Last week, the Swiss Governmental Computer Emergency Response Team (GovCERT), together with SWITCH, the registrar of .ch top-level domain names, have taken action against the Tofsee malware botnet that was abusing Swiss domains to host its dynamic command and control (C&C) servers.
Most of the work has been done by security experts working for GovCERT, who were able to crack the malware’s DGA, a dynamic algorithm that generates unique URLs every week, to which computers infected with the Tofsee malware connect to receive new instructions.
Tofsee, a malware used predominantly to send massive amounts of spam, needs its C&C server infrastructure to receive information on the new spam campaigns it needs to send out.
GovCERT cracks Tofsee DGA, blacklist all .ch domains
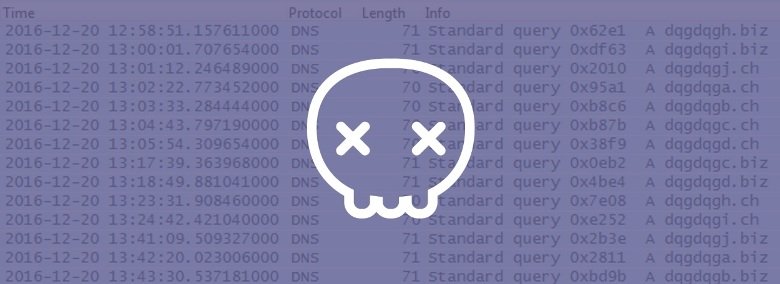
According to the GovCERT team, recent Tofsee variants generated 20 random domains each week, ten registered with .ch domains, and ten registered with .biz domains.
Researchers reverse-engineered the DGA (Domain Generation Algorithm) and were able to determine all the .biz and .ch domains to which the Tofsee malware would connect to receive new instructions in the next year.
GovCERT then contacted SWITCH, the local authority that controls .ch domain registrations, and together with the Registrar of Last Resort (RoLR) have created a blacklist that would prevent anyone from registering these domains.
Tofsee botnet crippled, but still alive
Because .biz domain registrations are spread across the world to different registrars, preventing the Tofsee gang from using these domains as C&C servers couldn’t be achieved.
Nevertheless, GovCERT researchers published the list of all .biz domains on their site, so security firms and ISPs can block traffic to these URLs. While the Tofsee botnet is still standing, GovCERT’s actions have severely crippled the botnet’s activity.
Because authorities weren’t able to coordinate a takedown of .biz domains, the Tofsee gang will still be able to push out an update for their malware, which will almost certainly switch to new domains for its C&C server architecture.
Tofsee, a relatively small malware botnet, first appeared in 2013 and has had a historical relation with the RIG exploit kit. In September 2016, Cisco Talos researchers noted an increase in activity from the Tofsee spam botnet, just when the RIG exploit kit was also becoming the top dog on the exploit kit market, following the deaths of the Angler and Nuclear exploits kits, and the passage of the Neutrino exploit kit into a closed-private state.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.