A new service launched on the Dark Web this week simplifies the process of tricking victims whose card details have been exposed into revealing their card’s PIN.
The service, which we’ll reference in this article based on the first three characters of its Onion URL (QAF), came to Bleeping Computer’s attention on Wednesday, March 1, following an XMPP spam campaign.
QAF’s target is a category of crooks called carders, who engage in the theft and commercialization of payment card details, but also in printing clone payment cards and emptying out victims’ accounts with the help of money mules.
According to the QAF ad, the service allows carders to create accounts and then buy credits. QAF customers can use these credits to place calls to a victim via the service.
QAF finally adds some value to “dumps”
Carders need to provide the victim’s name, the last four digits of their payment card, the bank’s name, and the bank’s phone number.
The first two types of information, the victim’s name and last four digits of his payment card, are always included in the data stolen by criminals from POS systems or online shops.
The third, bank’s name, can be deduced from the Bank Identification Number (BIN), which is the first four or six numbers of a customer’s payment card number.
The fourth, the bank’s phone number, can be easily discovered using a browser or phone book.
QAF calls and tricks users into revealing their PIN
QAF works by “calling” the user and asking users “to confirm their ATM PIN number.” It is unclear if this process of calling users involves a human operator, an automated calls robot, or SMS messages that lure victims into accessing a fake bank portal.
Contacted by Bleeping Computer through a third-party, QAF’s operators declined to comment for this story.
If the trick works and customers provide their PINs, they will appear in the customer’s dashboard.
QAF currently in beta testing
The QAF service is currently in beta stage and registration is open to everyone. Its author(s) says he intends to close registration when QAF launches out of beta, and the service has “enough users” to sustain itself.
Users that register during the beta currently receive 20 free calling credits to test the service. Before they receive the free credits, they need to activate accounts by sending $150 in Bitcoin to the admin’s Bitcoin address. This also gives them five calling credits.
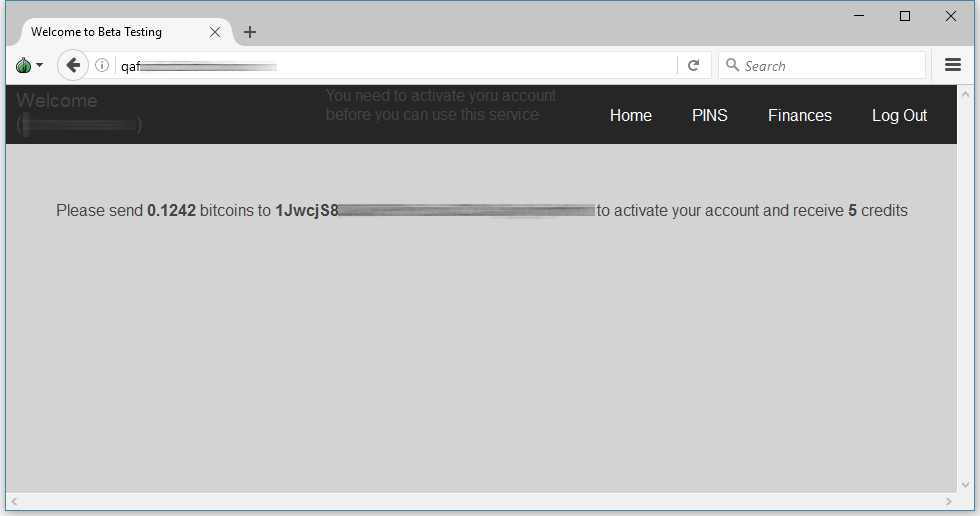
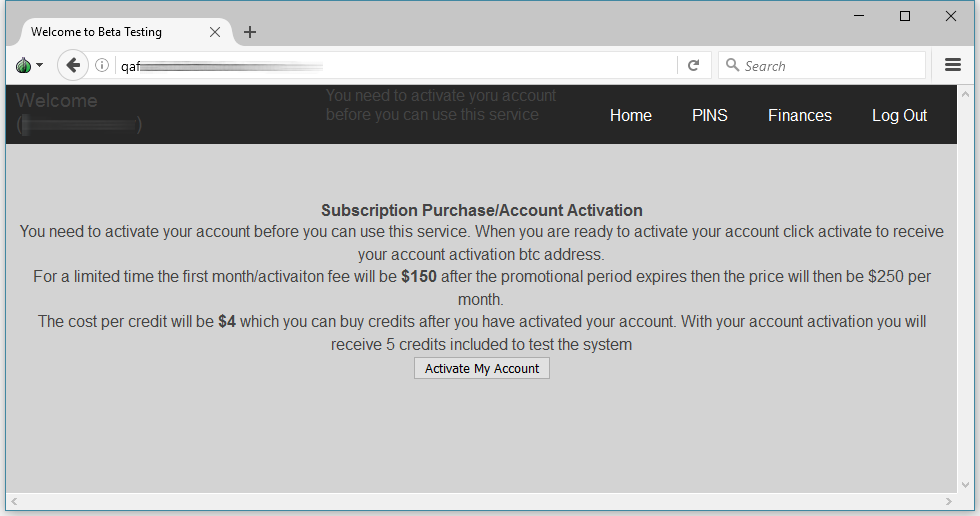
QAF admins say the activation fee is a monthly charge and once the service goes out of beta, it will go to $250 per month.
QAF looks like a very attractive target
While the price looks steep considering customers get only five calling cards, if carders secure a PIN for a well-stocked payment card, they could earn thousands in return when they empty the victim’s account.
Today there are hundreds of forums and websites where carders can sell or buy “dumps,” the name they use for collections of payment card data, such as names, card numbers, CVV codes, addresses, and other information they collect when they breach POS systems or online stores.
In most cases, this data is useless without a PIN, showing why a service like QAF is so crucial.
Didn’t think we should specifically add this to the article, but here’s a quick reminder: Never provide your payment card PIN to anyone! Banks never ask their customers their PIN number.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











