The Android spyware was used to steal personal data of victims – The campaign also shows why users should never use their real photos on Facebook.
There are almost 2 billion monthly active users on the social media giant Facebook and that makes it one of the most lucrative targets for hackers and cybercriminals. Recently, the researchers at Czech IT security researchers at Avast reported a sophisticated campaign in which attackers used Facebook and Facebook messenger to trick users into installing a highly sophisticated Android spyware.
Hackers Used Fake Facebook Profiles Of Attractive Females
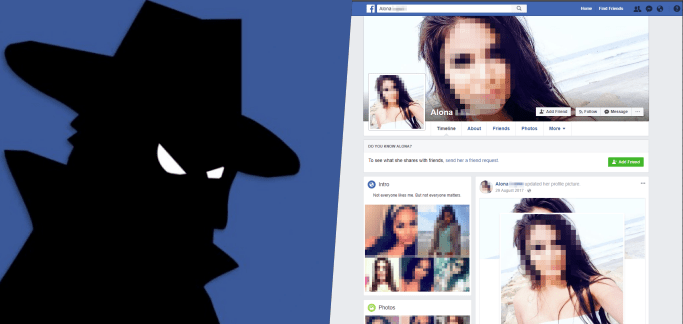
The scam was reported to Avast by one of their customers informing about receiving messages on their Facebook messenger carrying strange looking links sent by unknown profiles going by the names of Alona, Christina, and Rita using images of attractive women.
Upon analyzing the scam, researchers quickly identified that the profiles used in the scam were fake, stolen images from real people and used without their knowledge or consent. The women lured the victim to click on the link and install the latest version of Kik Messenger app on their device in order to continue their “flirty conversations”.

However, the link only disguised as the Kik Messenger app, in reality, it would take victims to a “very convincing” phishing website and which hosted the malicious version of Kik Messenger app. Once installed, the spyware app would steal personal data from the device.
Tempting Cedar Spyware & Lebanese Connection
Dubbed Tempting Cedar Spyware by Avast researchers, the attack aims at stealing personal data from victims Android devices including photos, contacts list, SMS, call logs, victims’ location and recording surrounding sounds including call conversations.
According to Avast, the operation has been targeting Android users since 2015 and so far it has hunted hundreds of victims in the Middle East. The most targeted victims were from Israel while a small number of victims were identified in China, France, Germany and the United States.
Based on the evidence such as login activity, IP addresses, Middle Eastern time zones, registrant data of domains used by hackers to distribute malware, Avast researchers believe that this campaign is being run from Lebonan. However, at the time of publishing this article, it was unclear if the Tempting Cedar Spyware campaign is still targeting users or it has been shut down.
“The cybercriminals behind the Tempting Cedar Spyware were able to install a persistent piece of spyware by exploiting social media, like Facebook, and people’s lack of security awareness, and were thus able to gather sensitive and private data from their victims’ phones including real-time location data which makes the malware exceptionally dangerous, concluded Avast.”
Just last month researchers at Lookout Security exposed a cyber espionage campaign called Dark Caracal in which attackers targeted thousands of victims across 21 countries. The researchers identified that the campaign is being run from Beirut, Lebanon from a building owned by the Lebanese General Directorate of General Security (GDGS).
Photos Used By Fake Profiles On Facebook
Avast has shared a few blurred photos used by hackers in the operation which indicates that social media users on any site should refrain from using their real photos. On Facebook, users should avoid using their photos as cover or profile photos and make sure their personal photos are only visible to their close friends.

Hamas Once Targeted IDF With Seductive Female Images
This is not the first time when hackers have used photos of attractive women to trap their victims. In fact, this is not the first campaign in which Israeli users have been lured into installing spyware on their phone by hackers using fake photos of attractive women. In January 2017, Hamas was found hacking dozens of smartphones belonging to IDF (Israel Defense Forces) soldiers using tons of seductive female images on Facebook and tricking soldiers into downloading malware which stole their text messages photos, contacts, WhatsApp conversations and identified their location.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.