Late last week, a new version of Cerber Ransomware was released that included some new features. The most notable change is the switch from the static .Cerber3extension for encrypted files to a random 4 character extension, the use of a HTA file as the ransom note, and the termination of various database processes before encryption.
With this version, when a victim’s files are encrypted, not only will the filename be scrambled, but the extension will be replaced as well. This means that a file that was previously encrypted as 5NgPiSr5zo.cerber3, would now be encrypted to a name like 1xQHJgozZM.b71c.
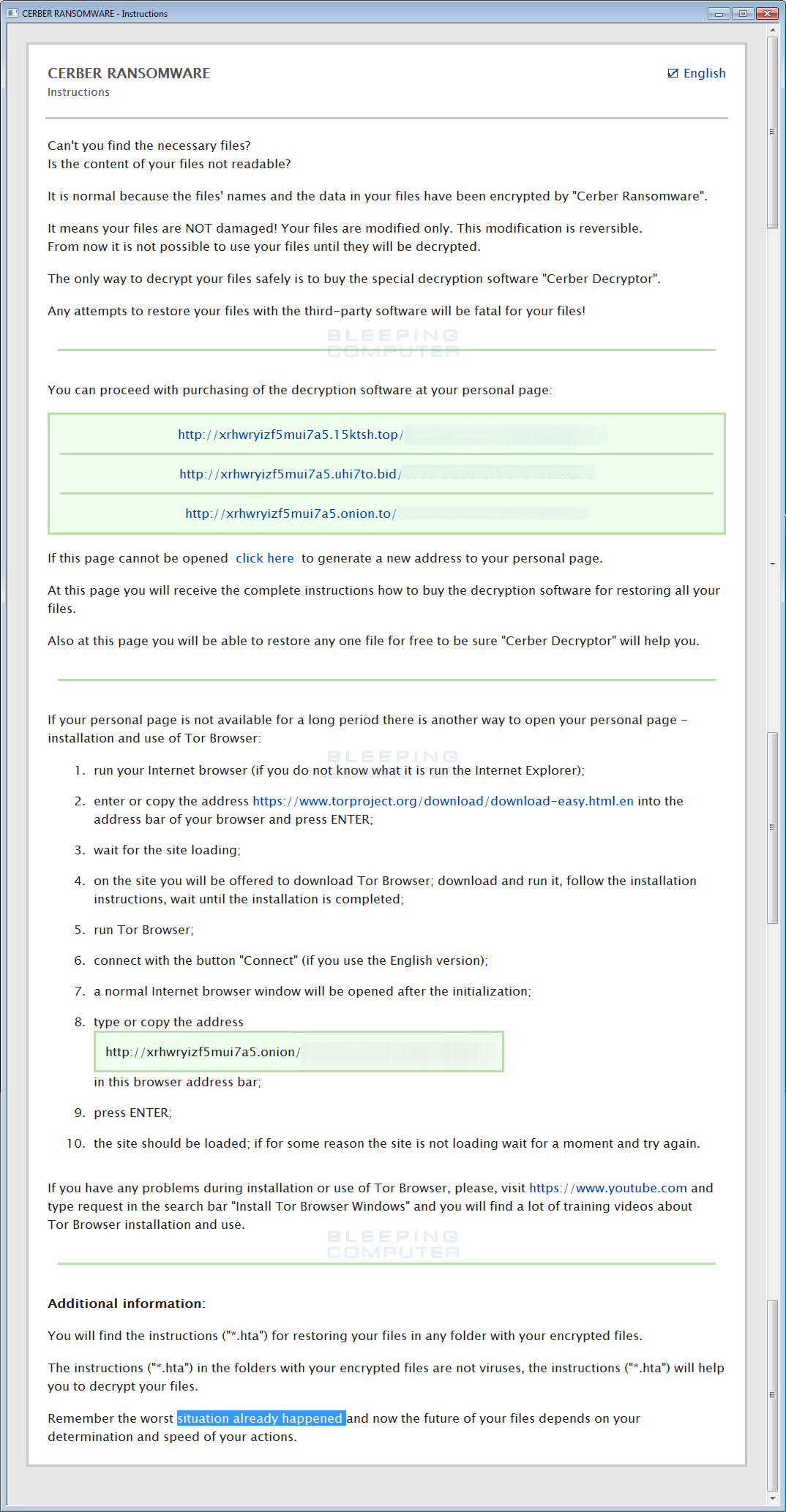
This version also includes a new ransom note called README.hta. When launched, the ransom note will appear in an application Window and display the normal ransom note. An example of the README.hta file can be found below.
According to security researcher BloodDolly, this update also includes the addition of new database processes that are closed by the close_process directive in Cerber’s configuration. This directive tells Cerber to terminate certain processes before encryption begins. The directive and the current list of processes being terminated are:
"close_process":
{
"close_process":1,
"process":["msftesql.exe","sqlagent.exe","sqlbrowser.exe","sqlservr.exe","sqlwriter.exe","oracle.exe","ocssd.exe","dbsnmp.exe","synctime.exe","mydesktopqos.exe","agntsvc.exeisqlplussvc.exe","xfssvccon.exe","mydesktopservice.exe","ocautoupds.exe","agntsvc.exeagntsvc.exe","agntsvc.exeencsvc.exe","firefoxconfig.exe","tbirdconfig.exe","ocomm.exe","mysqld.exe","mysqld-nt.exe","mysqld-opt.exe","dbeng50.exe","sqbcoreservice.exe"]
},
These processes are closed in order to enable the processes’s data files to be encrypted. If the processes are running during encryption, then the corresponding data files may not be accessible for encryption by Cerber.
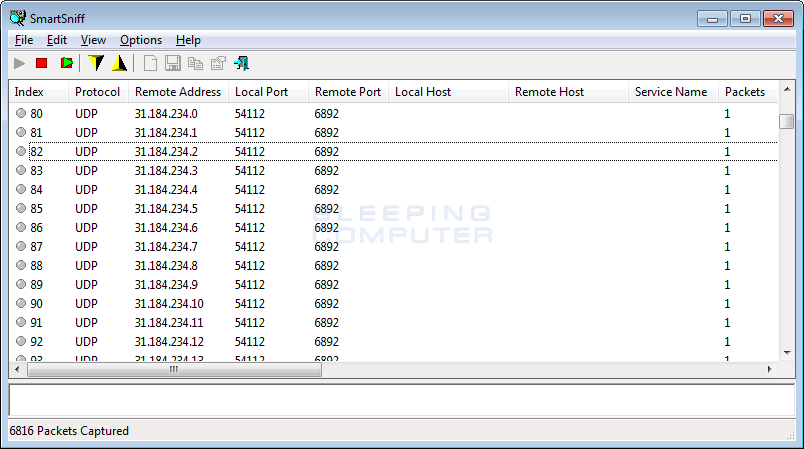
Finally, this version of Cerber Ransomware continues to send UDP packets to the 31.184.234.0/23 range for statistical purposes.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











