Scientists and medical professionals published a research paper in which they detailed a simple and inexpensive approach to creating a device that can be used to hack Implantable Cardiac Defibrillators (ICDs), also referred to as pacemakers.
For their research, the team hacked ten pacemakers with successful results. The researchers said they were able to drain the device’s battery, steal information stored or sent from the pacemaker, and more dangerously, send commands to the ICD.
To be able to do this, researchers created a test rig out of inexpensive commercial off-the-shelf equipment. The rig included a Universal Serial Radio Peripheral (USRP), a data acquisition system (DAQ), and a few antennas, portrayed below.
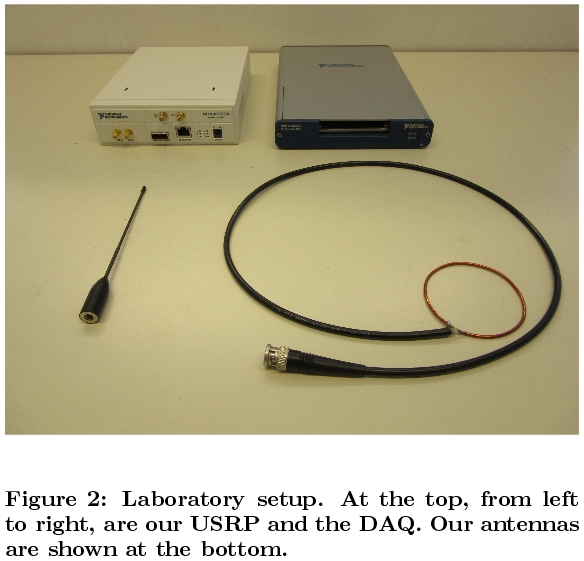
Researchers said they used a simple “black box testing” approach in the beginning, even managing to hack a pacemaker without reverse engineering its protocol. The rest of the devices protected their data and communications using a simple XOR algorithm.
Waking up the ICD is hard, but the rest is easy
The biggest hurdle the researchers faced was related to the fact that each ICD/pacemaker would first need to be activated before being capable of receiving a command.
This step implied close contact with the patient, with the attacker having to bring a magnetic programming head inches away from the patient’s skin to wake up the ICD. If the attacker couldn’t afford this step, he could just wait for the patient or a doctor to wake the device on their own.
Once out of sleep mode, the attack rig can be used to send periodic pings to the ICD and keep it in a constant “on” state. These pings also drain the ICD’s battery.
With their rig, the attack distance was two to five meters, but researchers said that attackers could use more powerful antennas to expand the rig’s reach.
Attacks can have lethal consequences
Technically, ICDs are more advanced than pacemakers, despite being referred to as pacemakers by some users. Just like a pacemaker, ICDs can send small electrical signals to a patient’s heart and regulate its activity. Additionally, ICDs are also capable of sending strong electrical signals, like a defibrillator, in the case of an emergency.
The research team said that an attacker could use the rig they’ve created to send commands to affected ICDs. Consequences are easy to imagine.
Researchers said they’d notified ICD vendors about the flaws they’ve found. The research paper, titled “On the (in)security of the Latest Generation Implantable Cardiac Defibrillators and How to Secure Them” is available online.
All “smart” medical devices are easy to hack
At the 32nd Chaos Communication Congress (32C3) held in Hamburg, Germany at the end of 2015, Marie Moe, a former member of Norway’s Computer Emergency Response Team, warned about the dangers of hackable pacemakers. Moe, herself, was using one such device.
A 2015 study by Independent Security Evaluators (ISE) has also shown the low level of skills an attacker needs to hack modern “smart” hospitals nowadays.
In October, Rapid7 security researcher Jay Radcliffe said he discovered that OneTouch Ping insulin pumps made by Animas, a Johnson & Johnson subsidiary, could be hacked and used to set off hypoglycemic reactions.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











