Summer vacation is over! During the past week, security researchers have discovered several distribution campaigns pushing the Locky ransomware via different methods, including a new variant that features one hell of a clever trick.
Spotted by Malwarebytes researcher Marcelo Rivero, this distribution campaign comes from the Locky group that uses the affiliate ID #5.
On-close Word macro campaign
According to Rivero, during the past week, Locky affiliate #5 has pushed a malicious spam wave spreading Word documents laced with macro scripts.
If this were it, this would have been nothing new, as this is the most prevalent malware distribution trick out there. By clever messages embedded in the Word document, users are enticed to enable macros inside the Word file to support newer features and/or to show new content.
Usually, enabling macros triggers a malicious script embedded in the document, which eventually installs malware. This week, Rivero spotted a Word document that behaved differently and didn’t execute the malicious script until the user closed the file.
While this doesn’t make a difference for victims, since they are in trouble from the moment they enabled macros inside Word, this small trick makes a huge difference when it comes to security scanners.
“For analysis purposes, many sandboxes lower the security settings of various applications and enable macros by default, which allows for the automated capture of the malicious payload,” Rivero explains the difference. “We ascertain that in their current form, the malicious documents are likely to exhibit a harmless behavior in many sandboxes while still infecting end users that would logically close the file when they realize there is nothing to be seen.”
Fake Dropbox account verification campaign
Another campaign, this time perpetrated by the Locky affiliate #3, used emails posing as Dropbox account verification requests.
The campaign was spotted by My Online Security, ISC SANS, and CSIS and bombarded users all last week.
This campaign delivered the latest Locky ransomware version, the one that uses the .lukitus extension.

HoeflerText popups targeting Chrome and Firefox users
Another Locky campaign from the same affiliate ID #3 group — the most active of all Locky campaigns — also used the now classic HoeflerText popups technique.
This campaign relied on malvertising and exploit kits to redirect traffic to malicious pages that showed a “HoeflerText font missing” message, enticing users to download and install the font (downloaded as a JS script file), in order to view the page’s content.
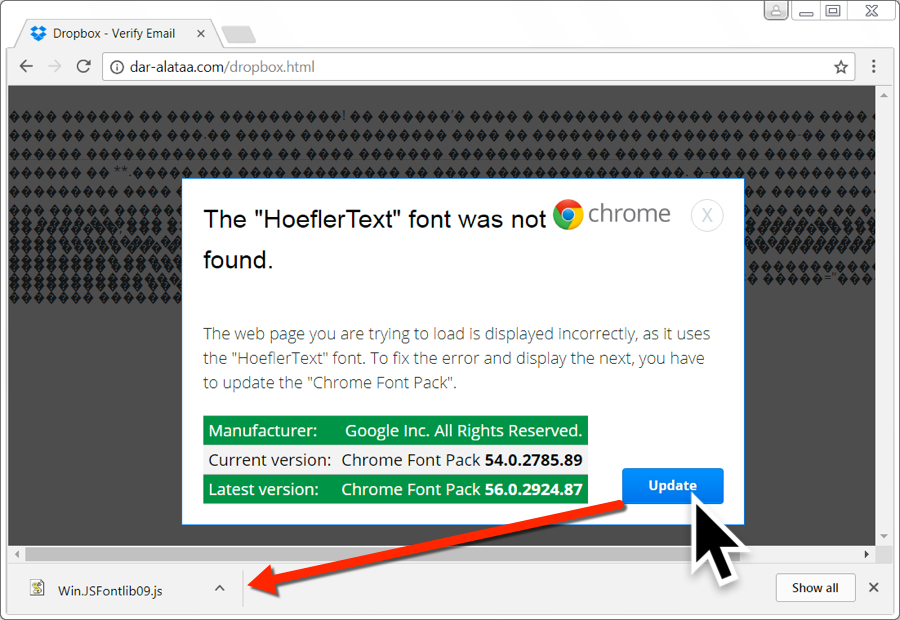
The popups appeared to users of Firefox and Chromium-based browsers only. This campaign became active yesterday, August 31, and is still ongoing, so users need to pay close attention to all Dropbox emails they receive in the upcoming days.
Boring spam campaigns
Prior to the HoeflerText popup campaign, the same affiliate ID pushed your run-of-the-mill spam emails all this past week.
These were classic spam campaigns using email subject lines that posed as scanned photos, documents, invoices, orders, and others. The file attachments with these emails were ZIP files containing a VBS script that installed Locky when users double-clicked it.
The campaigns were documented in blog posts by AppRiver, Comodo, and Barracuda.
Despite the huge push to make Locky relevant once more, statistics obtained by Bleeping Computer show a minimum spike in new Locky infections compared to the previous week.
Source:https://www.bleepingcomputer.com/news/security/boobytrapped-word-file-installs-locky-ransomware-when-you-close-the-document/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











