Researchers from Palo Alto Networks have come across a new ransomware family that combines many unique features, such as political statements, public subdomain creation, and encryption tiers.
Named RanRan, researchers spotted infections with this threat in only one country in the Middle East. Researchers were drawn to this threat by the political implications for each of the infected victim, who had to make political statements with which it most likely didn’t agree.
RanRan shuts down database processes
The distribution method is currently unknown, but when a victim runs the ransomware for the first time, it checks for a mutex (Services1.0). If it already exists, RanRan determines it already infected the PC and will stop its execution.
The ransomware achieves boot persistence by decoding a hard-coded base64 string. The value of this base64 string is a new registry key, which RanRan uses to launch its binary, located at C:\services.exe.
Before starting the encryption process, the ransomware will shut down a series of processes, in most part belonging to database servers. RanRan will also monitor these processes at regular intervals and prevent them from starting up again. Similarly, it also monitors and closes any desktop window containing the term “task manager.”
RanRan uses a tiered encryption scheme
The encryption is something different, as the ransomware uses different encryption keys depending on the size of the encrypted file. RanRan uses eight tiers.
- 0 – 5 MB
- 5 – 30 MB
- 30 – 100 MB
- 100 – 300 MB
- 300 – 700 MB
- 700 – 2000 MB
- 2000 – 3000 MB
- 3000 MB and greater
Palo Alto researchers describe RanRan’s encryption process as it follows:
This means that after the encryption ends, victims should see the following eight files on their computer:
- VictemKey_0_5
- VictemKey_5_30
- VictemKey_30_100
- VictemKey_100_300
- VictemKey_300_700
- VictemKey_700_2000
- VictemKey_2000_3000
- VictemKey_3000
Just like most ransomware strains, RanRan also appends a custom extension at the end of all encrypted files. This extension is .zXz.
Political message of the RanRan ransom note
Now for the most interesting part: the ransom note. This is stored in a file named zXz.html and is simple in design, with many English language errors.
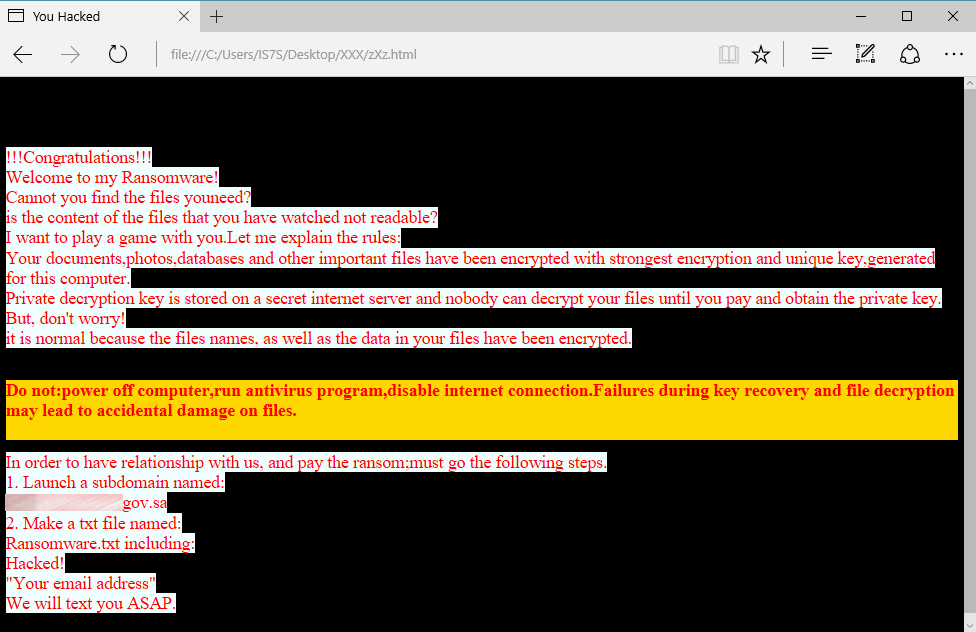
Instead of asking the victim to visit a site or make a payment to a Bitcoin address, RanRan asks victims to create a subdomain on their website, where they should upload a file named ransomware.txt containing their email address. This is in total opposition with most ransomware families which ask victims to contact the ransomware operator, not the other way around.
Furthermore, RanRan’s author uses the ransomware to deliver a political message. They do this by asking the victim to create the subdomain on their website using terms that incite violence against the country’s main political leader.
“By performing these actions, the victim, a Middle Eastern government organization, has to generate a political statement against the leader of the country,” researchers noted. “It also forces the victim to publicly announce that they have been hacked by hosting the Ransomware.txt file.”
Currently, attacks with RanRan have been spotted only in Saudi Arabia, a country where showing these political outbursts may not go well for the perpetrator. The political figure targeted in these attacks is King Salman bin Abdulaziz Al Saud, the country’s leader.
RanRan encryption defeated
Despite these innovative methods, RanRan’s author has made several mistakes when crafting the encryption process. Later they discovered the ransomware used encryption code copy-pasted from GitHub.
RanRan’s demise came because some errors prevented the ransomware from deleting original files in some situations, which allowed researchers to compare the two versions of the same file and crack the encryption scheme. Palo Alto says they already created two decrypters to recover data for victims of this new threat.
According to researchers, despite targeting a Middle Eastern country, RanRan has nothing in common with Shamoon, which recently was upgraded with ransomware features as well.
IOCs
Registry key
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WindowsProcesses it monitors and shuts down
MSSQLSERVER
SQLWriter
MSSQL$CONTOSO1
SQLServerAgent
MSSQL$SQLEXPRESS
Microsoft Exchange Information Store
OracleASMService+ASM
OracleCSService
OracleServiceORCL
OracleOraDb10g_home1TNSListener
usermanager
outlook
exchange
sqlFiles targeted for encryption
.mdf
.ldf
.edb
.pst
.ost
.doc
.docx
.pdf
.xls
.xlsx
.ppt
.pps
.pptx
.ppsx
.accdb
.mdb
.zip
.rar
.txt
.jpg
.bad
.epf
.bdp
.efp
.vsd
.mpp
.xlt
.cmd
.lic
.me
.xlsm
.war
.bdr
.stm
.sdb
.psd
.eml
.vdw
.vdx
.tar
.csv
.max
.png
.ai
.dwg
.dxf
.7z
.c
.cpp
.bak
.ese
.ashx
.asmx
.soap
.svc
.bkf
.issue
.sql
.fmb
.olb
.java
.webm
.mkv
.flv
.dbf
.mtb
.asp
.aspx
.sln
.cs
.jar
.bmp
.iso
.resx
.exe
.tar
.dat
.rtf
.img
.gz
.vmdk
.log
.ace
.kdbx
.rdp
.psc
.bat
.cfg
.rmvb
.3gp
.swf
.ipdb
.db
.cmsc
.kmz
.edxSource:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











