Communications failure leads to zero day, late patch, natch. Millions of do-it-yourself websites built with the Wix web maker were at risk of hijack thanks to a brief zero day DOM-based cross-site scripting vulnerability.
Wix boasts some 87 million users, among them two million paying subscribers.
Contrast Security researcher Matt Austin (@mattaustin) dug up the flaw he rates as severe, and attempted to get Wix to patch it under quiet private disclosure since October.
He says he heard nothing back from the web firm other than an initial receipt of the disclosure on 14 October after three subsequent update requests.
Checks appear to confirm the holes have been quietly shuttered after Austin’s public disclosure. Wix has been contacted for comment.
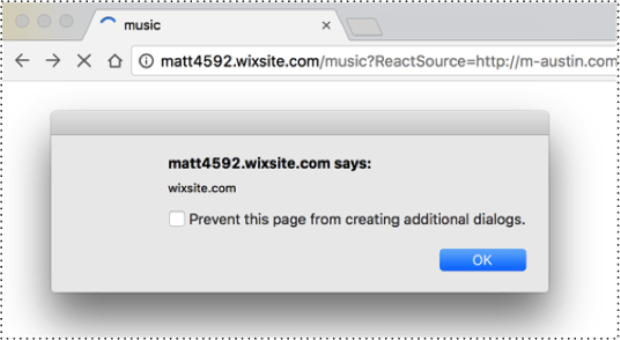
“Wix.com has a severe DOM cross-site scripting vulnerability that allows an attacker complete control over any website hosted at Wix,” Austin says in his disclosure.
“Simply by adding a single parameter to any site created on Wix, the attacker can cause their JavaScript to be loaded and run as part of the target website.
“Administrator control of a wix.com site could be used to widely distribute malware, create a dynamic, distributed, browser-based botnet, mine cryptocurrency, and otherwise generally control the content of the site as well as the users who use it.”
More attack scenarios awaited attackers who either found the flaw before Austin or spotted his disclosure before Wix could patch it.
Austin says attackers could have:
- Changed content of a hosted website for targeted users;
- Challenged the user for their Wix username and password;
- Challenged the user for their Facebook or Twitter username and password;
- Attempted to trick users of the website into downloading malware and executing it;
- Generated ad revenue by inserting ads into website pages;
- Spoofed bank web pages and attempted to have users log in;
- Make it difficult or impossible to find and delete the infection, and,
- Create new website administrator accounts.
Austin supplied then working proof-of-concept links showing the DOM cross-site scripting in action against Wix template sites.
He also provided five steps required for attackers to spin the vulnerability into a worm to hit scores of sites.
The public disclosure, while made sooner than the fastest industry standard 30 day bug fix window, should serve as a reminder to all businesses with an online presence to have a process in place to handle vulnerability disclosures. This should preferably include a nominated staffer to handle the disclosures, along with security@* email address which is visible on the business website.
Source:https://www.theregister.co.uk/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.