This attack chain exposed millions of potential victims in the US, Canada, the UK, and Australia, leveraging slight variations on a fake browser update scheme that worked on all three major Windows web browsers. The attack has been active for more than a year and is ongoing elsewhere, but this particular infection pathway was shut down when the site operator and ad network were notified of the activity.
Background
Despite dramatic declines in exploit kit activity over the last year, malvertising remains a profitable enterprise for actors who can achieve sufficient scale and deliver malware effectively in a landscape where vulnerable machines are increasingly scarce. To improve infection rates and better evade detection by vendors and researchers, threat actors have turned to advanced filtering techniques and social engineering instead of the widespread use of exploits.
Few groups are able to infiltrate the advertising chain on the most visited websites. We have recently looked at several of these groups including SadClowns [1], GooNky [2], VirtualDonna [3] and AdGholas [4]. While we have discussed Kovter in the past [14], we have not had the opportunity to look in depth at an operation by KovCoreG (aka MaxTDS per FoxIT InTELL). This post looks at a recent KovCoreG campaign and describes what we know of the current state of their very active social engineering scheme [5-11].
The Infection Chain
The infection chain in this campaign appeared on PornHub (Alexa US Rank 21 and world rank 38 as of this writing) and abused the Traffic Junky advertising network. It should be noted that both PornHub and Traffic Junky acted swiftly to remediate this threat upon notification.
We studied three cases of the chain on Windows: Chrome, Firefox, and Microsoft Edge/Internet Explorer(Figure 1). We will detail the Chrome variation but all three cases operate in a similar fashion.
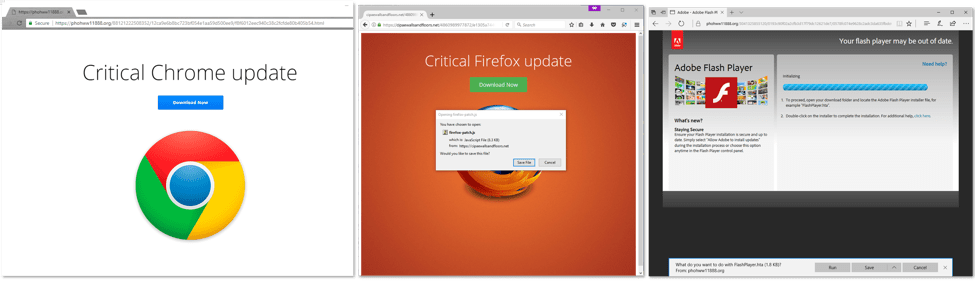
Figure 1: The three KovCoreG social engineering templates we observed
Figure 2 shows the full KovCoreG infection chain from PornHub through the Kovter callback to its command and control (C&C).
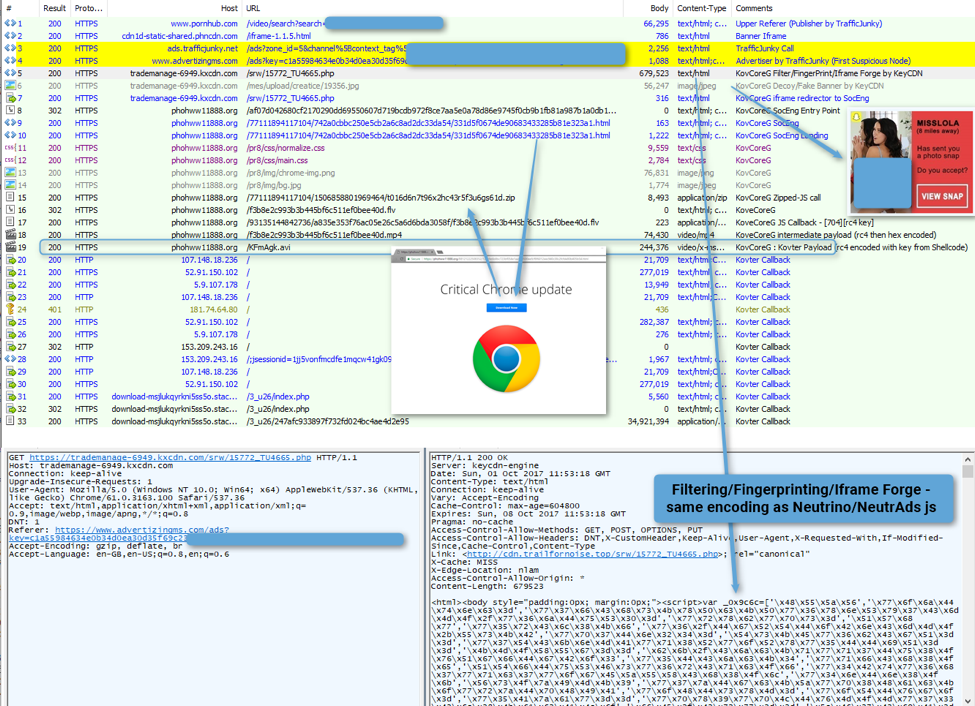
Figure 2: October 1, 2017 – Full KovCoreG infection chain
The chain begins with a malicious redirect hosted on avertizingms[.]com, which inserts a call hosted behind KeyCDN, a major content delivery network.
It appears that malvertising impressions are restricted by both geographical and ISP filtering. For users that pass these filters, the chain delivers a page containing heavily obfuscated JavaScript identical to that used by Neutrino and NeutrAds[15]. Note, however, that we do not believe there is a strong connection between the two groups other than code sharing or a common coder with a new customer/partner.
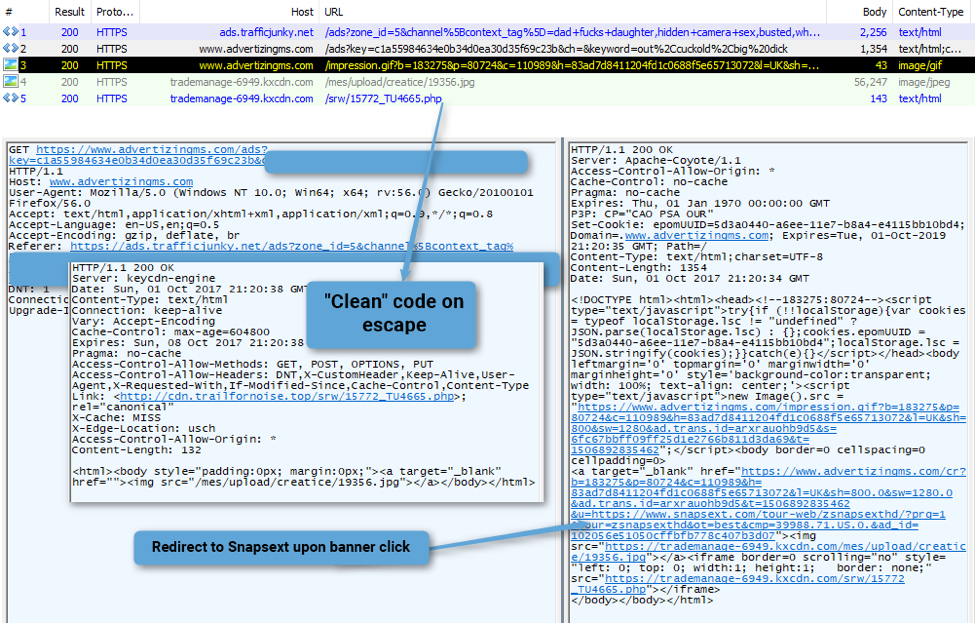
Figure 3: KovCoreG sending decoy call when evading unwanted visitors or systems
Analysis of this first step is ongoing, but it contains several components including filtering and fingerprinting of the timezone, screen dimension, language (user/browser) history length of the current browser windows, and unique id creation via Mumour [12].
Figures 4-6 show the fake update screens that appear once a user opens the file downloaded during the infection chain. The files are different depending on the browser in use.
Figure 4: Chrome browser template – KovCoreG fake “Critical Chrome update” drops a zipped runme.js file after a user clicks
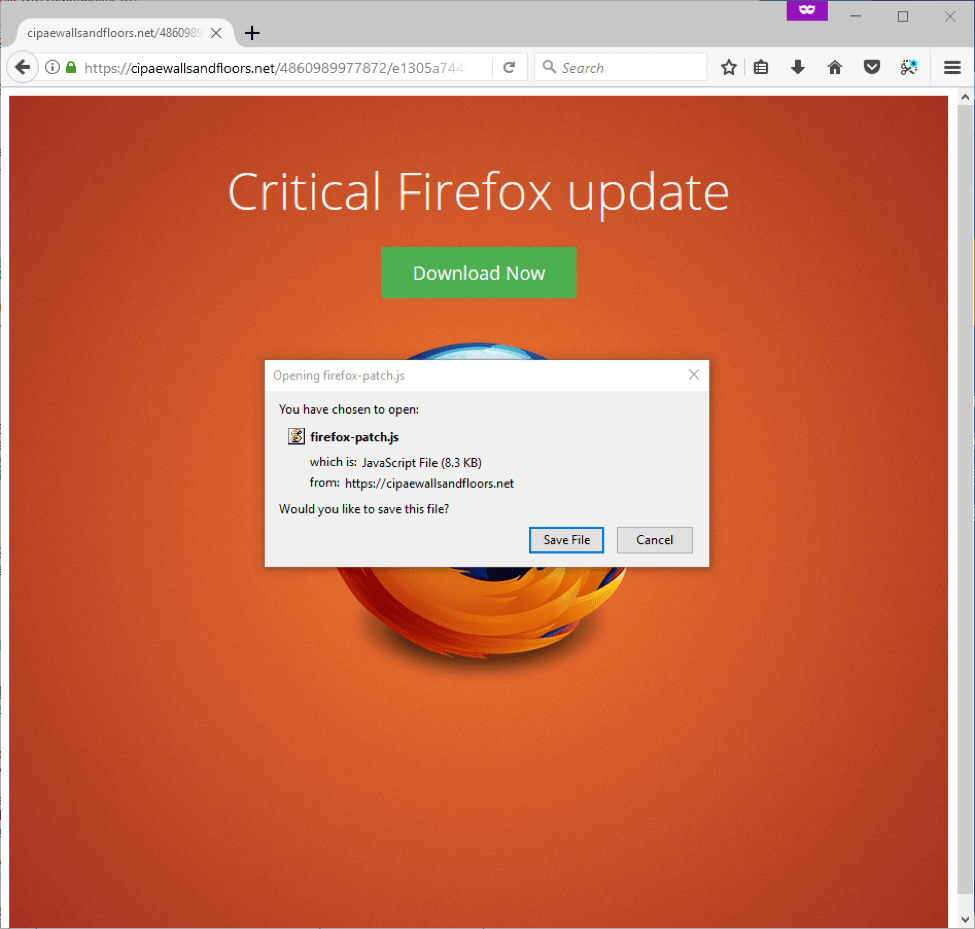
Figure 5: Firefox browser template – KovCoreG fake “Critical Firefox update” drops a firefox-patch.js file after a click
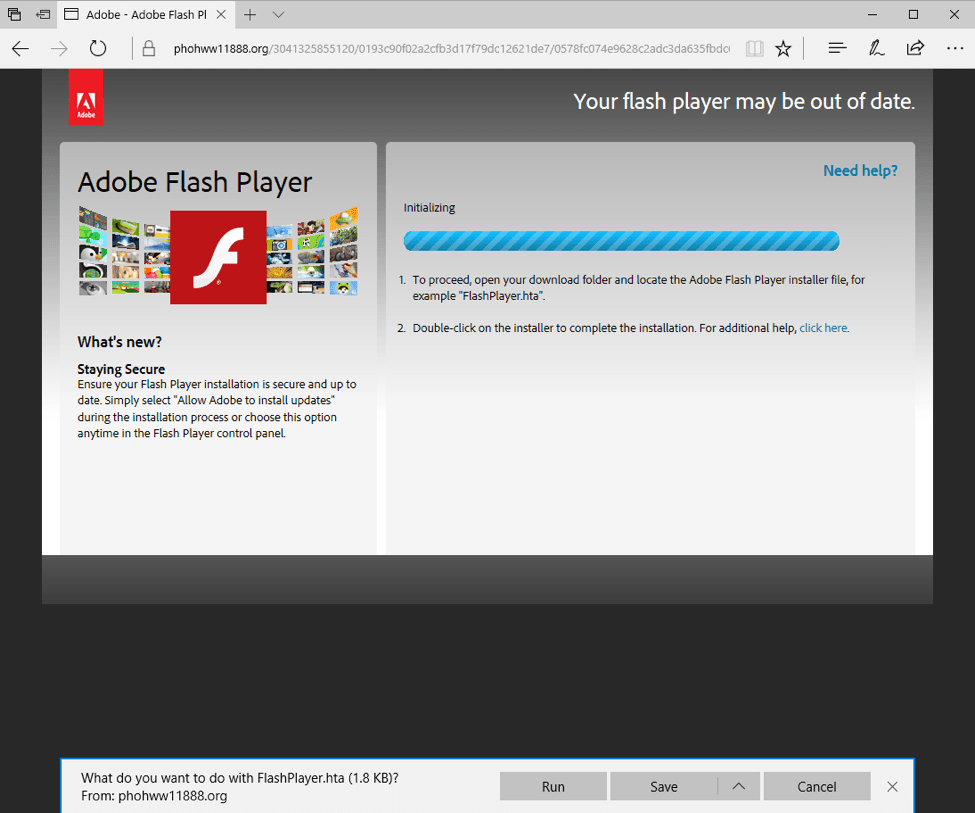
Figure 6: Microsoft Edge/Internet Explorer browser template – KovCoreG fake Adobe Flash Player update (“Your flash player may be out of date”) drops a FlashPlayer.hta file after a click
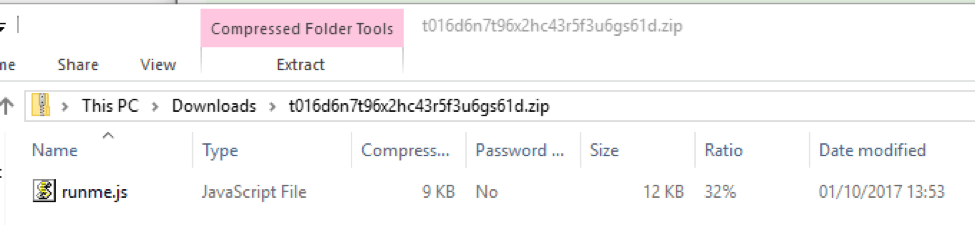
Figure 7: Chrome fake update zipped runme.js; the victim must explicitly open this file since this chain does not rely on exploits
The runme.js file associated with the fake Chrome update beacons back to the same server hosting the social engineering scheme. This adds an extra layer of protection against replay or study. Analysts will not be able to reach the next step in the chain if their IP has not “checked in” first to the malvertising host. This makes it extremely unlikely that the JavaScript can be run alone and provide the payload in a sandbox environment. This is most likely why this component of the chain has not been documented previously.
The JavaScript then downloads the “flv” and the “mp4” files. The flv file contains “[704][rc4 key]”. The mp4 file is an intermediate payload, encrypted with the rc4 key from the flv file and then hex-encoded. “704” here is likely the internal campaign ID.
The intermediate payload is itself more JavaScript, including an encoded Powershell script that embeds shellcode.This shellcode downloads and launches an “avi” file which is actually the Kovter payload, RC4-encoded with, in that particular pass, the key “hxXRKLVPuRrkRwuaPa” stored in the shellcode.
Kovter is known for, among other things, its unique persistence mechanism. Figures 8-10 show a Registry entry, .bat file shortcut, and the .bat file itself, respectively, that are artifacts of this mechanism, previously described by Microsoft [13].
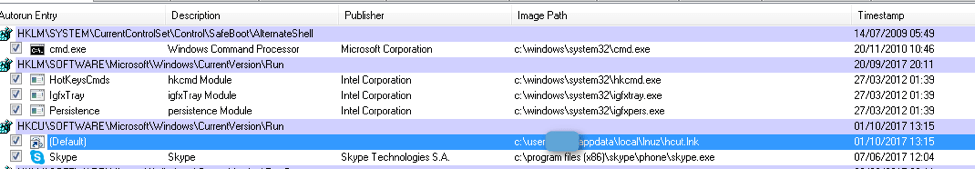
Figure 8: Kovter persistence mechanism artifact (Registry Entry)
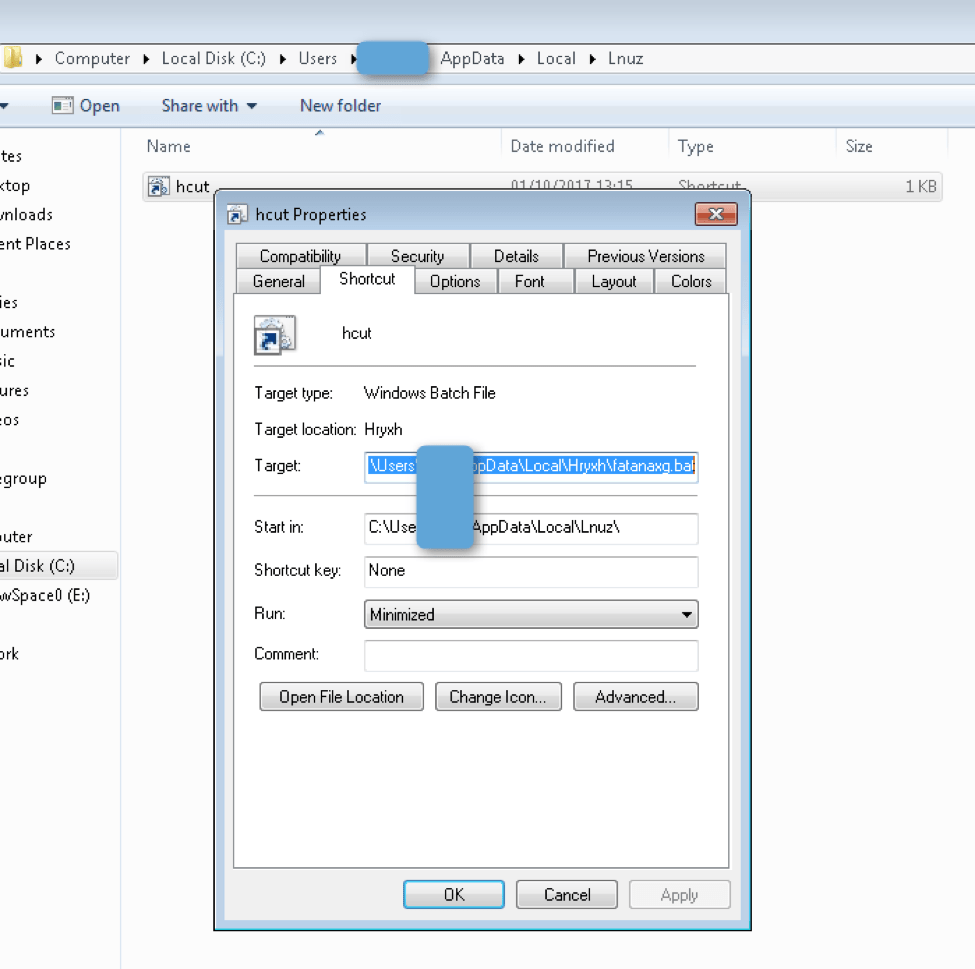
Figure 9: Kovter persistence mechanism artifact (Shortcut to .bat file)
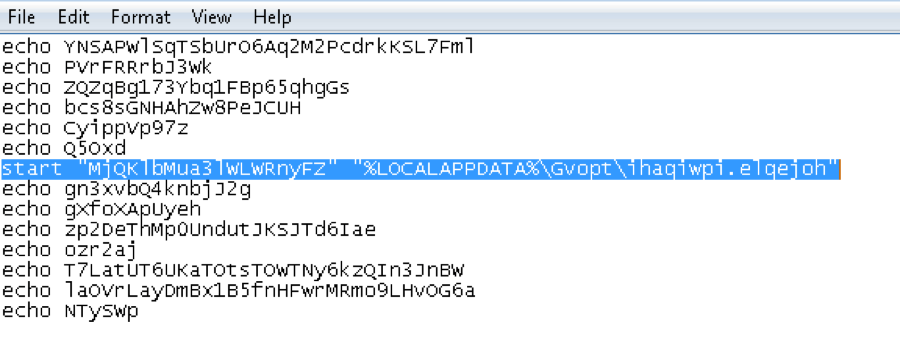
Figure 10: Kovter persistence mechanism artifact (bat file)
Conclusion
The combination of large malvertising campaigns on very high-ranking websites with sophisticated social engineering schemes that convince users to infect themselves means that potential exposure to malware is quite high, reaching millions of web surfers. Once again, we see actors exploiting the human factor even as they adapt tools and approaches to a landscape in which traditional exploit kit attacks are less effective. While the payload in this case is ad fraud malware, it could just as easily have been ransomware, an information stealer, or any other malware. Regardless, threat actors are following the money and looking to more effective combinations of social engineering, targeting, and pre-filtering to infect new victims at scale.
Source:https://www.proofpoint.com/us/threat-insight/post/kovter-group-malvertising-campaign-exposes-millions-potential-ad-fraud-malware

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











