A new spam wave posing as emailed fax messages is delivering a malware downloader that fetches and installs a ransomware family known as PClock, a CryptoLocker clone.
The ransomware, detected by Microsoft as Ransom:Win32/WinPlock.B or WinPlock, is more commonly referred to under the name of PClock and has been going around since January 2015, when users first complained about it on the Bleeping Computer forums.
Emsisoft security researcher Fabian Wosar was able to create a decrypter for the earlier versions that allowed users to unlock their files for free.
By May 2015, the PClock team updated their code and broke the decrypter. After that point, PClock victims could only restore their files from backup files or by paying the ransom.
PClock resurfaces with new spam wave
Since then, the number of infections with PClock has been low but steady. Microsoft’s security team recently picked up a spike in activity from the group’s operators.
In their most recent spam campaign, the ransomware’s creators are using emails disguised as fax messages, using a subject such as “PLEASE READ YOUR FAX T6931.”
The title is boring and mundane, but the email contains a file named “Criminal case against you,” which might get some users’ attention.
PClock installed via Crimace trojan
This RAR archive contains a WSF file. When users download and open the archive, and execute the WSF file, a JScript function starts a series of operations that download and install a malware known as Crimace, detected as TrojanDownloader:JS/Crimace.A.
This threat is a malware downloader, a trojan that connects to an online server and downloads and runs other malware. In this case, it was PClock.
If we take a look at the screenshots posted on the Bleeping Computer forums in January 2015, and the screenshots taken by Microsoft, we see that PClock hasn’t evolved, at least visually, at all.
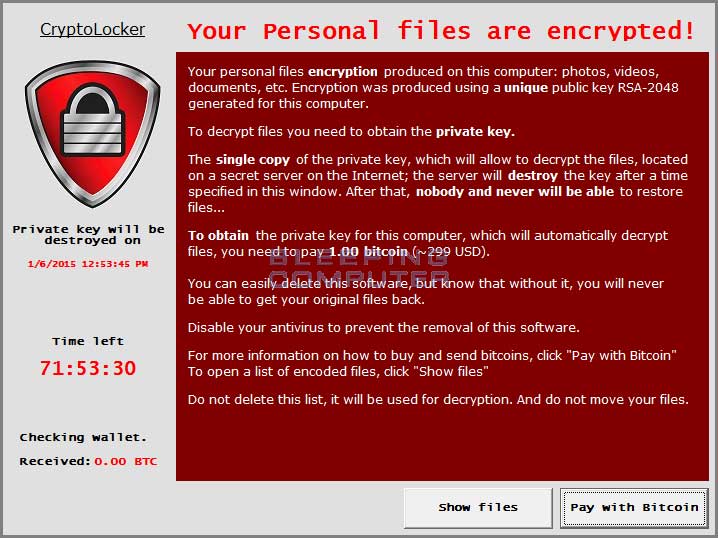
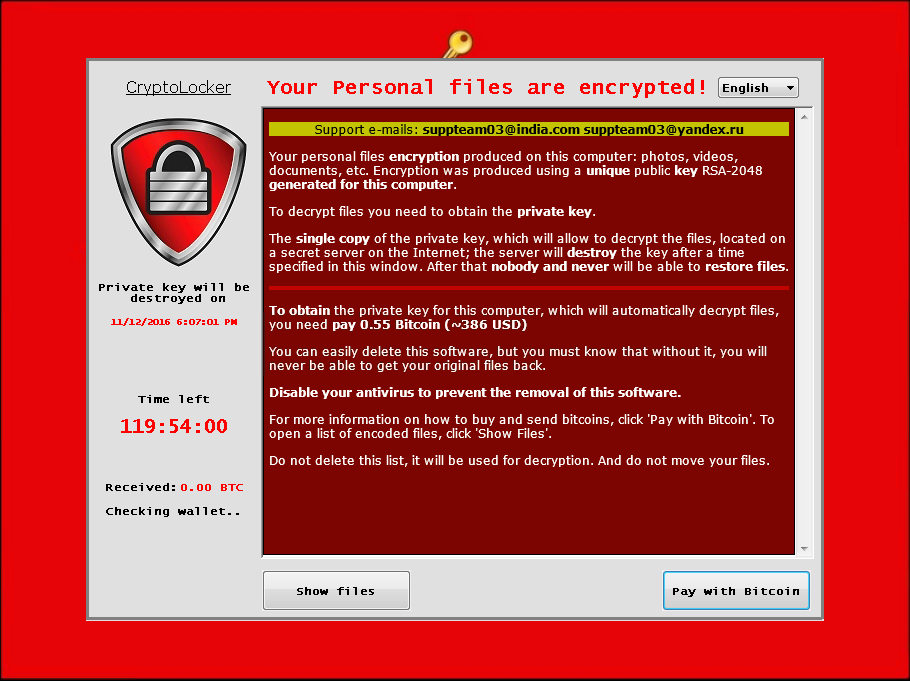
The ransomware has remained at the same level of sophistication, still posing as a CryptoLocker clone, even if other more dangerous ransomware families have emerged in the meantime.
PClock still an entry-level operation
Furthermore, PClock’s operators have yet to figure out how to host a decryption service on the Dark Web, the standard method for dealing with decryption operations, preferred by most high-end ransomware threats.
After almost two years in the wild, PClock has remained an entry-level operation, requiring victims to get in contact with PClock’s authors via email, a cumbersome and time-consuming task.
The only thing that has changed is the number of targeted files. Initial PClock variants targeted only 100+ file types for encryption, while the most recent variant targets a whopping 2,630 file types.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











