Comparisons to the Windows flaw WCry exploited are exaggerated, but only a little.
Maintainers of the Samba networking utility just patched a critical code-execution vulnerability that could pose a severe threat to users until the fix is widely installed.
The seven-year-old flaw, indexed as CVE-2017-7494, can be reliably exploited with just one line of code to execute malicious code, as long as a few conditions are met. Those requirements include vulnerable computers that (a) make file- and printer-sharing port 445 reachable on the Internet, (b) configure shared files to have write privileges, and (c) use known or guessable server paths for those files. When those conditions are satisfied, remote attackers can upload any code of their choosing and cause the server to execute it, possibly with unfettered root privileges depending on the vulnerable platform.
“All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it,” Samba maintainers wrote in an advisory published Wednesday. They urged anyone using a vulnerable version to install a patch as soon as possible.
Not WCry, but close enough
The vulnerability description led researchers to speculate exploits could be “wormable,” meaning they could self-replicate from vulnerable machine to vulnerable machine quickly and without requiring end users to do anything to trigger the spread. Samba was introduced in 1991 as an easier way for servers running Unix-derived operating systems to share files, printers and other resources. Samba eventually provided the means for Unix and Linux machines to interoperate with variety of Windows networking features, including Active Directory and Windows Server Domain. Samba 3.5.0, the version the introduced the flaw, was released in March 2010.
The vulnerability almost immediately drew comparisons to the Windows flaw that the WCry ransomware worm exploited earlier this month to infect more than 200,000 computers in 150 countries. That flaw, too, was more than five years old, resided in a widely used implementation of the server message block protocol for printer- and file-sharing, and allowed for highly reliable code-execution exploits that required no interaction on the part of end users.
When the Windows vulnerability was first disclosed in April, many security experts assumed it would be hard to exploit because few computers would expose file- and print-sharing capabilities on the Internet. The rapid spread of WCry quickly dashed those assumptions. Dan Tentler, founder of security firm Phobus Group, told Ars that more than 477,000 Samba-enabled computers exposed port 445, although it wasn’t clear how many of them were running a vulnerable version of the utility. Tentler cited figures returned by the Shodan computer search engine. Researchers with security firm Rapid7, meanwhile, said they detected 110,000 devices exposed on the internet that appeared to run vulnerable versions of Samba. 92,500 of them appeared to run unsupported versions of Samba for which no patch was available.
There are also some clear differences between the Windows and Samba vulnerabilities. Unlike Windows, which has SMB on and open by default, those capabilities must be manually turned on in virtually all Linux distributions. Another key difference is the absence of any equivalent to “DoublePulsar,” the advanced weaponized backdoor developed by the National Security Agency and leaked by a mysterious group calling itself the Shadow Brokers. DoublePulsar made it easy for WCry to capitalize on the Windows flaw.
Still, risks exist, and there are other potential attack scenarios that wouldn’t require sharing to be exposed on the Internet. A malicious spam message that successfully compromised a single computer on a corporate network, for instance, could use the Samba flaw to spread virally to other computers. Given the ease of exploiting the vulnerability, it could quickly infect large numbers of machines. Researchers said the vulnerability could also open home networks with network attached storage devices to attacks as well.
HD Moore, who is vice president of research and development at Atredis Partners, said he expected the exploit to be available in the next 24 hours for the Metasploit framework used by security professionals and hackers. He posted the following images showing successful exploits against Samba on a computer running Ubuntu and NAS device made by Synology.
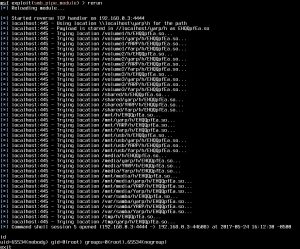
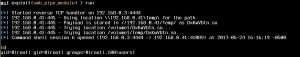
People who use Samba should check with their operating system or device provider to see if a fix is available. Those who are unable to patch immediately can work around the vulnerability by adding the line
nt pipe support = no
to their Samba configuration file and restart the network’s SMB daemon. The change will prevent clients from fully accessing some network computers and may disable some expected functions for connected Windows machines.
Given the ease and reliability of exploits, this hole is worth plugging as soon as possible. It’s likely only a matter of time until attackers begin actively targeting it.
Source:https://arstechnica.com/security/2017/05/a-wormable-code-execution-bug-has-lurked-in-samba-for-7-years-patch-now/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











