the files are encrypted they will have the ___xratteamLucked or the ____xratteamLucked extension appended to the filenames. A ransom note will also be created called Como descriptografar os seus arquivos.txt. This file name translates from Portuguese to English as How to decrypt your files.
Below is an example of this ransom note:
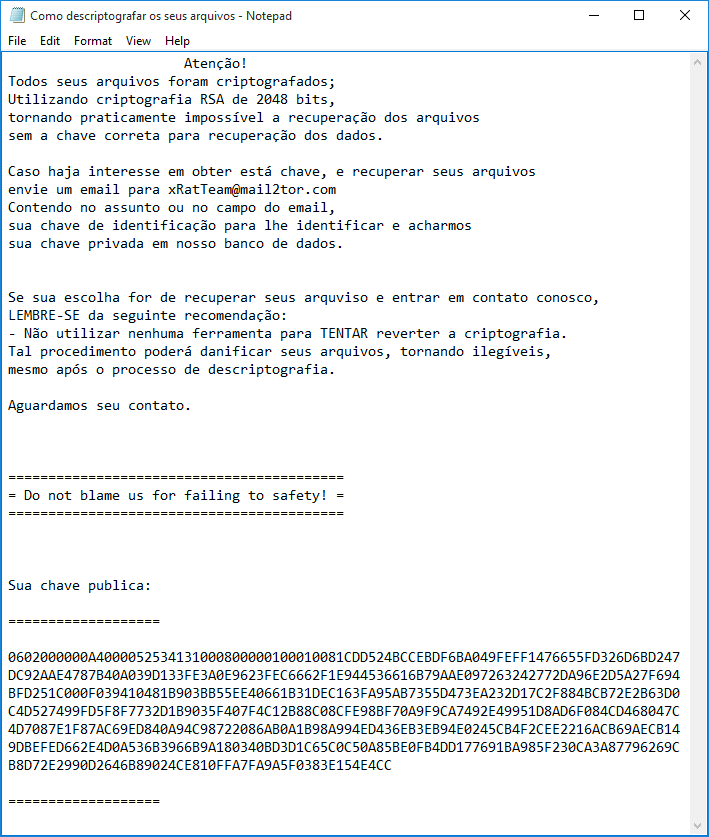
Source: TeamXRat: Brazilian cybercrime meets ransomware
The ransomware will also change the desktop wallpaper to the following image.
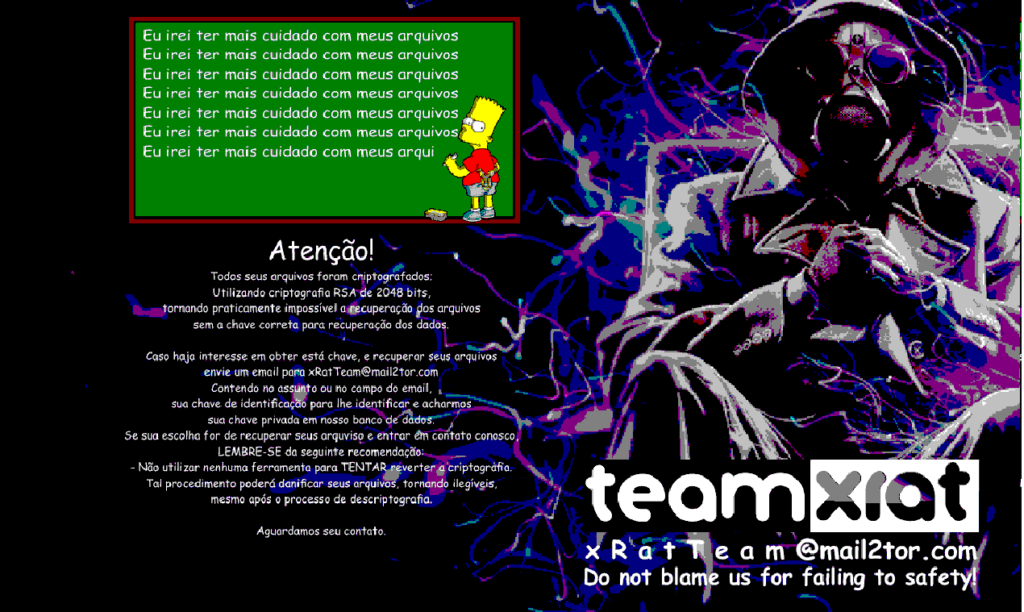
Victim’s are then asked to email the ransomware developers in order to get payment instructions, where the developers will ask for a 1 bitcoin ransom payment. Emails that Kaspersky report have been associated with this ransomware are xRatTeam@mail2tor.com and corporacaoxrat@mail2tor.com.
Kaspersky to the Rescue
The good news is that Kaspersky was able to crack the encryption being used by the Xpan Ransomware / TeamXrat Ransomware. For those who have been affected by this ransomware and whose encrypted files end with the ___xratteamLucked (3 underscores) and the____xratteamLucked (4 underscores) extension, do not pay the ransom! Instead you can contact Kaspersky at their support page.
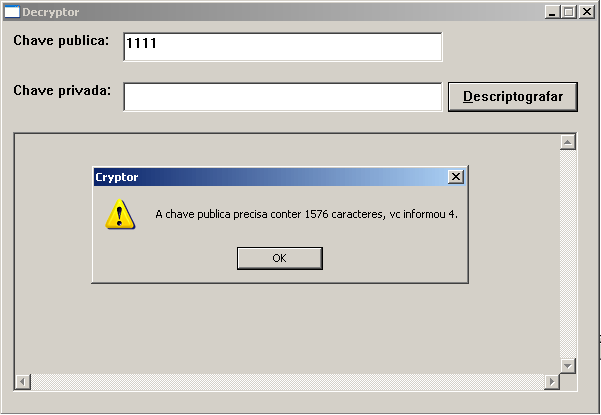
Source: TeamXRat: Brazilian cybercrime meets ransomware
It is unknown if Kaspersky is charging for this service, but in the past they have released their decryptors for free. My guess is that they are not making the decryptor publicly available to prevent TeamXrat from learning the weakness in their encryption algorithm.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











