A portal hidden on the Dark Web is responsible for the small deluge of recent PadCrypt ransomware versions that have been spotted almost on a monthly basis in the past year.
Besides infosec experts tracking ransomware evolution, very few people know that PadCrypt is one of the most active and well-maintained ransomware variants encountered in the wild today.
PadCrypt’s evolution
The ransomware was first spotted last year, in February, and when it came out, it included a unique feature that allowed victims to talk to the PadCrypt operator in real-time, via a live chat window.
The ransomware didn’t survive its first month, and after several of its C&C servers were taken down, its operators took a four-month break and came back in July 2016 with an improved version.
Despite its comeback, PadCrypt never rivaled other ransomware threats and continued to make sporadic infections here and there, evolving one small step at a time.
Things change drastically in November 2016, when security researchers spotted clues that PadCrypt might have added an affiliate system.
This update coincided with the release of PadCrypt v3 and was big news as it hinted that PadCrypt was preparing, or already moved from a one-man show to an operation where one man develops the PadCrypt source code, and multiple “affiliates” are distributing it to victims.
PadCrypt affiliate system linked to NemeS1S RaaS
For a long time, the only clue about PadCrypt’s affiliate system was an ID in the ransomware’s source code. Things changed in February 2017, when a security researcher found a link to PadCrypt’s RaaS portal.
That site didn’t live long, and after 24 hours it was down or moved to a new URL. Since the service wasn’t advertised via XMPP spam or on known underground hacking forums, we’ve lost track of PadCrypt’s RaaS, and its development.
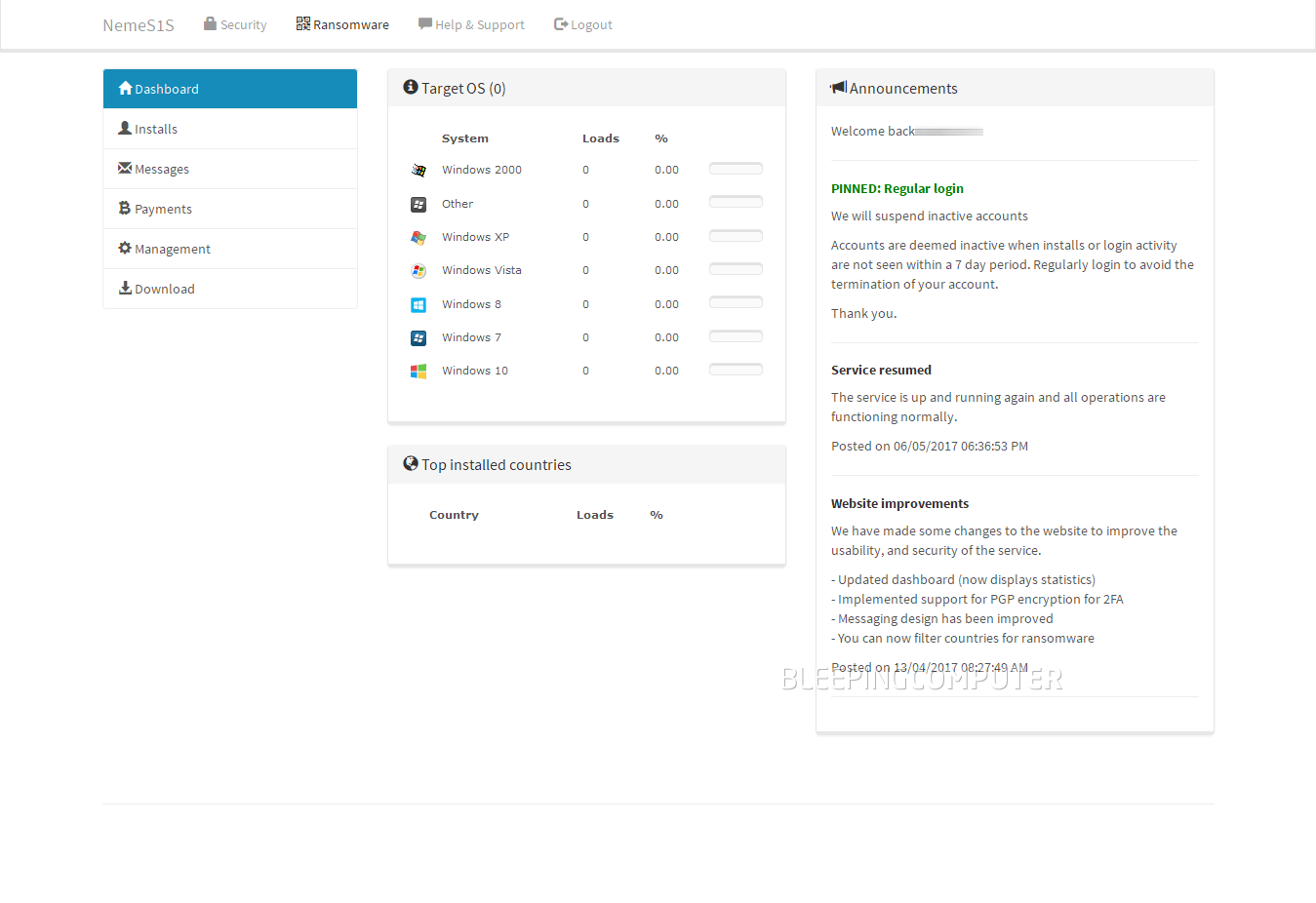
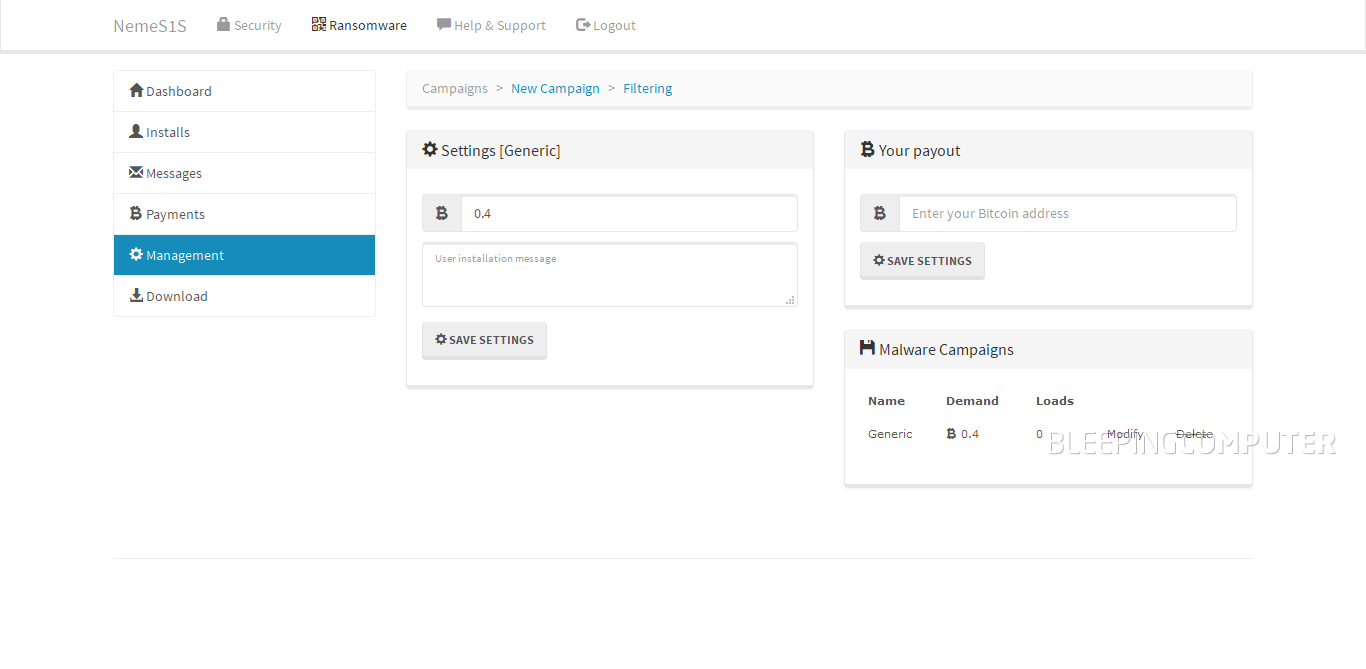
Yesterday, things changed. One of the Tor link directories we were keeping an eye on indexed a new site called “Control Panel.” Since the name would have piqued anyone’s interest, we checked out what this “Control Panel” was for. What we discovered was a generic page named “Ransomware Portal” featuring open registration.
Registering on the site we encountered our old friend, the NemeS1S RaaS, aka PadCrypt’s affiliate system, albeit with a little bit more features than the last time we saw it.
|
|
|
|
|
|
|
|
|
|
|
|
Is PadCrypt distribution a closed system?
Based on feedback from a threat intelligence company that wanted to remain anonymous, the PadCrypt operators didn’t bother advertising the NemeS1S RaaS, just like the last time we saw it.
The most natable feature was that the service didn’t include a section where a newly registered user could buy a license and join the affiliate system.
The lack of advertising or a buy link in the NemeS1S backend leads us to believe access to the service is only given to trusted distributors, most likely selected from friends, past collaborators, or users with a reputation in the ransomware industry.
This conclusion is supported by findings from security researcher MalwareHunter, who told Bleeping Computer that he only discovered two affiliate IDs in PadCrypt samples in the past months. Other RaaS-based ransomware threats, such as Cerber, usually have tens of third-party distributors (affiliates).
PadCrypt made very few victims, despite being active for a year
This lack of friendliness towards new users and the lack of affiliates also explains why the ransomware has never made so many victims in the past year.
The chart below shows the number of monthly PadCrypt infections for the past few months, as detected by the ID-Ransomware (IDR) service.
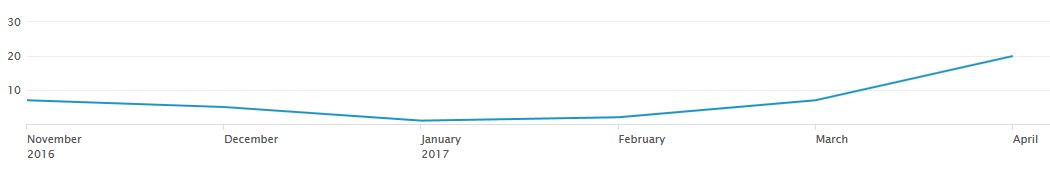
“IDR has seen less than 50 victims overall,” MalwareHunter told Bleeping Computer in an online chat. “A very small number, especially if we think about the number of samples seen.”
A tweet by David Montenegro hints that PadCrypt’s NemeS1S RaaS has currently made 192 victims, albeit this can’t be confirmed.
PadCrypt has a cloudy future
Ransomware projects rarely survive a month, let alone a full calendar year. PadCrypt, who in the meantime has reached version 3.4.4, has managed to keep a low profile and evolve from a low-end product to a fully-functional RaaS.
There are various reasons why PadCrypt’s author is keeping a low profile. He may bot be sure his service is strong enough to handle all the traffic, or he may not want the gaze of cyber-security firms on his operation. Whatever it is, it probable good news for the rest of us.
Currently, there’s no known method of recovering files encrypted by any of the PadCrypt versions.
Source:https://www.bleepingcomputer.com/news/security/nemes1s-raas-is-padcrypt-ransomwares-affiliate-system/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.