A password stealing Trojan called AdService is being quietly distributed by adware bundles that typically install other programs such as Russian adware, extensions, clickers, adware, and fake system optimization programs.
AdService uses Chrome DLL hijacking to load itself when Chrome is executed so that it can steal information from Facebook and Twitter accounts.
AdService Executes via Chrome DLL Hijacking
To give a little background info about DLL Hijacking, when a program is executed and needs to load a particular DLL the program can either load it from a specific location or can just specify the DLL it wishes to load and let Windows find it for them. In the latter scenario, when Windows tries to find the DLL it uses a search path to find the DLL and the first location it looks is in the folder that the executable is located. If requested DLL is found, it will automatically load that DLL into the program.
Malware can take advantage of this by placing malicious DLLs in a program’s folder that contain the same name of a DLL that the program would normally load from another folder. This causes the program to execute the malicious DLL instead of the legitimate one that it was expecting.
In this case, the AdService Trojan is placing a malicious version of the winhttp.dll in the C:\Program Files (x86)\Google\Chrome\Application folder. When a victim starts Chrome, chrome.exe will load the malicious version of winhttp.dll executed instead of the one in C:\Windows\system32.
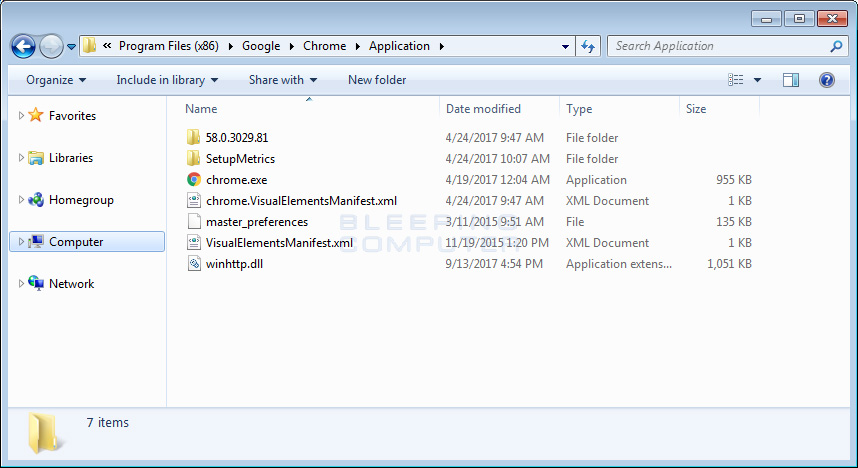
When Chrome starts, and the malicious winhttp.dll is loaded, the Trojan will connect to a remote site and send and receive information. It will then connect to Facebook and try to steal information from the user’s profile.
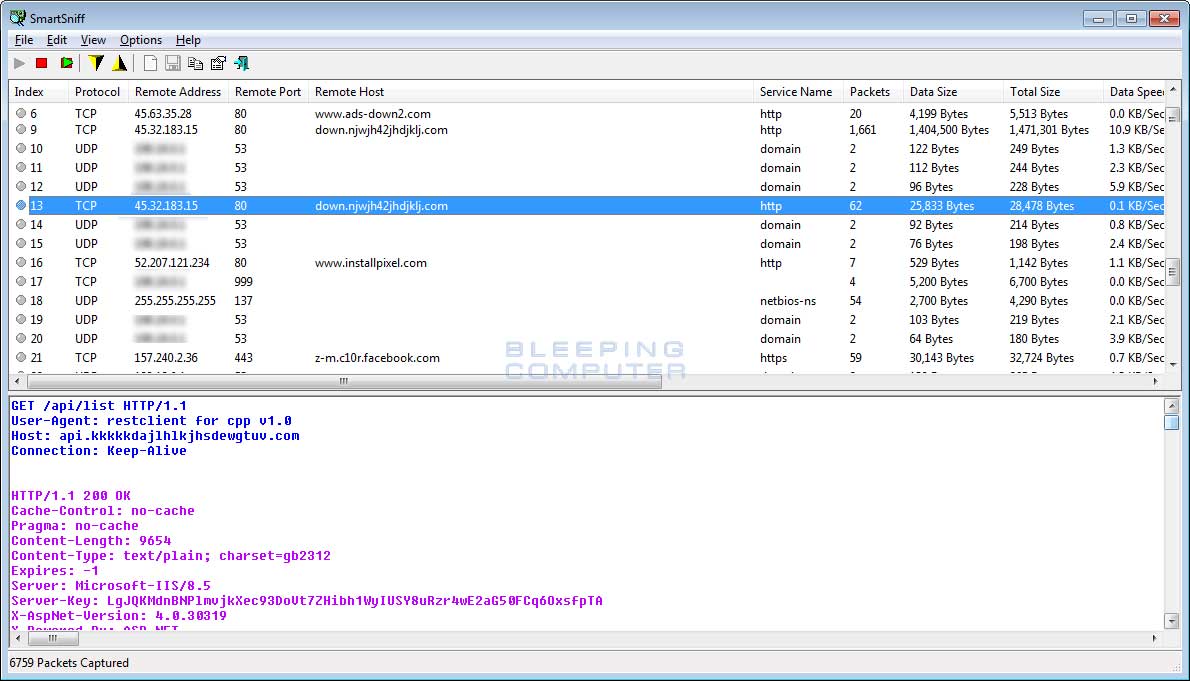
When connect to Facebook and Twitter, it will open the pages that include https://www.facebook.com/settings, https://www.facebook.com/bookmarks/pages, https://secure.facebook.com/payments/settings/payment_methods/?__a=1, https://www.facebook.com/profile.php, https://mobile.twitter.com/account, and https://twitter.com/settings/account.
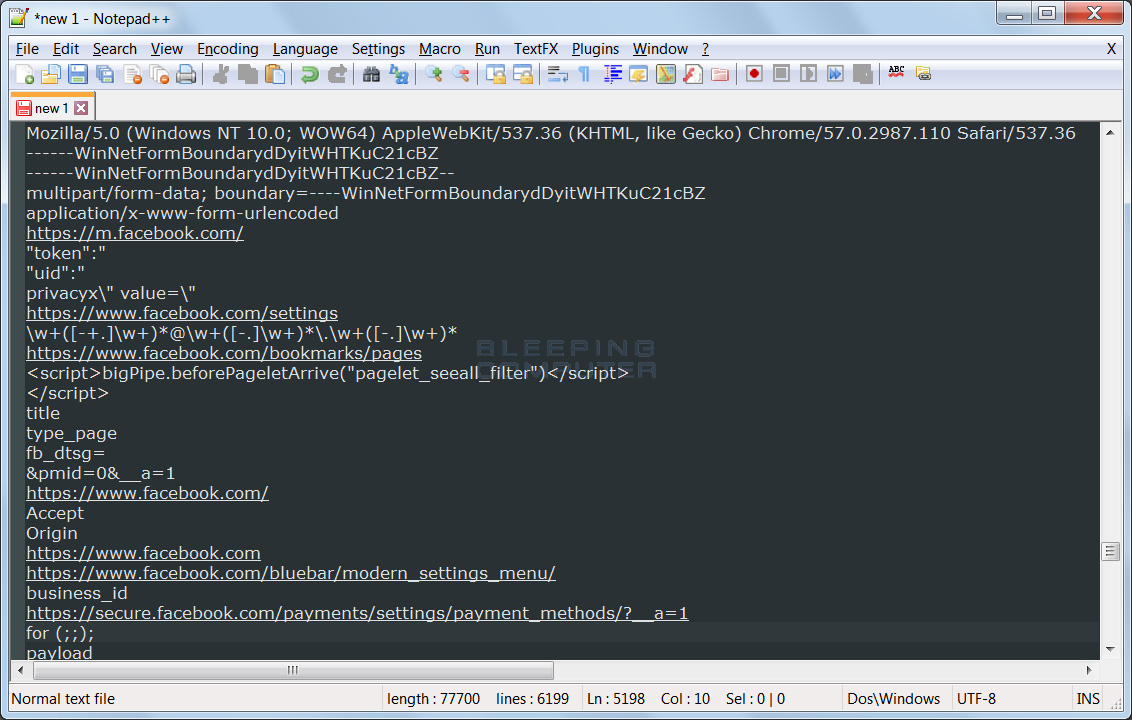
Each of these pages contain various information that could potentially be valuable for those with malicious intent. This includes a list of friends, a victim’s settings, their email address and phone number, what Facebook pages you are following, and information about any stored Facebook credit card details.This includes type of card, last 4 digits, expiration, and the billing zip code.
As you can see this information is not something you want those of ill-intent to have access. Thankfully, this service is detected by 45out of 64 security vendors on VirusTotal, even though the majority of them are not properly classifying the infection as a password stealer.
Adware bundles are getting out of hand
I have been railing against adware and download installer monetization companies that continuously cross the line too often without fear of reprisal. This is because people only think about the nuisance of popups and advertisements when it comes to adware, but in reality adware installers also install a variety of other unwanted and downright malicious programs.
These include password stealers, miners, tech support scams, ad clickers, browser hijackers, web browsing tracking, rootkits, and more. Over the past two years, we have seen some really nasty infections that include a major homepage hijacker called Fireball that affected millions of computers, extensions being hijacked to display ads, services being installed that block security programs from running, 1.65 million computers infected with miners, and much more.
As you can see, Adware and PUPs (potentially unwanted programs) are no longer just about being an annoyance to users and have easily crossed over into full-fledged computer infection territory. Law enforcement needs to actually start threatening jail time for these offenses & security companies and InfoSec researchers need to start taking adware and PUPs more seriously as their mischievous facades in many cases are hiding something far darker.
IOCs
Hashes:
adware bundle - 41474cd23ff0a861625ec1304f882891826829ed26ed1662aae2e7ebbe3605f2
svchost.exe (installer) - a7a42bdb5f390e21107aedce73904ade8385a6e550149f8358f89515f30db336
winhttp.dll - c44298540b45cd35d641fea76c7512f8e859967f9ef9a3c5df42477e8b6c7bdaNetwork Communication
api.kkkkkdajlhlkjhsdewgtuv.com/
www.installpixel.com
www.ads-down2.com
down.njwjh42jhdjklj.comAdService Associated Files
C:\Program Files (x86)\Google\Chrome\Application\winhttp.dll
%UserProfile%\AppData\Local\AdService\
%UserProfile%\AppData\Local\AdService\AdService.dll
%UserProfile%\Downloads\svchost.exe
AdService Associated Registry Keys
HKCU\Software\CrcXcInsatall
HKCU\Software\CrcXcInsatall\Install xxoo
HKCU\Software\SetupCompany
HKCU\Software\SetupCompany\Name SetupCompany
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Svchost\AdsServiceGroup AdsService
HKLM\SYSTEM\CurrentControlSet\services\AdsService
HKLM\SYSTEM\CurrentControlSet\services\AdsService\Type 32
HKLM\SYSTEM\CurrentControlSet\services\AdsService\Start 2
HKLM\SYSTEM\CurrentControlSet\services\AdsService\ErrorControl 1
HKLM\SYSTEM\CurrentControlSet\services\AdsService\ImagePath %SystemRoot%\System32\svchost.exe -k AdsServiceGroup
HKLM\SYSTEM\CurrentControlSet\services\AdsService\DisplayName AdsService
HKLM\SYSTEM\CurrentControlSet\services\AdsService\WOW64 1
HKLM\SYSTEM\CurrentControlSet\services\AdsService\ObjectName LocalSystem
HKLM\SYSTEM\CurrentControlSet\services\AdsService\Description AdsService
HKLM\SYSTEM\CurrentControlSet\services\AdsService\Parameters
HKLM\SYSTEM\CurrentControlSet\services\AdsService\Parameters\ServiceDll %UserProfile%\AppData\Local\AdService\AdService.dllSource:https://www.bleepingcomputer.com/news/security/adware-installs-infostealer-trojan-that-it-loads-via-chrome-dll-hijacking/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











