More than a third of the websites you visit online may include an outdated JavaScript library that’s vulnerable to one or more security flaws.
This is the conclusion of recent research carried out by a team of six scientists from the College of Computer and Information Science at Northeastern University, who scanned over 133,000 domains and found that 37% loaded outdated and insecure JavaScript libraries.
Scan methodology
The JavaScript ecosystem is the largest in the world, and the npm repository includes nearly 100,000 libraries. The scan did not cover all, but only 72 of the most popular JavaScript projects, such as jQuery, Angular, Handlebars, Bootstrap, Modernizr, Moment, LoDash, and others.
To assess the state of each library, researchers also built their own database of vulnerabilities for the selected JavaScript projects.
Using Amazon’s Alexa site index, they then scanned 133,000 websites (Alexa top 75K and 75K random .com sites) and monitored if one of the 72 libraries was loaded on each site, and what library version.
The scan didn’t only monitor the website’s own libraries, but also JavaScript loaded by third-parties, such as advertisers.
In total, researchers detected 11,141,726 JS script file inclusions and inline JS scripts. Below is a summary of the different results researchers obtained:
- 37% of the scanned websites loaded at least one vulnerable library version
- 10% of the scanned websites loaded two or more vulnerable library versions
- At least 36.7 % of jQuery, 40.1 % of Angular, 86.6 % of Handlebars, and 87.3 % of YUI inclusions use a vulnerable version
- Many websites continue to load libraries SWFObject and YUI, which are no longer maintained
JS libraries stay without updates for 3 to 4 years
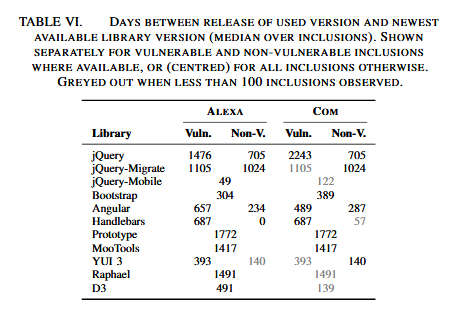
On top of these numbers, researchers observed other issues through second-stage analysis. For example, the median time difference between the release date of vulnerable library version (loaded on the site) and the date of the latest release of that library is 1,177 days for Alexa sites, and 1,476 days for random .com sites.
What this means is that many websites have continued to use old JS library versions, despite updates being available. On average, sites remained vulnerable for at least three to four years.
In addition, libraries loaded inline or transitively via third-party code/widgets have a higher rate of vulnerabilities compared to JS libraries loaded through direct script calls on the site.
This can be explained by the fact that developers find it generally easy to check the “scripts” section of their website and update any outdated libraries, but often forget about inlined JS code, or can’t force their advertiser to use a secure version.
Furthermore, researchers also observed a general lack of awareness to security problems in the JavaScript community. Information on security bugs was hard to find, and web developers were often trapped in using outdated JavaScript library versions because many updates broke backward compatibility, meaning webmasters had to rewrite applications from scratch, something that’s out of the question.
From the view of an outsider, the JavaScript community grew too fast, too quick, and developers have not had the time to define and cultivate a security-minded approach to writing and maintaining JavaScript code. Just imagine that only a decade ago we all wanted one of those silly jQuery image carousels on our homepages, and now, JavaScript runs most of our web and mobile apps, handles encryption, 3D graphics, and complex data visualizations.
“The paper’s findings are a painful wake-up call,” says Tim Kadlec, developer for Snyk, a service that finds vulnerabilities in JS projects. “Generally speaking, our industry has been quick to take advantage of the wealth of resources that open-source development provides, but much slower to recognize and protect ourselves from the risks that can come along with it.”
Similar past studies
But there’s a good side to this recent research. Similar studies have taken place in the past. A scan of the Alexa Top 100K sites, carried out in 2014, found much more worrisome results, with 60% of the scanned sites loading vulnerable JavaScript library versions.
Outside the JavaScript ecosystem, similar research targeted other environments, such as the influence of outdated libraries and dependencies in Java, Windows, and Android [1, 2].
The full research paper, titled “Thou Shalt Not Depend on Me: Analysing the Use of Outdated JavaScript Libraries on the Web,” is available for download here. The research team presented their work at last week’s Network and Distributed System Security (NDSS) Symposium held in San Diego, California.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











