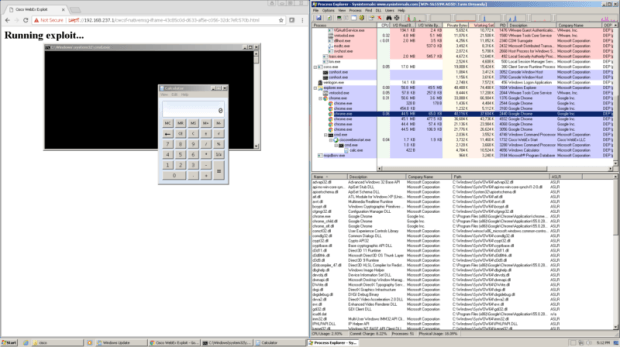
Publicly known “magic string” lets any site run malicious code, no questions asked.
The Chrome browser extension for Cisco Systems WebEx communications and collaboration service was just updated to fix a vulnerability that leaves all 20 million users susceptible to drive-by attacks that can be carried out by just about any website they visit.
A combination of factors makes the vulnerabilities among the most severe in recent memory. First, WebEx is largely used in enterprise environments, which typically have the most to lose. Second, once a vulnerable user visits a site, it’s trivial for anyone with control of it to execute malicious code with little sign anything is amiss. The vulnerability and the resulting patch were disclosed in a blog post published Monday by Tavis Ormandy, a researcher with Google’s Project Zero security disclosure service.
Martijn Grooten, a security researcher for Virus Bulletin, told Ars:
If someone with malicious intentions (Tavis, as per Google’s policy, disclosed this responsibly) had discovered this, it could have been a goldmine for exploit kits. Not only is 20 million users a large enough number to make it worthwhile in opportunistic attacks, I assume people running WebEx are more likely to be corporate users. Imagine combining this with ransomware!
All that’s required for a malicious or compromised website to exploit the vulnerability is to host a file or other resource that contains the string “cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html” in its URL. That’s a “magic” pattern the WebEx service uses to remotely start a meeting on visiting computers that have the Chrome extension installed. Ormandy discovered that any visited website can invoke the command not just to begin a WebEx session, but to execute any code or command of the attacker’s choice. To make the exploit more stealthy, the string can be loaded into an HTML-based iframe tag, preventing the visitor from ever seeing it.
While Monday’s patch came a commendable two days after Ormandy privately reported the vulnerability, the researcher warned the patch may not adequately secure the Chrome extension from all types of code-execution exploits. That’s because the update still allows Cisco’s webex.com website to invoke the magic pattern with no warning. Should the site ever experience a cross-site scripting vulnerability—a vexingly common type of Web application bug that lets attackers inject scripts into Web pages—it might be possible to use it to once again exploit the WebEx extension flaw.
Some critics also faulted the fix for providing a less-than-clear warning message when WebEx-enabled browsers visit sites that load the magic string. The warning reads: “WebEx meeting launcher needs to launch a WebEx meeting on this site. WebEx meeting client will be launched if you accept this request.” The message then gives users the option of clicking Cancel or OK.
“This is a social engineering nightmare,” Filippo Valsorda, a security researcher at content delivery network CloudFlare, told Ars. He provided this guide for protecting against the vulnerability.
In an e-mail, independent cryptography and security researcher Aaron Zauner provided this technical analysis:
The extension has its own sort-of-an API and passes JSON messages between the extension, the website where the WebEx session is supposed to happen (e.g is embedded into the website), and native browser code (i.e.Chrome). As Tavis [Ormandy] notes, the extension passes a lot of properties about the session along, many of which seem security sensitive and may be able to allow for attack vectors. One of these properties seems to have its own scripting language (Tavis’s words) and thus allows interaction with native code. The extension ships (at least parts) of Microsoft’s C runtime and thus gives an attacker the possibility to call C functionality by just passing JSON properties/objects. An exploit may be a simple webpage with JavaScript code in it. Having the WebEx extension in chrome installed—an attacker may point the victim to such a website and run arbitrary code or start programs, delete files et cetera on the victim’s computer.
The critical update is made available in version 1.0.3 of the WebEx extension for Chrome. It will be downloaded and run automatically, but given the severity, users should make sure it’s installed immediately by clicking on the three vertical dots in the top rights of Chrome. They should choose More Tools, Extensions, and view the information pertaining to WebEx. To force WebEx to update right away, users can check the “Developer Mode” checkbox and click the “Update extensions now” button.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.