Today we are going to take a quick look at a new ransomware called RSAUtil that was discovered by Emsisoft malware researcher xXToffeeXx. RSAUtil is distributed by the developer hacking into remote desktop services and uploading a package of files. This package contains a variety of tools, a config file that determines how the ransomware executes, and the ransomware itself.
While this ransomware is currently not decryptable for free, it may be in the future. If you wish to discuss this ransomware or receive support, you can use the dedicated RSAUtil Help & Support topic in our forums.
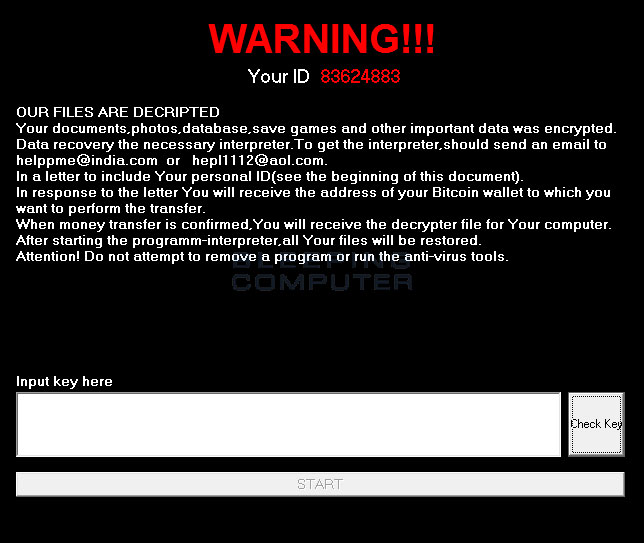
Taking a look at the RSAUtil Installation Package
Before we look at the ransomware component, let’s take a quick look at the contents of the package uploaded by the developer to a hacked machine. This package is used to prep the computer for the installation of the RSAUtil ransomware. Below is the folder containing all of the files that are part of the RSAUtil installation.
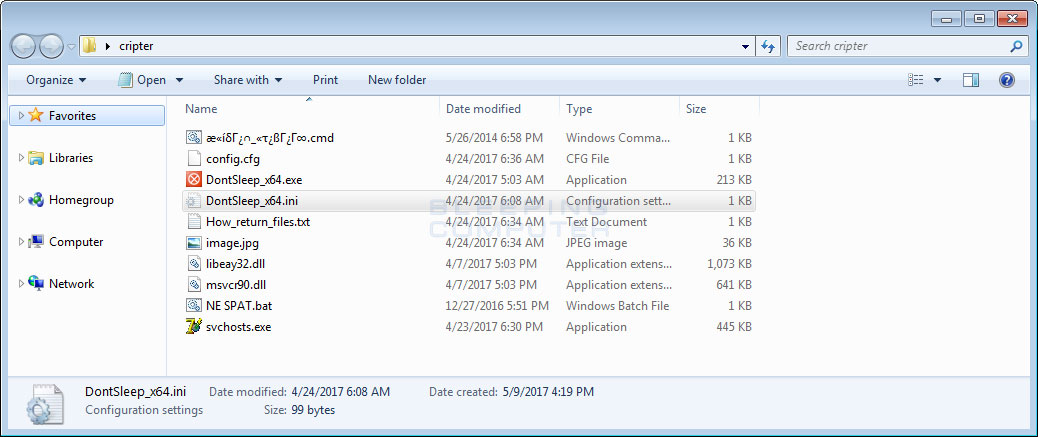
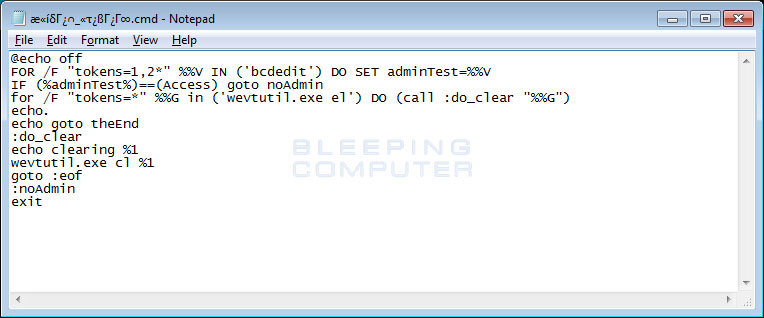
Going through each file in the package, we will start with the first CMD file. This file is used by the hacker to clear all of the event logs on the machine to clean up traces of how the machine was compromised.
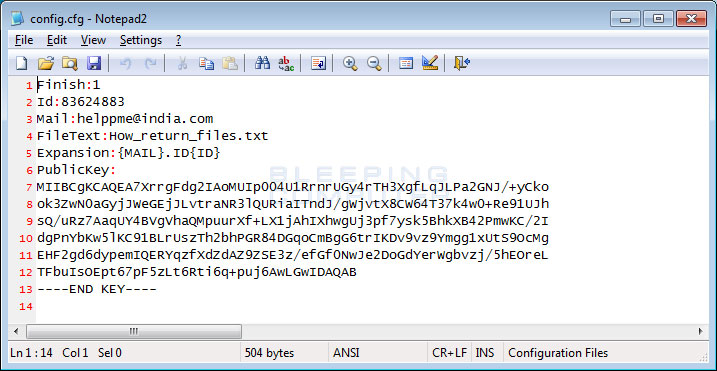
The config.cfg file is the configuration file used by the RSAUtil ransomware component when performing the encryption. The various directives control whether the ransomware has encrypted the computer already, what ID to use, what email to use, the ransom note name, the encrypted file extension, and the public encryption key to use to encrypt files.
The DontSleep_x64.exe and DontSleep_x64.ini files are used to stop the computer from going to sleep or hibernating. This is done so that the hacker does not lose connection and so that the ransomware does not get interrupted. This is a legitimate program being used by the ransomware developer.
How_return_files.txt is the ransom note that will be placed in every folder that a file is encrypted.
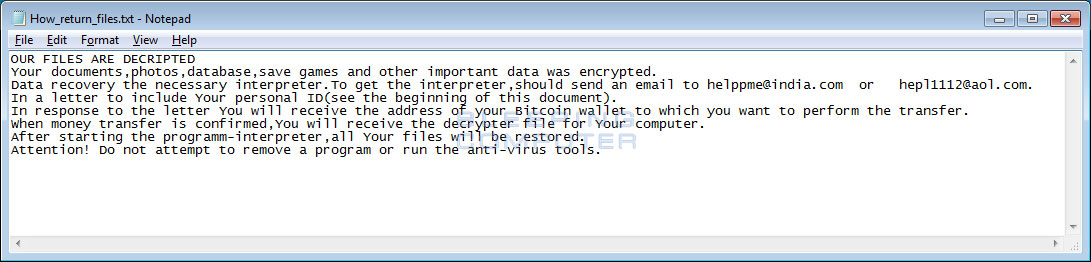
Image.jpg looks to be an image file that the desktop background should be set to. I didn’t see this file being used in my test, unless the hacker manually changes the background to that image.
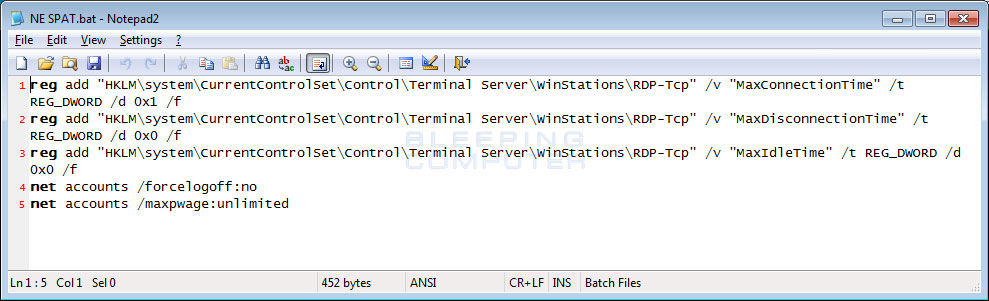
NE SPAT.bat is used to configure various remote desktop services options. This file is run by the hacker to make it so they will not be disconnected from the Remote Desktop connection when they are idle.
Finally, we have the svchosts.exe file, which is the RSAUtil ransomware. As long as Finish is set to 0 in the config.cfg file, when executed, the ransomware will scan the computer’s folders, mapped network drives, and unmapped network shares for files and encrypt them. We will go into a bit of detail about that process in the next section.
Launching the Svchosts.exe Executable
When the hacker has prepped the computer using the package’s CMD/batch files and executables, it is time for them to encrypt the targets computer. To do this they simply execute the svchosts.exe program and it will begin to scan the computer, mapped drivers, and unmapped network shares for files to encrypt.
Unlike most ransomware, RSAUtil does not have an list of file extensions it targets. This means that many executables on the computer will become encrypted as well, which is incredibly annoying when trying to analyze ransomware.
While encrypting files it will use the encryption key found in the config.cfg fil and append an extension to the encrypted files based on various information in the config file. For example in the sample xXToffeeXx discovered, we have the following settings:
Id:83624883
Mail:helppme@india.com
Expansion:{MAIL}.ID{ID}This means that the extension that is appended will be in the format .helppme@india.com.ID83624883. So a file named test.jpg will be encrypted as test.jpg.helppme@india.com.ID83624883. You can see a folder of encrypted test files below.
.jpg)
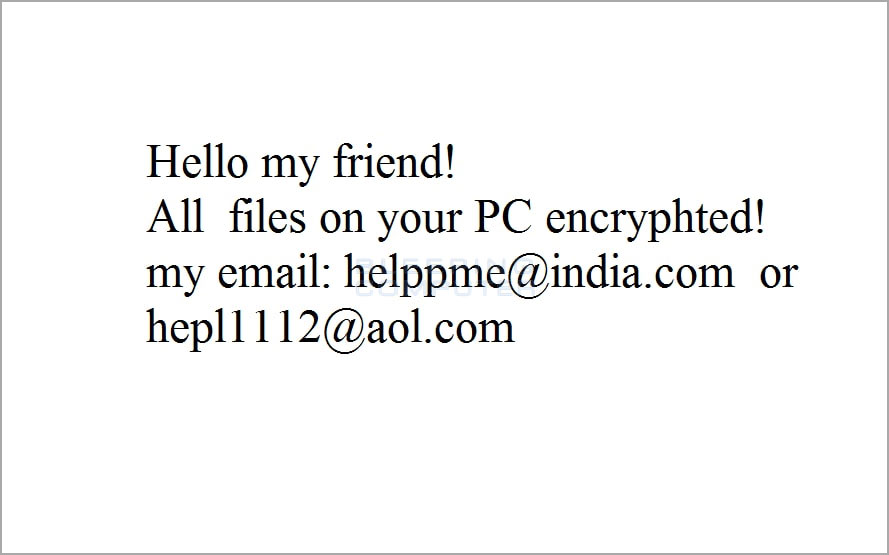
When the ransomware has finished encrypting files it will display a lock screen that tells you to contact helppme@india.com or hepl111@aol.com to receive payment instructions. Once payment is made, a victim will receive a decryption key that they can input into the lock screen to decrypt their files.

The ransomware will also create ransom notes named How_return_files.txt in every folder that a file was encrypted. This ransom note can be seen below and contains the same information as the lock screen.

As previously said, while this ransomware is not currently decryptable for free, it may be in the future. So please, contact us here or in the RSAUtil Help & Support topic before paying the ransom to see if we can help or not.
IOCs
Hashes:
SHA256: 70796b9d2dc9a178f8127c1b7f17f602134e6c0cbd325bae92e6cee51bbcbd03
Files associated with RSAUtil:
config.cfg
DontSleep_x64.exe
How_return_files.txt
image.jpg
libeay32.dll
msvcr90.dll
NE SPAT.bat
svchosts.exe
æ«ídG¿n_«t¿ßG¿G8.cmdRegistry Changes:
HKLM\system\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp "MaxConnectionTime"=1
HKLM\system\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp "MaxDisconnectionTime"=0
HKLM\system\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp "MaxIdleTime"=0
Source:https://www.bleepingcomputer.com/news/security/rsautil-ransomware-helppme-india-com-installed-via-hacked-remote-desktop-services/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











