A new adware family named Crusader will rewrite tech support phone numbers returned in Google search results, display ads, and show popups pushing tech support scams.
Current versions of Crusaders are installed on victims’ computers via software bundles. Users usually download a free application, whose installer also adds Crusader.
The adware takes the form of a Chrome extension, Firefox add-on, and Internet Explorer Browser Helper Object. Because it’s delivered as a browser extension, Crusader is in the privileged position of listening and modifying the user’s entire Internet traffic.
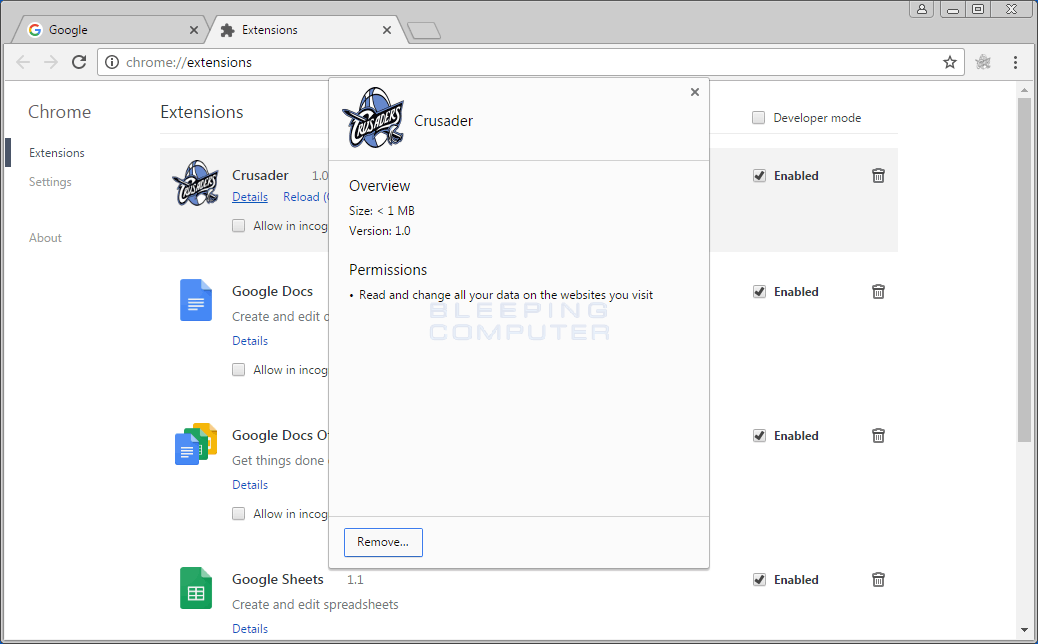
All the malicious actions Crusader takes are detailed in a configuration file the adware downloads after it infects each user, and at every boot-up. The config file is retrieved following an HTTP request at:
https://demo1.geniesoftsystem.com/Crusader/index.php/api/getdetails?data={%22id%22:%221%22,%22keyword%22:%22antivirus%22,%22count%22:%225%22,%22country%22:%22[country]%22}Based on Bleeping Computer’s tests, the only country this server returns a configuration file is for India. The content of the configuration file also makes us believe Crusader is still in development because many options contained the words “demo” and appeared to be placeholder settings. Below, we’ll go over Crusader’s config file, one block at a time.
The above block shows that Crusader has the ability to change the browser’s homepage and default search engine settings to the crook’s provided URL. Currently, both values are google.co.in, the official URL of Google India.
"data": {
"userid": "1",
"default_search_url": "https:\/\/www.google.co.in",
"default_homepage": "https:\/\/www.google.co.in",
"default_setting_status": "true",
"popup_status": "true",
"popunder_status": "",
"textdisplayads_status": "true",
"searchmarketing_status": "true",
"urlredirection_status": "true",
"broadredirection_status": "true",
"banner_status": "true",
"banner_replacement_status": "true",
"popupOverlay_status": "true",
"catfishbanner_status": "true",
"object_browser_status": "true",
"search_text": "antivirus",
"splitwindow_status": "true",
"youtube": [
],Other settings reveal that Crusader was conceived with intentions to show popup ads, popunder ads, insert banner ads on top of other websites, replace existing page banners, and redirect users to specific URLs. Each of these features can be turned on or off, based on the latest configuration file crooks upload to their C&C server.
The config snippet below directs Crusader to display a pop-up containing the configured site when a user searches for a particular keyword. In this example, if a user searches for “quickbook support” it will open a popup that displays www.preranatechnologies.net, why if you search for “free movies” it displays www.esolvz.net.
"keywordlist": {
"popup_compaign_name1": "Quickbook Campaign",
"popup_includekeyword1": "quickbook support",
"popup_url1": "www.preranatechnologies.net",
"popup_exclude_url1": "",
"popup_browser1": "Internet_Explorer,Chrome,Firefox",
"popup_exclude_macadd1": "",
"popup_frequency_date1": "02\/01\/2023",
"popup_filter_ip1": "0",
"popup_compaign_name2": "demo",
"popup_includekeyword2": "free movies",
"popup_url2": "www.esolvz.net",
"popup_exclude_url2": "",
"popup_browser2": "Internet_Explorer,Chrome,Firefox",
"popup_exclude_macadd2": "",
"popup_frequency_date2": "02\/20\/2018",
"popup_filter_ip2": "0"
},More campaigns could be added in this block, to show more popups, advertising other sites, all depending on the list of preconfigured keywords.
The below config snippet directs Crusader to open a new unfocused window (popunder ad) for amazingdeals.online/daily_deals/, every type the user navigates to amazon.co.uk.
"popunderlist": {
"popunder_include_url1": "amazon.co.uk",
"popunder_url1": "https:\/\/amazingdeals.online\/daily_deals\/",
"popunder_exclude_url1": "",
"popunder_compaign_name1": "demo",
"popunder_browser1": "Internet_Explorer,Chrome,Firefox"
},The next block is currently empty, but we presume it’s a feature to insert or replace ads in Google or Bing search results themselves or to convert text on a page into clickable advertisements.
"TextDisplayaddslist": [
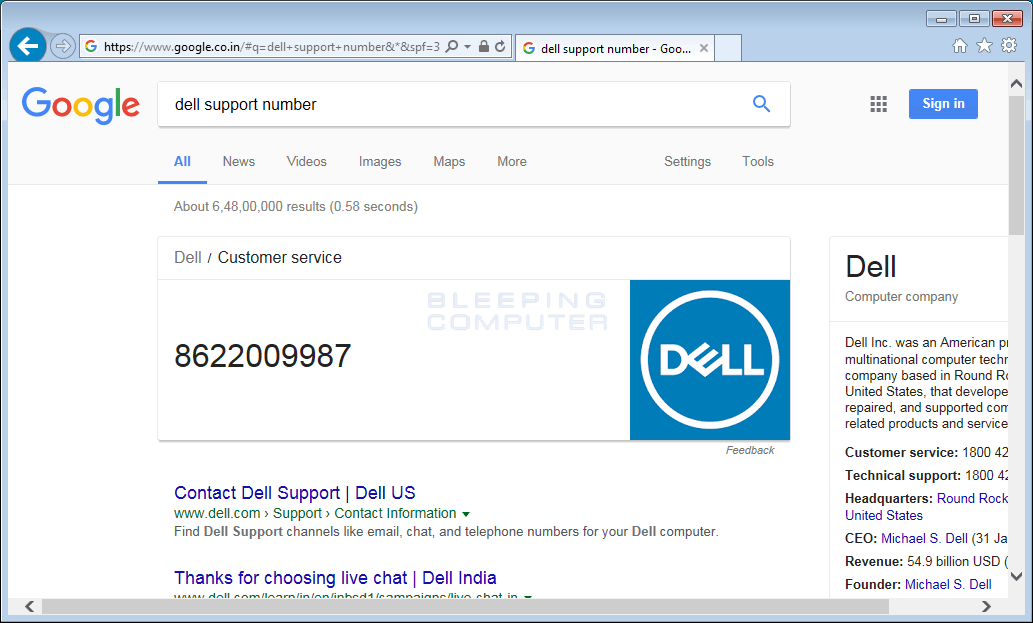
],Now, this is the most interesting block, because the settings above tell the adware to snoop on search queries and replace the contact number for various security products.
"searchMarketinglist": {
"antivirus_keyword1": "dell support number",
"antivirus_contact1": "8622009987",
"antivirus_exclude_macadd1": "",
"antivirus_browser1": "Internet_Explorer,Chrome,Firefox",
"antivirus_filter_ip1": "0",
"antivirus_keyword2": "norton support number",
"antivirus_contact2": "9143109610",
"antivirus_exclude_macadd2": "",
"antivirus_browser2": "Internet_Explorer,Chrome,Firefox",
"antivirus_filter_ip2": "0"
},Currently, the adware will replace the phone number returned in search results for Dell and Norton whenever the user searches for “dell support number” or “norton support number.” We presume more options could be added to target other antivirus vendors.
This is both a self-defense mechanism and a marketing tool. If users detect something wrong with their browser and looks up the support number in Google, intsead of the legitimate number being displayed, Crusader will rewrite the text and display a different number. When a user calls this number they will be redirected to a tech support call center, where an operator disguising themselves as representative for those two companies might sell him services or products he doesn’t need.
This code block tells the Crusader adware to redirect all search queries for “hotel goa” to Hilton.com. In the future, expect links with affiliate IDs in this section, as the crook could earn a nice profit by driving traffic to certain websites.
"redirectionlist": {
"urlredirection_compaign_name1": "demo",
"urlredirection_current_url1": "hotel goa",
"urlredirection_target_url1": "www.hilton.com",
"urlredirection_frequency_time1": "150 views",
"urlredirection_exclude_macadd1": "",
"urlredirection_frequency_date1": "2\/20\/2018",
"urlredirection_filter_ip1": "0"
},Currently empty, we presume this is another URL redirection system that also hijacks search results. The term “broad,” might imply this is a more generic en-masse URL redirection mechanism.
"broadredirectionlist": [
],This block tells Crusader to replace banner ads with the crook’s own. Currently, this block loads a generic banner that links to Facebook.
"bannerreplacement_list": {
"replace_compaign_name1": "demo",
"replace_url1": "https:\/\/www.facebook.com\/",
"banner_name1": "BR00036",
"sponsor_type1": "facebook",
"replace_banner1": "https:\/\/demo1.geniesoftsystem.com\/Crusader\/uploads\/banners\/aerojetobj_1487159946_1487911841.jpg",
"exclude_macadd1": "",
"banner_replacement_frequency_date1": "2\/20\/2018",
"banner_replacement_filter_ip1": "0"
},We haven’t seen this feature in action, but we presume it’s another keyword search hijacking feature.
"splitwindow_list": {
"Advertisement_compaign_name1": "demo",
"Advertisement_URL1": "https:\/\/preranatechnologies.net\/",
"Your_Keyword1": "vicidial",
"Search_Engine1": "Google,Yahoo,Bing",
"split_window_frequency_date1": "2\/20\/18",
"split_window_filter_ip1": "0"
},The code below is used to show popup ads when users visit a certain website, in this case, wow.com. The banners show a fake antivirus alert and are obvious lures for tricking users in calling tech support scammers.
"popupoverlaylist": {
"overlay_compaign_name1": "demo",
"overlay_include_url1": "https:\/\/www.wow.com\/",
"banner_name1": "P0002",
"overlay_banner1": "https:\/\/demo1.geniesoftsystem.com\/Crusader\/uploads\/banners\/file-system-warning (US1)_1487948400.gif",
"overlay_frequency_date1": "2\/20\/2018",
"overlay_compaign_name2": "demo",
"overlay_include_url2": "www.cyboscan.com",
"banner_name2": "P0004",
"overlay_banner2": "https:\/\/demo1.geniesoftsystem.com\/Crusader\/uploads\/banners\/file-system-warning-(US2)_1487955020.gif",
"overlay_frequency_date2": "2\/20\/2018",
"overlay_compaign_name3": "demo",
"overlay_include_url3": "www.facebook.com",
"banner_name3": "P0005",
"overlay_banner3": "https:\/\/demo1.geniesoftsystem.com\/Crusader\/uploads\/banners\/file-system-warning-(AU)_1489010023.gif",
"overlay_frequency_date3": "2\/20\/2018"
},You can see an example of an injected ad below.
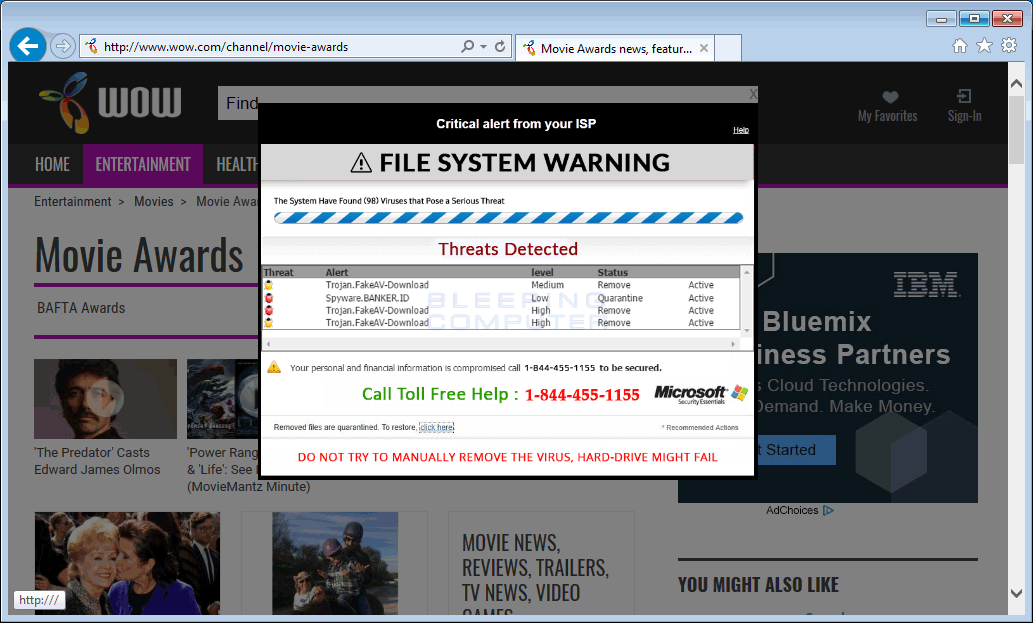
These last two blocks in the configuration file are for injecting floating banners on top of other sites, at the bottom of the browser window.
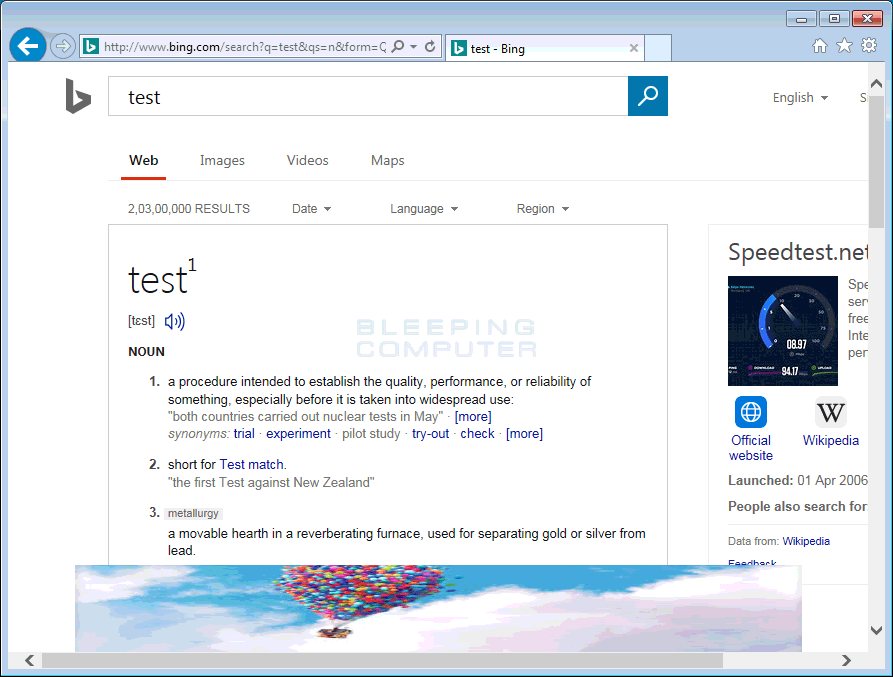
"catfishbannerlist": {
"cat_compaign_name1": "demo",
"cat_url1": "www.bing.com",
"banner_name1": "C0002",
"cat_frequency_time1": "150 views",
"cat_banner1": "< body >< center >< a href=\"https:\/\/www.yahoo.com\" target=\"blank\">< img src=\"https:\/\/demo1.geniesoftsystem.com\/Crusader\/uploads\/download3.jpg\" border=\"0\" height=\"89\" width=\"727\"\/>< \/a>< \/center>",
"catfish_frequency_date1": "2\/20\/2018",
"cat_filter_ip1": "0"
}, "bannerinjection": {
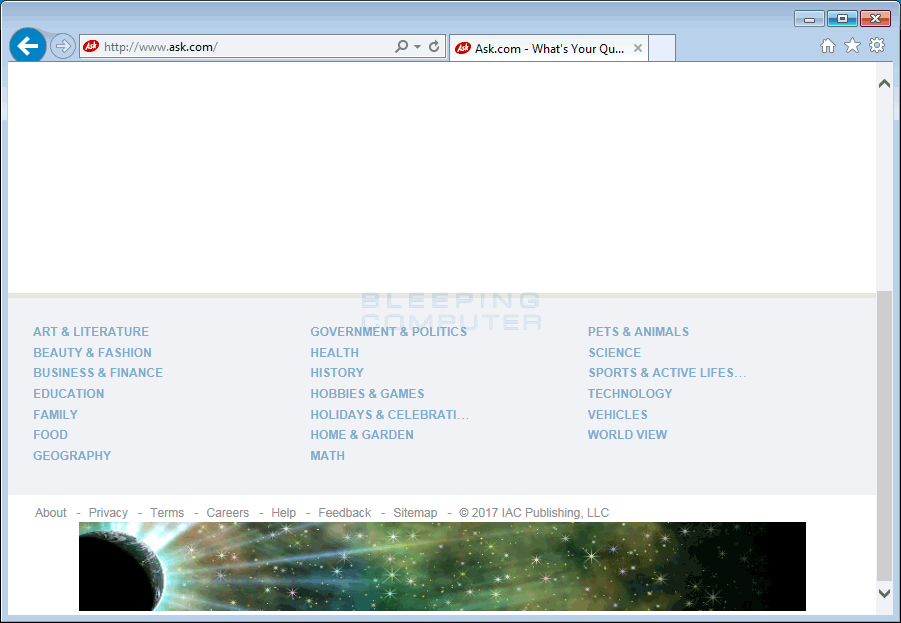
"banner_compaign_name1": "demo",
"banner_url1": "www.ask.com",
"banner_header1": "< body>< center>< a href=\"\" target=\"blank\">< img src=\"https:\/\/demo1.geniesoftsystem.com\/Crusader\/uploads\/82e85b2a94b3d4371b42189b9d69eb05.jpg\" border=\"0\" height=\"89\" width=\"727\"\/>< \/a>< \/center>",
"banner_footer1": "< body>< center>< a href=\"\" target=\"blank\">< img src=\"https:\/\/demo1.geniesoftsystem.com\/Crusader\/uploads\/ithaca-nightlife-night-life-astro-image-1001.jpg\" border=\"0\" height=\"89\" width=\"727\"\/>< \/a>< \/center>",
"banner_name1": "B0002",
"banner_excludemacadd1": "",
"banner_frequency_date1": "2\/20\/2018",
"banner_filter_ip1": "0"
}The config file currently shows these banners on top of the Ask.com and Bing homepages, but they could be overlaid, in theory, on top of any website.
|
|
|
At this point Crusader appears to be in a testing mode, but if it is currently live or becomes live, you can use this guide to remove Crusader from your system.
Source:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.