Panera didn’t fix flaw for 8 months; 37 million records were allegedly exposed. Eight months ago, Panera Bread was notified of a security flaw that was leaking customer information to anyone who knew where to look for it. But the company failed to fix the flaw until this week after the breach was made public in a report suggesting that it affected 37 million customer records.
Panera Bread said this week that the leak affected fewer than 10,000 consumers and that it has been fixed. But security reporter Brian Krebs and the security researcher who notified Panera of the breach last year disputed that account. They say that millions of customer records were available online and that they remained available at publicly accessible URLs after Panera said the flaw was fixed. Those URLs appear to have finally been scrubbed of the customer information, as they now produce error messages instead of customer data.
The records “could be indexed and crawled by automated tools with very little effort,” Krebs wrote yesterday. Leaked data included Panera customers’ loyalty card numbers, “which could potentially be abused by scammers to spend prepaid accounts or to otherwise siphon value from Panera customer-loyalty accounts,” he wrote.
Leaked data also included usernames, first and last names, email addresses, phone numbers, birthdays, the last four digits of credit card numbers, home addresses, social account integration information, and saved food preferences and dietary restrictions, according to security researcher Dylan Houlihan.
Before being taken down, the URLs showed customer data in this format:

According to Houlihan, the flaw “let anyone search by a variety of customer attributes, including phone number, email address, physical address, or loyalty account number.” In the example above, “the phone number was a main line at an office building where many different employees apparently registered to order food online.”
Panera ignored email, saying it looked like a scam
Houlihan notified Panera about the data leak on August 2, 2017, telling the company that its delivery website “exposes sensitive information belonging to every customer who has signed up for an account to order Panera Bread online.” Panera has more than 2,000 stores nationwide and annual sales of more than $5 billion.
Houlihan offered to send Panera more details on the flaw in an encrypted format if the company was willing to provide a PGP key. Houlihan also offered to send the information via unencrypted email or discuss it in a phone call.
In response, Panera Information Security Director Mike Gustavison accused Houlihan of trying to scam the company, according to screenshots of emails published by Houlihan in his blog post yesterday.
Here was Gustavison’s response: My team received your emails however it was very suspicious and appeared scam in nature therefore was ignored. If this is a sales tactic I would highly recommend a better approach as demanding a PGP key would not be a good way to start off. As a security professional you should be aware that any organization that has a security practice would never respond to a request like the one you sent. I am willing to discuss whatever vulnerabilities you believe you have found but I will not be duped, demanded for restitution/bounty, or listen to a sales pitch.
The email screenshots don’t show Houlihan trying to sell anything—he was privately notifying Panera of a flaw that leaked the data of many customers, including his own. As a security professional himself, Houlihan noted that he would not start a conversation about a potential security flaw “by being antagonistic.”
Gustavison eventually provided a PGP key and Houlihan sent the detailed information in an encrypted message. Houlihan sent several followup emails without getting a response but then received a reply from Gustavison on August 9 saying that the company was “working on a resolution.”
“[A]fter I was reassured this would be fixed, I checked on this vulnerability every month or so because my own data is in there, which means I’m personally affected by it,” Houlihan wrote. “So I personally know for a fact that it was never patched in the interim. And even if it was, that it would be fixed and inadvertently reintroduced is nearly as bad as not fixing it at all. But I held off on doing anything, deciding to let them proceed. Eight months go by.”
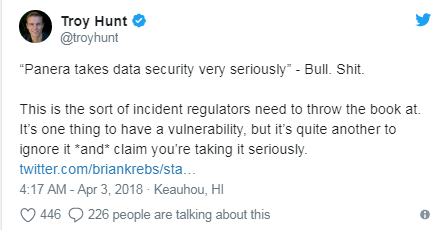
“Panera takes data security very seriously”
Frustrated by the lack of a fix, Houlihan finally reached out to Krebs and security expert Troy Hunt. An article published by Krebs yesterday spurred Panera to take action, at least on the public relations front.
“Panera takes data security very seriously, and this issue is resolved,” Panera Bread Chief Information Officer John Meister told Fox in this article yesterday.
Panera said there was no evidence of payment card information being leaked and that “[o]ur investigation to date indicates that fewer than 10,000 consumers have been potentially affected by this issue.”
Krebs disputed Panera’s attempt to downplay the story last night. In an update to his article, he wrote that Panera “basically ‘fixed’ the problem by requiring people to log in to a valid user account at panerabread.com in order to view the exposed customer records (as opposed to letting just anyone with the right link access the records).”
Krebs also tweeted links that, he said, showed the breach affected 37 million customer records.
The links provided by Krebs now result in error messages.
“I’m not aware of any of the flaws that I saw yesterday still existing on the site,” Krebs told Ars today.
Krebs said his own testing “seems to indicate the issues I raised are no longer issues.” But he added that “only Panera can really tell you if they’ve fixed it.”
Ars has emailed Panera’s public relations department and Gustavison, and we will update this story if we receive more information. Among other things, we asked Panera how it determined that fewer than 10,000 consumers were affected.
Houlihan was disappointed in Panera’s response to the security flaw and the company’s attempt to downplay the flaw’s severity in public statements.
“Until we start holding companies more accountable for their public statements with respect to security, we will continue to see statements belying a dismissive indifference with PR speak,” Houlihan wrote. “In the words of Troy Hunt, when Panera Bread says, ‘We take security seriously’, they mean, ‘We didn’t take it seriously enough.'”

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.