Security researchers find easy to exploit vulnerability. North Korea is one of those countries whose governments pushed for the migration to a domestically-developed operating system that’s supposed to be more secure than foreign software, such as Microsoft’s own Windows, which they claim can always include backdoors and malicious code.
This is how North Korea ended up developing Red Star OS, a Linux-based operating system that’s supposed to be fully hackerproof.
But as it turns out, Red Star OS isn’t exactly as secure as North Korean leader Kim Jong-un wanted it to be, as a group of security researchers managed to break into the operating system using just a link.
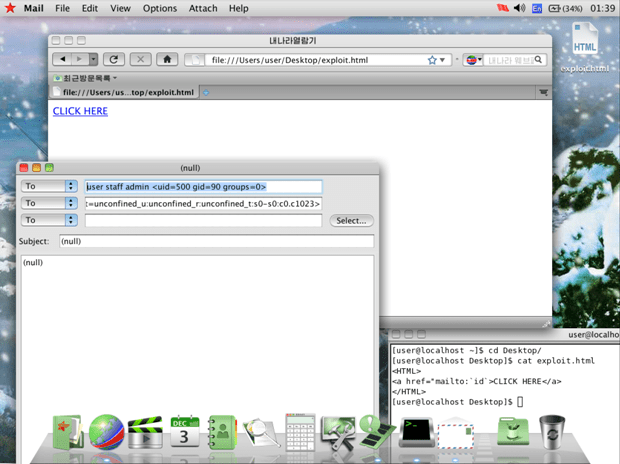
Security firm Hacker House discovered a vulnerability in the operating system that makes it possible for a potential attacker to gain remote access to a computer running Red Star OS by convincing a user to open a malicious link.
Full control over computers running Red Star OS
The researchers explain that this security flaw can be used to install malware or exploit computers running the operating system, and it’s all possible through the browser that ships with Red Star and called Naenara (which is based on the more popular Mozilla Firefox). The security firm reveals how an exploit could work:
“Whilst probing for vulnerabilities it was noticed that registered URL handlers were passed to a command line utility “/usr/bin/nnrurlshow”. This application (aside from having null ptr de-refs and other cute bugs) takes URI arguments for registered URI handlers when handling application requests such as “mailto” and “cal”. Naenara doesn’t sanitize the command line when handling these URI argument requests and as such you can trivially obtain code execution by passing malformed links to the nnrurlshow binary.”
Red Star OS is a homegrown operating system that gives North Korean authorities more control over the computers that install it, providing not only what they described as uncompromised security, but also with tools that help track files that are being used on a machine running it.
For example, Red Star OS is capable of watermarking documents, files, and even USB flash drives that are connected to a computer, so if the government wants, every bit of data can be traced easily.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.