A cyber-crime infrastructure known in infosec circles as pseudo-Darkleech has been the source of many ransomware infections during the past year, either by malicious spam attachments or via automated attacks carried out via exploit kits.
pseudo-Darkleech is the name of a collection of hacked websites that host malicious scripts, secretly inserted in the source code of these sites by malicious actors.
The infected websites vary in nature and range from Drupal to WordPress, and various other CMS platforms. The only thing in common is the mode of operation, and the scripts injected on these sites, which places them under the control of the pseudo-Darkleech group.
pseudo-Darkleech employed to deliver traffic to exploit kits
This campaign has been on the radar of security researchers for years and has evolved from Darkleech, another infrastructure of hacked sites that crooks employ in a similar way, but using different exploitation routines and injected scripts.
pseudo-Darkleech appeared in late 2014 – early 2015, and consists of selecting random users that access the compromised websites, and loading hidden iframes in the background of their pages.
These iframes run source code from exploit kits that test the user’s browser for weaknesses. If the victim is deemed vulnerable, then an exploit soon follows, which takes hold on the user’s PC and then downloads a predetermined malware payload from the exploit kit’s servers.
pseudo-Darkleech campaigns have been very active in 2016, something that has been noticed by multiple security firms, such as Microsoft, Heimdal Security, Palo Alto Networks, and security researcher Brad Duncan from Malware-Traffic-Analysis.
According to multiple sources, pseudo-Darkleech has used multiple exploit kits to deliver various types of ransomware in the past year. A short summary is as follows:
- Jan 2016: Angler EK delivered CryptoWall ransomware
- Feb 2016: Angler EK delivered TeslaCrypt ransomware
- Apr 2016: Angler EK delivered CryptXXX ransomware
- Jun 2016: Neutrino EK delivered CryptXXX ransomware
- Aug 2016: Neutrino EK delivered CrypMIC ransomware
- Sep 2016: Rig EK delivered CrypMIC ransomware
- Oct 2016: Rig EK delivered Cerber ransomware
- Nov 2016: Rig EK delivered Cerber ransomware
- Dec 2016: Rig EK delivered Cerber ransomware
Just in the past two weeks alone, there have been multiple sightings of pseudo-Darkleech redirecting hijacked traffic to exploit kits.
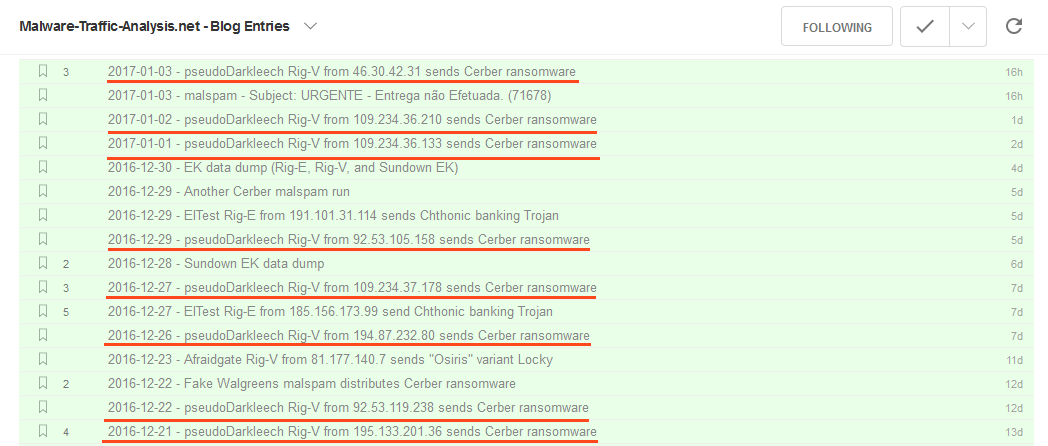
But besides exploit kit traffic, pseudo-Darkleech actors have also used the compromised websites to send spam campaigns via mailer scripts placed on the underlying servers.
pseudo-Darkleech also used to send spam
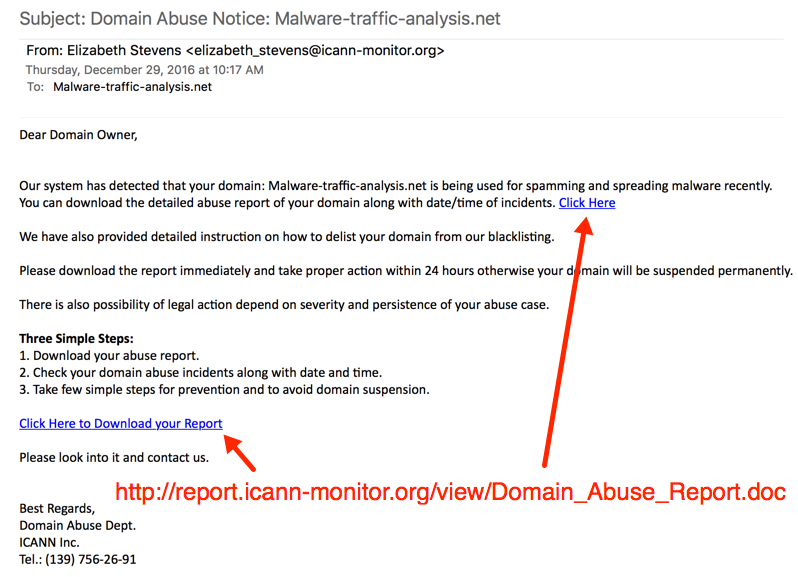
Two recent spam campaigns originating from pseudo-Darkleech infected servers have been analyzed by Brad Duncan and Heimdal Security. Just like the recent exploit kit campaigns, these have pushed the same Cerber ransomware.
Most spam emails have used subject lines perpetrating to be credit card reports, order deliveries, and ICANN domain abuse notices. Links inside these emails delivered Office documents that would have downloaded the Cerber ransomware via attached macro scripts.
Today, pseudo-Darkleech, together with similar campaigns such as the original Darkleech, Afraidgate, and EITest account for a large chunk of traffic redirected to exploit kits.
Some of these campaigns use public websites where crooks advertise their services and offer to redirect users from legitimate websites to any destination the buyer may want.
This is why we see pseudo-Darkleech being involved in so many cyber-crime activities today.
Because ransomware often provides the quickest financial turnaround for malware authors, this also explains why we see pseudo-Darkleech powering so many ransomware operations.
pseudo-Darkleech and fellow campaigns stand testament why it’s imperative to keep servers and website software up to date at all times.
A vulnerable website isn’t a danger only to the server it’s hosted on, but for thousands of other users that might be indirectly affected by a webmaster’s indifference.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











