The WannaCry ransomware — also known as WCry, Wana Decrypt0r, WannaCrypt, and WanaCrypt0r — infected a honeypot server made to look like a vulnerable Windows computer six times in the span of 90 minutes, according to an experiment carried out by a French security researcher that goes online by the name of Benkow.
During one of those infections, WannaCry infected the honeypot in a mere three minutes after it was reset, showing the aggressive nature of the ransomware’s scanning module, which helps it spread to new victims. Remind you that the ransomware was defanged via a kill-switch researchers found in its code, but this test shows how quickly new infections will be made if this kill switch wouldn’t have been discovered.
Furthermore, three minutes is about the same amount of time IoT malware will infect a vulnerable home router left connected to the Internet without patches.
We all know the huge problems caused by IoT malware and IoT botnets, and Benkow’s experiment shows how widespread the WannaCry problem is.
223,000 infections later the group has made only $31,000
According to data from the MalwareTech botnet tracker, the WannaCry ransomware has made over 223,000 victims since it started to spread on Friday afternoon.
Across the large number of infections, researchers have discovered that the authors of the ransomware have used only three Bitcoin addresses to receive payments [1, 2, 3].
At the time of writing, these three Bitcoin wallets hold 17.309 Bitcoin, which is around $31,600. Compared to the number of infections, the WannaCry gang has failed to capitalize on their tool.
According to Stefan Tanase, security researcher for Kaspersky Lab, an explanation for this is that the ransomware was active during the weekend and that many companies have not noticed the infections, and payments will increase on Monday, as they will resume operations.
WannaCry is mundane, nothing special
In a very simplistic explanation, under the hood, the WannaCry ransomware is made up of two main parts: the ransomware itself — which encrypts users’ files — and the SMB worm — the component that spreads the ransomware to random computers that have an exposed SMB port (port 445).
The SMB worm is top-shelf code, mainly because it’s a modified version of the ETERNALBLUE exploit, an alleged hacking tool created by the NSA, stolen and leaked online by an anonymous group known as The Shadow Brokers.
On the other hand, the ransomware module is quite mundane —your run-of-the-mill ransomware. It’s not as bad as other ransomware variants Bleeping Computer has analyzed in our ransomware write-ups in the past 3-4 years, but it’s nowhere near as sophisticated as top ransomware threats such as Locky, Cerber, or TeslaCrypt (now defunct).
The work of an unsophisticated group
Remind you, WannaCry is actually version 2.0 of a ransomware family previously referred to as WCry.
Version 1.0 of this ransomware was discovered by Malwarebytes researcher S!Ri on February 10 and then spotted in a brief campaign on March 25 by GData security researcher Karsten Hahn. It was so unimpressive that there were very few mentions of its activity prior to Friday’s attacks.
Before the global outbreak — obviously powered by the SMB worm module — Trend Micro had detected a WCry 1.0 version in a distribution campaign on April 25. For that campaign, the WannaCry gang had used mundane tactics seen with many other ransomware families, such as email spam or malware droppers. In some incidents, the group even hosted some of the ransomware’s payloads on Dropbox — out of all services — where Trend Micro had no problem reporting the resources and having them taken down.
A security researcher that wanted to remain anonymous described the previous versions as “utter [expletive].” Why the harsh words? Probably because the ransomware uses only three Bitcoin addresses instead of one per infected user. As Bleeping Computer’s Lawrence Abrams highlighted on Friday this will cause problems when payng the ransom, as the WannaCry gang will have a hard time distinguishing who paid the ransom and what victims are making false claims. This is usually the hallmark sign of an in-dev ransomware, created by people with little experience in the field.
Unfortunately, in spite of these operational slip-ups, researchers have yet to find a flaw in the WannaCry ransomware encryption process to allow them to restore the victims’ files.
Despite some clickbait articles in mainstream media that claim this is the work of a nation-state actor — or even WikiLeaks — all clues point to the fact that an unsophisticated group — active on the ransomware stage for at least three months — had stumbled upon ETERNALBLUE and were the first to find a way to weaponize the NSA hacking tool for their shady operation. Expect other groups to implement the SMB worm in their code in the near future, as it’s just too effective to be ignored.
No new WannaCry version, as of yet
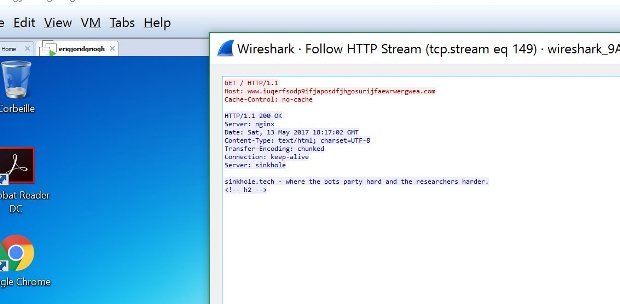
On Friday night, a security researcher was able to discover a so-called “kill switch” in the ransomware’s source code. Going by the nickname of MalwareTech, this researcher found that the ransomware was pinging the iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com domain before starting the encryption process.
If the domain was not registered, the ransomware would start its encryption process, if it was registered, it would not encrypt any files. To protect victims, the researcher registered the domain, effectively preventing WannaCry from making new victims.
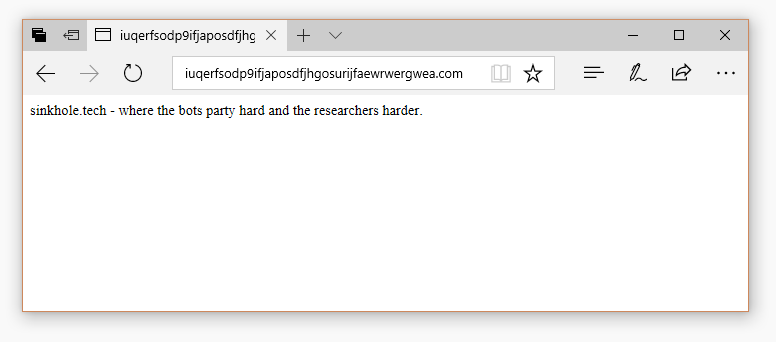
Unfortunately, some AV companies and network administrators misunderstood this process and started banning requests to this domain, and indirectly allowing the ransomware to continue to spread.
Furthermore, there have been claims that the WannaCry gang had created a new version without the kill switch system. Despite some media reports on the topic, the researchers who made those claims never presented any evidence, and backed down on their claims the second day [1, 2]. All the researchers Bleeping Computer contacted denied seeing a new version.
Users should focus on patching computers
For the time being, Wana Decryptor seems to have been contained. This is the perfect time for users and companies to patch vulnerable computers.
The ransomware’s SMB worm takes advantage of a vulnerability that Microsoft patched via security bulletin MS17-010 way back in March.
Because WannaCry attacks were so bad, on Saturday, Microsoft also released extra patches for the SMB exploit for old operating systems it stopped supporting years before, such as Windows XP, Windows 8, and Windows Server 2003.
Additionally, the CERT Spain team has released a tool that sysadmins can deploy on computers as a way to prevent the WannaCry ransomware from running. Similarly, Cybereason has updated their RansomFree utility to detect the early phases of a WannaCry infection and stop it.
For those affected, you can discuss this ransomware and receive support in the dedicated WanaCrypt0r & Wana Decrypt0r Help & Support Topic. Bleeping Computer also published a technical analysis of the WannaCry / Wana Decrypt0r ransomware.
Source:https://www.bleepingcomputer.com/news/security/honeypot-server-gets-infected-with-wannacry-ransomware-6-times-in-90-minutes/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.