Russian authorities have arrested the Cron malware gang, responsible for selling the Tiny.z Android banking trojan and the PonyForx Windows infostealer.
The investigation was of massive proportions and authorities arrested over 16 individuals in six different Russian regions between November 2016 and April 2017.
Details about the arrest became public yesterday via a statement from Russian police and Group-IB, a cyber-security firm based in Russia, which helped during the investigation.
Cron group started operating in mid-2015
The Cron malware gang began operations in mid-2015 when they started distributing the Tiny.z Android banking trojan via third-party app stores.
The crooks disguised the trojan as copies of official banking apps, or inside other apps, such as Navitel, Framaroot, Pornhub, Avito, and others.
Once users installed these apps on their devices, the malware hidden inside them granted the Cron group the ability to phish banking credentials and two-step verification codes from the user’s device by intercepting SMS messages.
Tiny.z allowed crooks to take over bank accounts using the user’s Android device, and siphon money from victims in small transactions of $120 on average.
While the group targeted customers of banks in various countries, the group made a crucial mistake by targeting customers of Russian banks, the country where they were living in.
Their intrusive malware campaigns caught the attention of Group-IB researchers and Russian authorities, who began an investigation into the group’s operation.
Cron group advertised malware on underground hacking forums
Their biggest mistake was when, on April 1, 2016, they published an ad on a Russian-speaking forum, advertising their Android banking trojan. This gave Group-IB researchers an initial clue of who was behind the wave of Tiny.Z infections.
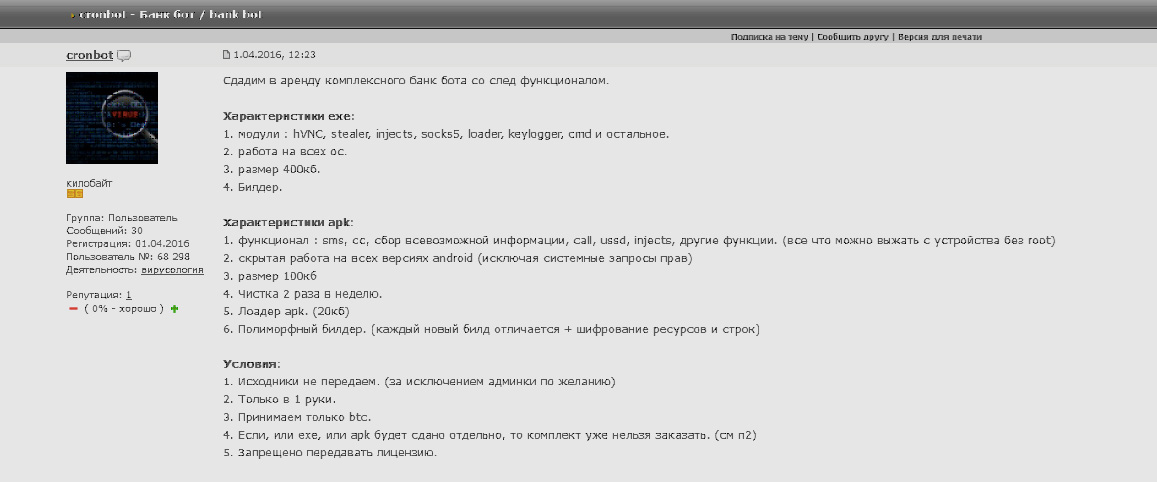
The group used the nickname Cronbot and referenced their banking trojan as “Cron,” but by that point security firms detect the malware as Tiny.z. Images of the Tiny.z malware backend panel are below.
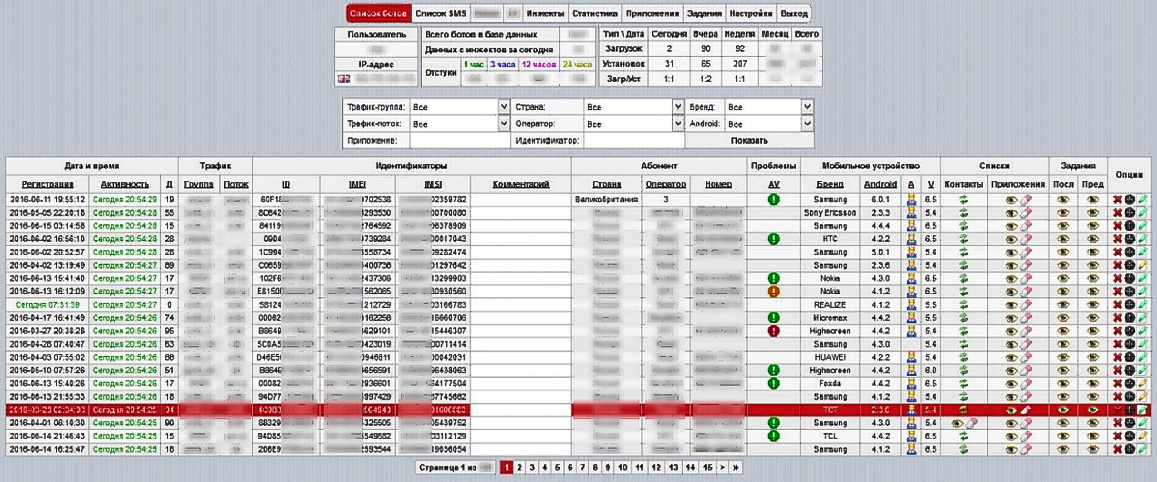 |
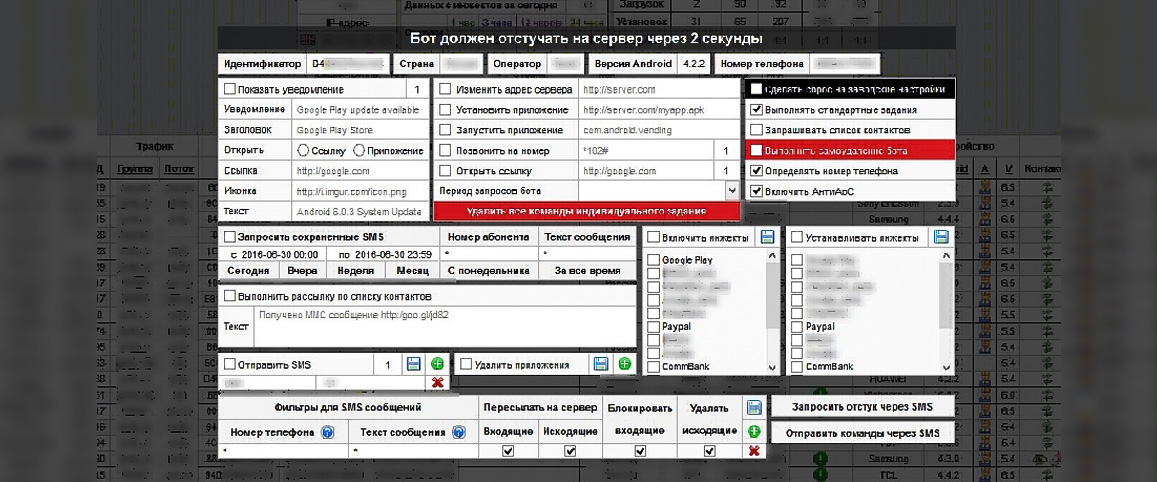 |
According to Group-IB, the ad’s purpose was to find one collaborator to expand their original team, which already featured various individuals in roles of money mules, cryptors, traffickers, and other.
According to the ad, this person would have gained access to the Tiny.z backend panel and helped the group spread the malware to new victims.
After this initial expansion, the Cron gang decided to go fully public and posted another ad in June 2016, where they opened the Tiny.z backend to any potential customer for $2,000 per month.
By that point, Tiny.z had expanded from targeting just Russian banks and included support for attacks on banks in the US, the UK, Germany, France, Turkey, Singapore, Australia, and other countries.
Cron group was behind Ponyforx malware
In September 2016, French security researcher Kaffeine spotted another ad from the Cron gang, this time for the Ponyforx malware, an infostealer trojan targeting the Windows platform, and based on the more popular Pony malware.
In their ad, the group referred to this infostealer as “Fox stealer v1.0”. Ponyforx is how security researchers tracked the malware before the ad’s appearance.
However, the group didn’t have time to proliferate this new tool because by November 2016, Russian police, with support from Group-IB, had already tracked down group members and started making arrests.
In total, 16 members, including the Cron group leader, were detained in the Russian provinces of Ivanovo, Moscow, Rostov, Chelyabinsk, Yaroslavl, and Republic of Mari El. The last arrest took place in April when police arrested a man in Sankt Petersburg.
Cron group made $900,000 just in Russia alone
In a press release, the Russian Ministry of Internal Affairs said the group made over 50 million rubles ($0.9 million) from operating the Tiny.z Android banking trojan in Russia alone. The group’s profit is most likely larger if we take into account the other countries they targeted.
Group-IB says crooks infected over one million Android devices in Russia alone, were making over 3,500 new victims per day and used over 6,000 bank accounts to launder their proceedings.
The video below contains footage from the 20 raids conducted by Russian authorities.
Source:https://www.bleepingcomputer.com/news/security/russian-police-apprehend-cron-gang-behind-tiny-z-and-ponyforx-malware/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











