A dissatisfied customer has breached the server of TrueStresser, a DDoS-for-hire service, pilfered its database, and leaked some of the content online.
While we don’t know when the actual hack took place, two files were uploaded on the Hastebin and Pastebin text sharing services last nights, each containing different parts of the stolen TrueStresser data.
Data leaked after a customer support dispute
A first paragraph atop the Pastebin file explains the attacker’s motives, revealing the hack took place after one of the TrueStresser admins banned the hacker’s account. We quote:
Besides the short explainer, the Pastebin file also contained:
› Details for 331 user accounts [username, hashed password, email]
› Cleartext passwords for 16 accounts
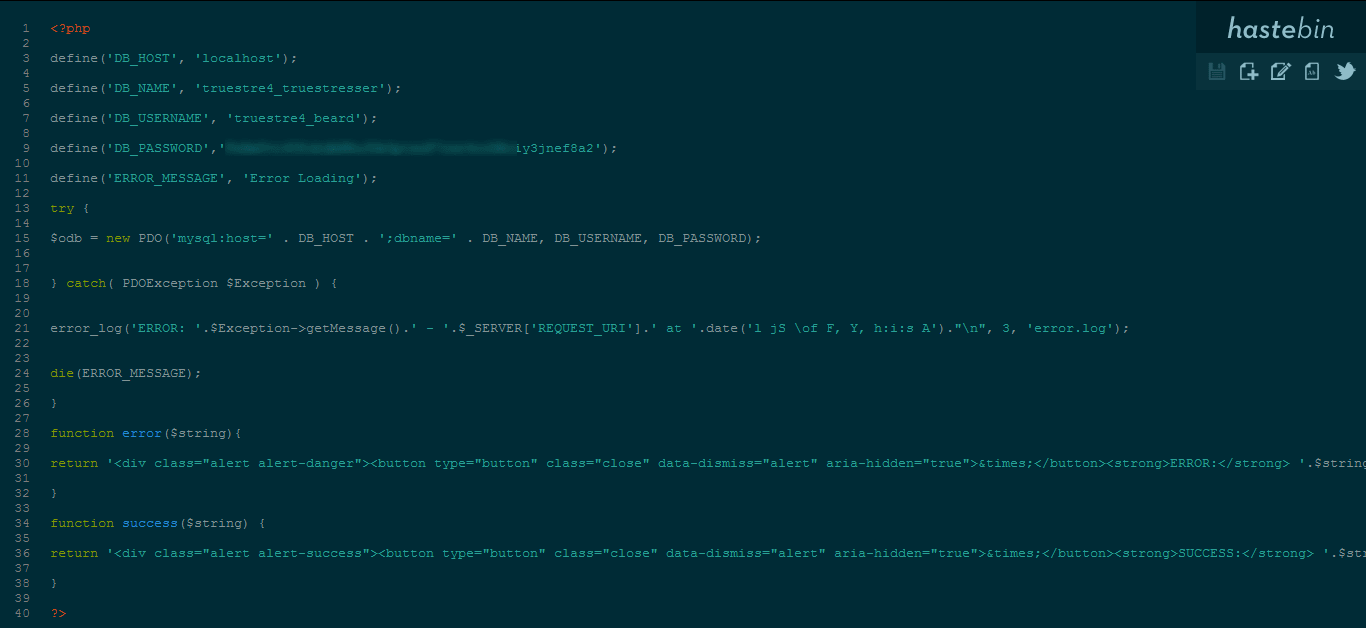
› A link to the Hastebin file, which the leaker claimed to be TrueStresser’s config.php file.
The Hastebin file, in turn, contained database credentials for TrueStresser’s control panel, the interface customers use to issue commands to a DDoS botnet and start attacks.
TrueStresser aware of the leak
The breach came to light when security researcher Derrick Farmer discovered the file on Pastebin’s list of recent uploads.
Farmer told Bleeping Computer in a private conversation that he verified the leak’s authenticity by logging in using one of the leaked cleartext credentials.
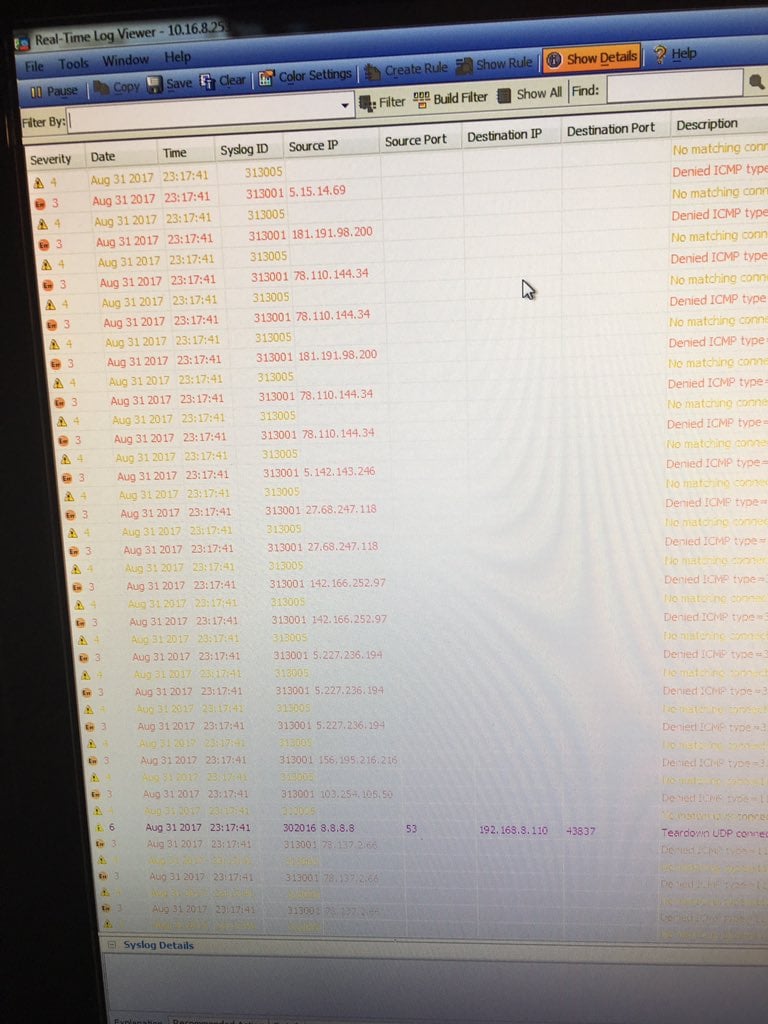
The researcher said that shortly after his test, the IP he used to log into one of the leaked accounts was bombarded by an ICMP flood.
“I suspect they were aware of the leak and were watching for logins of those accounts,” Farmer told Bleeping.
The researcher provided your reporter a short video of the attack, along with the screenshot below, showing the ICMP flood in progress.
TrueStresser is a Defcon.pro customer
Looking closer at dumped API calls, we can see that TrueStresser is actually renting infrastructure from another DDoS booter service called Defcon.pro.
The leaked API calls are in the same format as the Defcon API documentation, accessible in the Defcon.pro control panel.
https://api.defconpro.io/api.php?ip=[host]&port=[port]&time=[time]&method=[method]&key=MrBeard422+Jayden2311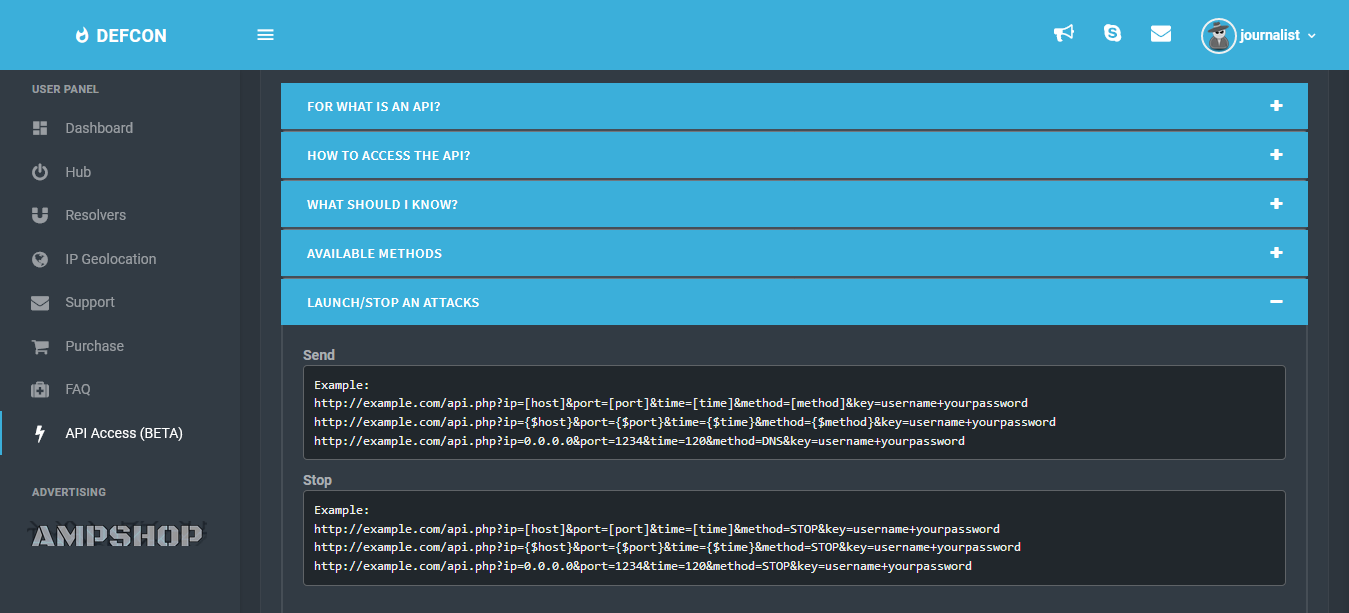
The entire situation is eerily similar to the PoodleStresser-vDos chain of events. In August 2016, an unknown party breached and leaked the PoodleStresser database, which was later tied to another DDoS-for-hire service named vDos, the larger provider of DDoSing infrastructure at the time.
On its website, Defcon.pro claims to serve over 7,700 customers. A counter showed that customers used the service to launch over 3,900 attacks today, September 1, at the time of writing, and over 117,000 DDoS attacks in total.
In the API documentation, Defcon.pro operators claim to be able to launch the following types of DDoS attacks:
NORMAL:
------------------
DNS
DNS-Sec
NTP
SNMP
OVH
STORM
NINJA-off
SOURCE
REK
PROLAND
PiSoland
XSYN
XACK
XMAS
PREMIUM:
------------------
TS3-Droper
TS3-Fuck
CLDAP
WOLF
ABUSE
GRENADE
GK_Steam
GK_Samp
GK_MTA
GK_Minecraft
GK_Cod
GK_BF
GK_CS
GK_Quake
GK_Vicesity
GK_TF
GK_MoH
TCP-AMP
TCP-SACKThe Defcon.pro website also lists the following features:
Private Methods
Skype Resolver
99% UPTIME
Dedicated Servers
Paypal/Bitcoin
Stop Button
IP Geolocation
Cloudfare resolver
Domain resolver
Amazing Power
Easy to use interface
Neither TrueStresser staff nor Defcon.pro admins responded to a request for comment.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











